Technology
The Dark Side of Microsoft’s AI Partnership with China

Beauty Fitness
Transform Your Skin with Micro Needling in Tomball

Living in Tomball, we know just how much we cherish our sunny days and outdoor adventures. However, the Texas heat, humidity, and intense UV exposure can take a toll on our skin. Whether it’s persistent acne scars, sun spots, or the fine lines that seem to deepen every year, we all know how difficult it can be to maintain that youthful, glowing complexion.
At Enfield Royal Med Spa Tomball, we believe in a holistic approach to skincare — healing from within. That’s why we’re big fans of Micro needling, a gold-standard treatment that’s transforming the skin of many Tomball locals.
What is Micro needling?
Micro needling, or Collagen Induction Therapy, is a minimally invasive procedure that uses a specialized device to create thousands of tiny, microscopic channels in your skin’s surface.
Although the idea of tiny needles poking your skin might sound intimidating, don’t worry! It’s actually a gentle and highly effective process. These micro-injuries stimulate your body’s natural healing response, triggering the production of new collagen and elastin — essential building blocks for firm, smooth, and youthful-looking skin.

Why Tomball Locals Love Micro needling: 5 Key Benefits
If you’re still undecided about whether Micro needling is the right fit for you, here’s why this treatment is a fan favorite in Tomball:
1. The Ultimate Multi-Tasker
One of the best things about Micro needling is its versatility. Unlike treatments that only address one skin concern at a time, Micro needling tackles multiple issues in a single session. With just one treatment, we can improve:
- Fine lines and deep wrinkles
- Acne scars and pockmarks
- Enlarged pores
- Uneven skin texture and tone
- Sun damage and hyperpigmentation
It’s like a skin reset button that gives you a more youthful, even complexion from head to toe.
2. Natural, Effortless Results
One of the biggest advantages of Micro needling is that it works with your body’s own collagen production. That means no artificial-looking changes — just you, looking fresher, more rested, and glowing. Unlike Botox or fillers that can give a “frozen” appearance, Micro needling enhances your natural beauty, leaving you looking like the best version of yourself.
3. Minimal Downtime
Unlike other aggressive treatments like chemical peels or lasers, Micro needling offers a low-impact recovery time. Most clients experience redness similar to a mild sunburn for 24-48 hours, after which they’re ready to go about their normal routine — and even wear makeup! There’s no peeling, flaking, or discomfort that might make you want to hide at home. You’ll be glowing and ready to face the world in no time.
4. Boosts the Power of Your Skincare
Micro needling doesn’t just improve your skin; it also enhances the effectiveness of the skincare products you already use. After the treatment, your skin is primed to absorb serums and moisturizers up to 300% deeper than usual, allowing those pricey products to work even harder for you.
5. Safe for All Skin Types and Tones
If you’ve ever been hesitant to try laser treatments due to concerns about your skin tone, you’ll be happy to know that Micro needling is a great option for almost everyone. Unlike thermal treatments like lasers, which can be risky for darker skin tones, Micro needling uses mechanical action, making it safe and effective for all skin types. Whether your skin is fair or deep-toned, you can enjoy the benefits of a smoother, healthier complexion.
What to Expect at Enfield Royal Med Spa Tomball
We understand that trying a new treatment can be nerve-wracking, but rest assured that your comfort is our top priority. Here’s a look at what a typical Micro needling session at our spa involves:
- Numbing: To ensure the treatment is comfortable, we start by applying a high-quality numbing cream to the treatment area. Most clients only feel a light vibration during the process.
- The Treatment: A trained provider will gently glide the micro needling device over your skin. We can adjust the depth of the needles to target specific concerns like deep acne scars or fine lines around the eyes. The procedure usually takes 30-60 minutes, depending on the area treated.
- Soothe: Once the treatment is complete, we’ll apply soothing serums or a cooling mask to help calm your skin and kickstart the healing process.
Ready to Glow?
If you’ve been dealing with dull texture, stubborn scars, or uneven skin tone, Micro needling could be just the treatment you need to refresh your complexion.
At Enfield Royal Med Spa in Tomball, we specialize in creating personalized skincare plans tailored to your unique needs. Whether you want to smooth out fine lines, minimize sun spots, or rejuvenate your skin’s texture, we’re here to help you look and feel your best.
Stop by for a consultation today, and let’s discuss how Micro needling can help you achieve healthy, glowing skin that’s ready for anything.
Care
Gas Furnace Heating and Its Impact on Indoor Air Quality
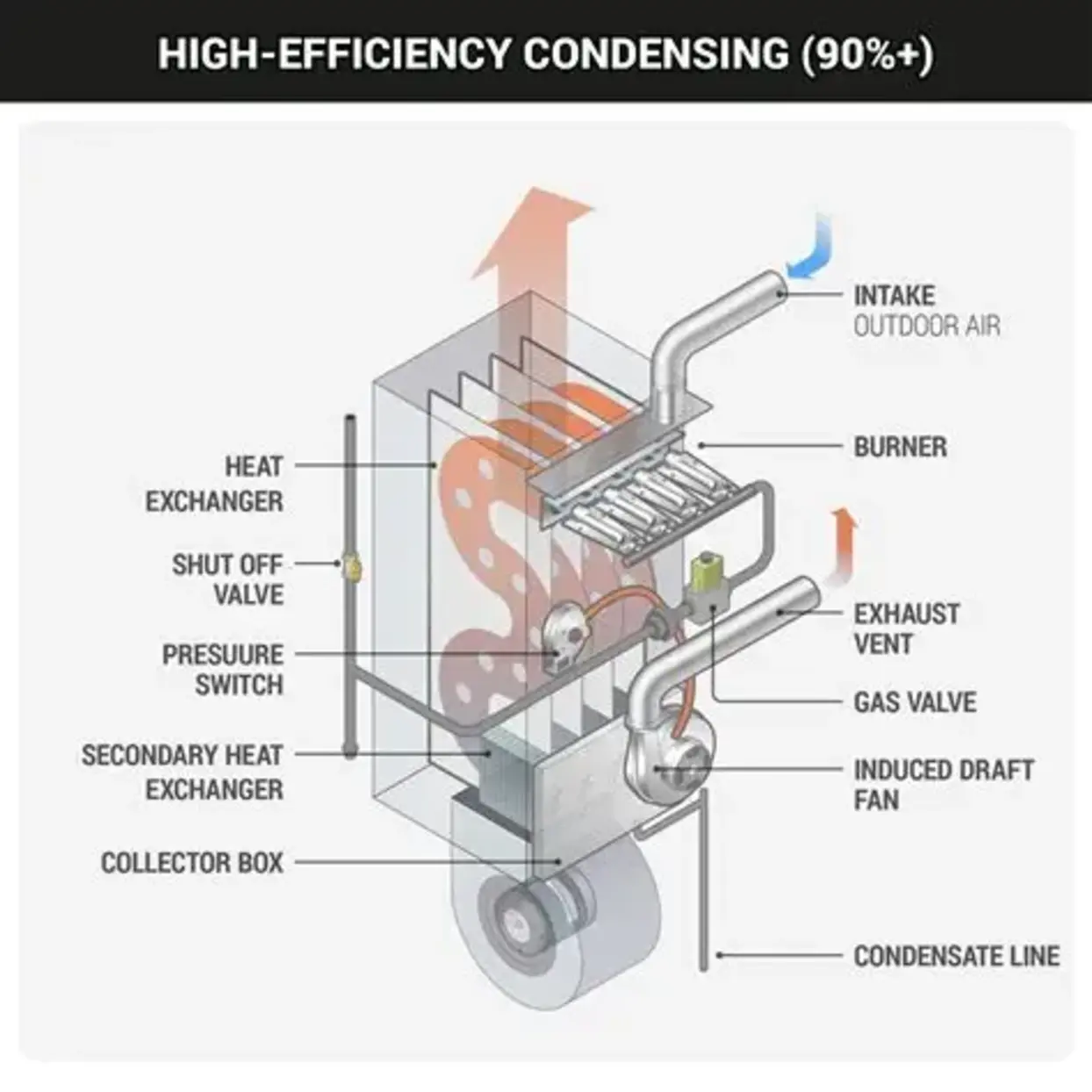
Indoor Air Quality (IAQ) has become a defining metric of building performance. Across residential, commercial, and light industrial spaces, occupants expect heating systems not only to deliver thermal comfort but also to support a healthy indoor environment. Gas furnace heating remains one of the most widely adopted solutions globally due to its reliability, efficiency, and cost-effectiveness. However, its impact on Indoor Air Quality depends heavily on system design, installation, and maintenance.
This article examines how gas furnaces influence Indoor Air Quality and outlines practical strategies to optimize performance while protecting occupant health.
Understanding How Gas Furnaces Operate
A gas furnace generates heat by burning natural gas or propane in a sealed combustion chamber. The combustion gases pass through a heat exchanger, transferring warmth to circulating air, which is then distributed throughout the building via ductwork. Modern high-efficiency furnaces use sealed combustion and direct venting systems to isolate combustion air from indoor air.
This distinction is critical. Older, non-sealed systems may draw combustion air from inside the building, which can negatively affect Indoor Air Quality if ventilation is inadequate. High-efficiency sealed combustion systems, by contrast, significantly reduce indoor contamination risk.

Key Indoor Air Quality Concerns with Gas Furnace Heating
1. Combustion Byproducts
Incomplete combustion can generate pollutants such as carbon monoxide (CO), nitrogen dioxide (NO₂), and trace particulate matter. Carbon monoxide is particularly dangerous due to its colorless and odorless nature.
Properly installed and tuned gas furnaces minimize these risks. Modern units incorporate advanced burner design, flame sensors, and safety shutoff controls to ensure stable combustion. Routine inspections and combustion analysis remain essential to maintaining Indoor Air Quality standards.
2. Particulate Circulation Through Ductwork
Gas furnaces rely on forced-air systems. If ductwork is poorly sealed or filtration is inadequate, dust, allergens, and debris can circulate through indoor spaces.
High-performance filtration systems play a central role here. MERV-rated filters capture varying particle sizes, and advanced systems can integrate HEPA filtration for enhanced Indoor Air Quality in sensitive environments such as healthcare or educational facilities.
3. Humidity Imbalance
Gas furnaces produce dry heat. During winter months, prolonged operation can reduce indoor relative humidity levels below recommended thresholds (30–50%). Low humidity can contribute to respiratory irritation, dry skin, static electricity, and increased viral transmission risk.
Integrated humidification solutions counteract this effect and help stabilize Indoor Air Quality.
Positive Contributions of Modern Gas Furnaces to Indoor Air Quality
While risks exist, modern gas furnace systems are engineered to actively support healthier indoor environments.
Sealed Combustion Technology
Sealed combustion furnaces isolate the combustion process from indoor air, drawing intake air from outside and venting exhaust externally. This prevents back drafting and reduces pollutant exposure. For new installations and retrofits, sealed systems are now the industry standard in high-performance buildings.
Advanced Filtration Integration
Today’s gas furnace platforms are designed to accommodate:
- High-efficiency media filters
- Electronic air cleaners
- UV germicidal lamps
- Bipolar ionization systems
When integrated correctly, these solutions significantly enhance Indoor Air Quality by targeting airborne particulates, microbial growth, and volatile organic compounds (VOCs).
Variable-Speed Blower Motors
Variable-speed ECM blower motors maintain consistent airflow and enable continuous low-speed circulation. This improves air mixing, reduces temperature stratification, and increases the effectiveness of filtration systems—ultimately contributing to better Indoor Air Quality across the entire space.
Installation Quality: The Deciding Factor
Even the most advanced furnace will fail to deliver optimal Indoor Air Quality if improperly installed.
Key installation considerations include:
- Correct furnace sizing based on load calculations
- Proper venting configuration
- Airtight duct sealing
- Balanced airflow distribution
- Adequate fresh air ventilation
Oversized systems short-cycle, reducing filtration time and humidity control. Undersized systems overwork and may stress components. Professional commissioning ensures that combustion efficiency and airflow performance align with Indoor Air Quality objectives.
Maintenance and Monitoring Best Practices
Maintaining Indoor Air Quality with gas furnace heating requires proactive care.
1. Regular Filter Replacement
Filters should be replaced according to manufacturer guidelines, typically every 1–3 months depending on usage and environmental conditions.
2. Annual Professional Inspection
Certified technicians should inspect burners, heat exchangers, venting systems, and safety controls annually to prevent combustion-related air quality issues.
3. Carbon Monoxide Detection
CO detectors should be installed on every occupied level. This is a non-negotiable safety requirement in gas-heated environments.
4. Duct Cleaning and Sealing
Periodic duct inspections prevent particulate buildup and leakage, supporting consistent Indoor Air Quality performance.
Integrating Gas Furnace Systems with IAQ-Focused Solutions
Forward-looking manufacturers are engineering gas furnace platforms that serve as central hubs for Indoor Air Quality management. These integrated systems may include:
- Smart thermostats with air quality monitoring
- Humidity sensors and control modules
- Ventilation energy recovery units (ERVs/HRVs)
- Real-time filter status alerts
By combining heating and air purification into a unified system, building owners can manage comfort and Indoor Air Quality simultaneously through centralized controls.
Global Considerations
In colder regions across North America, Europe, and parts of Asia, gas furnace heating remains a cornerstone of building infrastructure. However, regional air quality standards, building codes, and fuel availability vary widely.
Manufacturers serving a global market must design systems that:
- Meet local emissions regulations
- Accommodate diverse climate conditions
- Support both natural gas and propane options
- Integrate with varying ventilation standards
Global compliance and adaptability are now essential components of product development in the heating sector.
The Bottom Line
Gas furnace heating, when properly designed, installed, and maintained, does not inherently compromise Indoor Air Quality. On the contrary, modern high-efficiency systems can enhance IAQ through sealed combustion, advanced filtration compatibility, and integrated humidity management.
The true impact depends on system quality and lifecycle care. Building owners, facility managers, and HVAC professionals should prioritize equipment that supports comprehensive Indoor Air Quality strategies rather than viewing heating as an isolated function.
As Indoor Air Quality continues to gain global attention, gas furnace technology is evolving beyond simple heat delivery. The future lies in integrated, intelligent systems that provide comfort, safety, and cleaner indoor environments—without compromise.
Care
Fly Airlines Policies: Changing Flights, Cancellations, and Refunds

Flying is now a big part of the way we live today. People do it for work, fun, or to see family and friends. But sometimes, plans can change fast. You may have an emergency, need to work, or something else might come up. So, it helps to know the rules about changing flights, canceling trips, and getting your money back. The Fly Airlines Policy gives clear steps for travelers. It lets people handle their bookings quickly, save money, and have an easy trip.
Flight Change Policy
One of the main things that is part of the Fly Airlines Policy is how to change flights. Fly Airlines lets people change their booking in more than one way. You can do this on the official website, using the mobile app, or by calling customer support. All flight changes must follow the airline’s time rules. If you ask to change your flight close to the day you fly, you might have to pay higher fees or face more rules. This depends on the ticket type and fare details.
Passengers may need to pay a small fee for making changes. This fee can change based on the route, ticket type, and fare class. Also, you must pay any extra amount if your new booking costs more. For instance, if you want to move from an economy seat to a business class seat, you have to pay the higher fare when you make the change.

Some fare types, like fully refundable or premium tickets, give you more freedom. You can change them more than once, and you will not face big fees. Standard economy tickets are different. They can have more rules and limits. But the Fly Airlines Policy makes things clear. You will see all the details when you book your ticket.
When you travel to another country, Fly Airlines gives you more freedom if you have problems like visa delays, travel limits, or emergencies. Passengers should get in touch with customer help right away to talk about what they can do.
Cancellation Policy
Cancellations happen for many reasons. The Fly Airlines Policy gives clear steps to help with these. You can cancel your ticket on the airline’s website, by using their mobile app, or by calling their customer support hotline. There are fees for cancelling, and these depend on your fare type, when you cancel, and your flight route.
Fully refundable tickets let you get your money back if you need to cancel. You can do this right up to the day your flight leaves. You may not have to pay any fee or you might just pay a small one. Non-refundable tickets cost less, but there could be a fee if you want to cancel. Still, Fly Airlines often gives you some of your money back as travel credits or vouchers. You can use these for future tickets. This way, you do not lose the value of what you spent on your first ticket.
The Fly Airlines Policy also has rules for cases like extreme weather, natural disasters, or travel rules set by the government. When this happens, Fly Airlines might give fee waivers, rebooking choices, or travel credits to help make things easier for the passenger.
Refund Policy
The refund process is a key part of the Fly Airlines Policy. Refunds are usually given back using the same way as the first payment. It often takes about 7 to 14 business days for your refund to be done.
For tickets that you can get money back on, people can ask to get all their money back. The company might take out some service fees first. If your ticket is not one that you can get a refund for, you might get credit or a voucher instead of your money back. You can use these travel credits at another time. They are only good for a certain length of time. This lets people book a new trip later, so they do not lose the money from their ticket.
The policy also covers cases when the airline cancels a flight. In these times, the passenger will get a full refund or be given a new way to travel with no extra charge. If the airline changes the flight time, the passenger can take the new time or ask for a refund. This helps keep things fair and clear for everyone.
Passenger Support and Guidelines
Fly Airlines focuses on making things easy and clear for you. The Fly Airlines Policy says you should read the rules about your ticket when you book it. You should also keep a digital or paper copy of your booking confirmation. If there is any problem, get in touch with customer support right away.
It is good to use the online portal or the mobile app for making change policy.
-
Business3 years ago
Cybersecurity Consulting Company SequelNet Provides Critical IT Support Services to Medical Billing Firm, Medical Optimum
-
Business3 years ago
Team Communication Software Transforms Operations at Finance Innovate
-
Business3 years ago
Project Management Tool Transforms Long Island Business
-
Business2 years ago
How Alleviate Poverty Utilized IPPBX’s All-in-One Solution to Transform Lives in New York City
-
health3 years ago
Breast Cancer: The Imperative Role of Mammograms in Screening and Early Detection
-
Sports3 years ago
Unstoppable Collaboration: D.C.’s Citi Open and Silicon Valley Classic Unite to Propel Women’s Tennis to New Heights
-
Art /Entertainment3 years ago
Embracing Renewal: Sizdabedar Celebrations Unite Iranians in New York’s Eisenhower Park
-
Finance3 years ago
The Benefits of Starting a Side Hustle for Financial Freedom
































