Technology
Secure Your Mac: Essential Tips for Enhanced Security

Enhance Mac Security with Strong Passwords
At present online realm, maintaining the safety of your sensitive personal data is essential. If you utilize your Mac for professional purposes or for personal reasons, implementing proactive measures to keep your data safe and privacy is vital. Through the implementation of the subsequent actions, you can strengthen the protection of your Macintosh. These actions lessen the chance of unauthorized use.
Boost Mac Safety with Powerful Passwords
A key basic elements for ensuring the security of your Apple computer requires establishing secure and exclusive login credentials. Refrain from using easily guessable combinations like “qwerty” nor “admin.” Instead, choose complex passwords that incorporate both uppercase and lowercase letters, numbers, and special characters. Moreover, take into account using an online password tool for generating and storing your passwords with high security.
Simplify Authentication using Passwords on Apple Computers
In order to simplify the procedure for confirming identity and decrease dependence on typical password-based authentication. Mac presents the possibility of making use of passkeys. Passcodes use physical characteristics such as Touch ID or Facial Recognition to confirm user identity without password dependence. This removes the inconvenience of recalling and handling multiple passcodes. By activating passcodes, you can strengthen security and streamline the sign-in experience on your Macintosh.
Safeguard Your Apple computer using User Credentials
In case multiple people have direct access to your computer, it is crucial to configure isolated user profiles for every individual. This guarantees that every individual possesses their own individualized settings, documents, and confidentiality. Mandating users to sign in not just stops illegitimate entry but additionally guarantees that user data and configurations remain segregated. In this manner, every individual possesses exclusive control to their own files and preferences. It gets rid of the potential for manipulation or unapproved entry.

Photo by Desola Lanre-Ologun on Unsplash
Protect Your Mac with User Logins
In order to protect private or classified data kept on your Mac, think about utilizing FileVault safeguard. FileVault encrypts your information on your computer, blocking its accessibility unless the user password is typed. By activating FileVault, you provide an additional layer of security to your documents and stop unauthorized persons from gaining access to your information even though they acquire physical access to your Mac device. This guarantees that your personal confidential data stays safe and kept confidential.
Conclusion
Implementing measures to protect your personal computer is essential in the contemporary interconnected environment. By using robust passwords, installing passkeys, mandating user logins, safeguarding your Mac during idle periods, restricting administrative users, and securing your data with FileVault, you can substantially strengthen the security of your Mac. That will aid in securing the personal information from unapproved access.
Bear in mind, giving importance to Mac security is a never-ending task. Keep updated concerning the most recent security protocols and updates to software to guarantee the safety of your Mac against emerging dangers.
Costumer Services
Troubleshooting McAfee Antivirus: Common Issues and Solutions

McAfee antivirus is one of the most trusted security programs used to protect devices from viruses, malware, ransomware, and online threats. It offers real-time protection, firewall security, web protection, and identity monitoring features for complete digital safety. However, many users sometimes face issues like McAfee not responding, McAfee not opening, or the software failing to run properly. When McAfee stops working, your system may become vulnerable to cyber threats.
If you are experiencing a McAfee not working error, don’t worry. In this complete troubleshooting guide, we will explain the possible reasons and provide step-by-step solutions to fix the issue. If the problem continues, you may consider contacting the official McAfee support number for professional help.
Common Reasons Why McAfee Is Not Working
Before applying any fix, it’s important to understand why McAfee may stop working. Below are the most common causes:
- Corrupted or incomplete installation
- Outdated McAfee software version
- Conflict with another antivirus program
- Windows update errors
- Malware infection blocking the antivirus
- Damaged system files
- Expired subscription
Identifying the root cause can help you apply the right solution quickly.
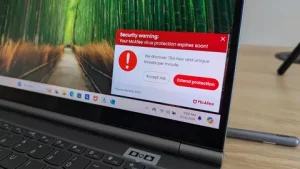
1. Restart Your Computer
Sometimes, temporary glitches or background processes can cause McAfee not responding issues. Restarting your computer can refresh system files and stop conflicting processes.
Steps:
- Close all open applications
- Click on Start
- Select Restart
After rebooting, try opening McAfee again. If McAfee is not opening, move to the next solution.
2. Check Your Internet Connection
McAfee requires an active internet connection for updates and license verification. A weak or unstable connection may prevent it from working properly.
- Restart your router
- Check if other websites are loading
- Try switching to a different network
Once your connection is stable, open McAfee again.
3. Update McAfee Antivirus
Running an outdated version can lead to performance issues and errors. Updating the software may fix the McAfee not responding problem.
Steps:
- Open McAfee (if accessible)
- Click on “PC Security” or “My Info”
- Select “Check for Updates”
- Install any available updates
- Restart your system
If McAfee is still not opening, continue troubleshooting.
4. Repair McAfee Installation
Corrupted installation files often cause McAfee not working errors. You can repair the software using Windows settings.
Steps to Repair:
- Press Windows + R and type
- Press Enter to open Programs and Features
- Select McAfee from the list
- Click Uninstall/Change
- Choose Repair
- Follow on-screen instructions
After completion, restart your PC and check if the issue is resolved.
5. Uninstall and Reinstall McAfee
If repair does not solve the problem, reinstalling McAfee can fix damaged or missing files.
Steps to Reinstall:
- Open Control Panel
- Click Programs > Uninstall a Program
- Select McAfee and click Uninstall
- Restart your computer
- Visit the official McAfee website
- Download the latest version
- Install and activate with your product key
This method commonly fixes McAfee not opening and startup errors.
6. Remove Conflicting Antivirus Software
Having more than one antivirus installed can cause serious software conflicts. If another security program is installed, uninstall it.
Steps:
- Open Control Panel
- Go to Programs and Features
- Uninstall any other antivirus software
- Restart your device
After removal, check whether McAfee works properly.
7. Install Pending Windows Updates
An outdated Windows system may create compatibility issues with McAfee.
Steps:
- Go to Settings
- Click Update & Security
- Select Windows Update
- Click Check for Updates
- Install available updates
- Restart your computer
Updating Windows often resolves performance and compatibility errors.
8. Run a Malware Scan
In some cases, malware can disable antivirus software. If McAfee not responding persists, use Windows Defender or Safe Mode to run a full system scan.
To scan in Safe Mode:
- Restart your computer
- Press F8 (or Shift + Restart on Windows 10/11)
- Select Safe Mode with Networking
- Run a full system scan
Remove any detected threats and restart normally.
9. Check Subscription Status
If your McAfee subscription has expired, some features may stop working.
- Log in to your McAfee account
- Check subscription status
- Renew if necessary
After renewal, reactivate the product.
When to Contact McAfee Support Number
If you have tried all the above solutions and McAfee is still not working, the issue may be technical or account-related. In such cases, contacting the official McAfee support number is recommended. Certified experts can help diagnose advanced problems such as:
- Activation errors
- License key issues
- Severe system conflicts
- Persistent McAfee not opening errors
Always make sure to contact official support channels to avoid scams.
Final Thoughts
Facing issues like McAfee not responding or McAfee not opening can be frustrating, especially when your device security is at risk. Fortunately, most McAfee not working errors can be fixed by restarting your system, updating the software, repairing installation files, or reinstalling the program.
Follow the step-by-step troubleshooting guide above to restore your antivirus protection quickly. If the problem remains unresolved, reaching out to the official McAfee support number can provide expert assistance and ensure your system stays protected.
Disclaimer:-
If you require official assistance, we recommend contacting McAfee directly through their official website or authorized customer support channels. Any reference to the “McAfee support number” in this content is intended strictly for informational purposes
Digital Development
IP PBX System: Benefits for Remote Access and Scalability

Growing companies face one common problem. Communication becomes hard to manage as teams expand across cities and time zones. A simple phone line no longer supports daily operations. Teams require a unified system that links office personnel, remote employees, and branch sites.
An IP PBX System solves this challenge by moving business calls to the internet. It replaces old phone wiring with software based control. Calls travel through data networks instead of copper lines. This allows teams to connect from anywhere using desk phones, laptops or mobile apps.
For companies with distributed teams this setup keeps everyone on the same network. It creates one shared system for internal and external communication. When communication improves work moves faster and service quality stays steady.
Why Traditional Phone Systems Fail Growing Teams
Old phone systems were built for single offices. They depend on physical wiring and hardware boxes placed on site. When a company grows, adding new lines becomes costly and slow. Maintenance also requires technical support on location.
Distributed teams make this problem worse. Remote staff cannot easily connect to the office switchboard. Internal call transfers become difficult. Managers struggle to track calls and monitor service levels.
An IP PBX System removes these limits. Since it works through the internet teams can connect from any location. A sales agent working from home uses the same system as someone in the main office. This keeps operations unified and easier to manage.

How Internet Based Calling Works
Voice calls convert into digital signals and travel through secure networks. The system routes calls to the right extension without manual handling. This process happens within seconds and does not need extra wiring.
Centralized Communication for Distributed Teams
When teams work from different places they still need one shared communication platform. A single dashboard helps manage users extensions, call routing and reports. Managers can see activity levels and track performance in real time.
Using hosted call center software along with an IP PBX System adds more control. Calls can be recorded, monitored and routed based on team roles. Remote agents log in from anywhere while staying connected to the company network.
This central structure supports smooth collaboration. Internal calls remain free within the system. Teams can hold conference calls without extra tools. Messages and voicemails stay stored in one place. That reduces confusion and saves time each day.
Easy Scalability Without Heavy Setup
Growing companies need systems that expand quickly. Hiring new staff should not require complex hardware changes. Adding a new user in an IP PBX System usually takes only a few minutes. An admin assigns an extension and the employee logs in from any device.
Hosted call center software strengthens this benefit. Since the platform runs on remote servers companies avoid large upfront costs. There is no need for physical switchboards or bulky machines. Updates happen automatically through the provider.
Scalability allows businesses to grow without stress on communication tools. Teams stay productive even during expansion.
Remote Access and Mobility
Employees can answer calls using mobile apps or softphones. A stable internet link is enough to stay connected. This ensures that customer calls never depend on one physical office.
Better Call Control and Management
Efficient call handling improves both team productivity and customer experience. An IP PBX System offers smart call routing based on department time or agent availability. Calls reach the right person without delay.
Features such as call transfer voicemail to email and call recording support daily operations. Managers monitor call flow and identify service gaps. Reports provide clear insight into call volume and response times.
Hosted call center software adds advanced management options. Supervisors can track agent performance and maintain service standards across locations. Training becomes easier because call recordings help review real conversations.
This level of control supports faster decision making. Instead of guessing, managers rely on real data. That leads to better service quality and improved team coordination.
Cost Efficiency and Long Term Value
Communication costs often rise as businesses expand. Traditional systems charge for line rentals, hardware repair and maintenance visits. International calls also add high fees.
An IP PBX System lowers many of these expenses. Calls over the internet reduce long distance costs. Maintenance shifts to software updates instead of hardware repairs. Since the system uses existing data networks companies avoid heavy installation work.
Hosted call center software further reduces capital spending. Businesses pay based on usage or number of users. This makes budgeting easier and more predictable. Small companies benefit from enterprise level features without large investment.
Over time savings from maintenance call charges and hardware upgrades add real value. The system becomes a stable base for future growth.
Security and Reliability for Modern Teams
Business communication must remain secure and reliable. Internet based systems use encryption and secure access controls to protect call data. User permissions limit who can access settings or recordings.
Cloud based backups ensure that data remains safe even if one location faces technical issues. Teams can continue working from other sites without service interruption.
For distributed companies this reliability builds trust. Employees stay connected. Customers receive consistent support. Communication no longer depends on one office building.
Supporting Growth Without Complexity
Growing teams need structure not confusion. An IP PBX System provides that structure while keeping operations simple. It brings all calls, extensions and reports into one easy interface.
When combined with hosted call center software the system supports remote agents supervisors and managers in one shared environment. Everyone stays aligned even when working from different regions.
Clear communication supports faster response times, stronger collaboration and steady service quality. As companies expand they require tools that grow with them. A modern IP based phone system offers that stability.
Strong internal and external communication builds trust among teams and customers. For businesses planning long term growth this type of system becomes an essential part of daily operations.
Digital Development
Boldify for Facebook: Quick Bold Text in Seconds

Scroll through Facebook for just five minutes and you’ll notice something: most posts look exactly the same. Plain text blends into the feed, making it easy for users to scroll past without noticing important messages. In a crowded social media environment, visual formatting plays a major role in grabbing attention and increasing engagement. This is where Boldify, a powerful bold text generator, makes a difference. Instead of struggling with plain, unformatted posts, Boldify allows you to create eye-catching Facebook bold text instantly. In this article, you’ll learn why bold text matters, how Boldify works, and how you can use it to stand out on Facebook within seconds.
Why Bold Text Matters on Facebook (User Engagement Psychology)
Facebook is a fast-moving platform. Users scroll quickly, often stopping only when something visually stands out. Bold text works because it creates contrast. When certain words appear heavier or more prominent, the brain processes them faster.
Here’s why bold text improves engagement:
- It grabs attention in crowded feeds.
- It improves readability and scan ability.
- It highlights key messages instantly.
Bold formatting is especially powerful in:
- Facebook posts
- Comments
- Bios
- Facebook groups
If you’re building a brand or growing a personal profile, bold text strengthens your identity. It emphasizes important announcements, promotions, or calls to action, making your message harder to ignore.
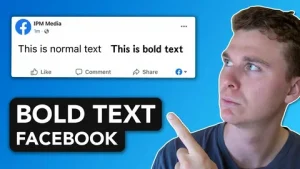
The Challenge: Facebook Doesn’t Offer Built-In Bold Formatting
One of the biggest frustrations for users is that Facebook does not provide built-in bold formatting for regular posts. Unlike word processors, you cannot simply select text and click “Bold.”
That’s why many people search for:
- how to bold text on Facebook
- Facebook bold text generator
- bold letters for Facebook
Without a proper tool, users are left copying complicated codes or trying ineffective formatting tricks. This creates a clear need for a reliable and easy-to-use bold font generator.
What Is Boldify?
Boldify is an online bold text generator designed to help users create stylish bold letters instantly. Instead of modifying Facebook’s formatting, Boldify uses Unicode-based bold fonts that are fully compatible with social media platforms.
Here’s what makes Boldify simple and powerful:
- No installation required
- Works directly in your browser
- Free and instant access
- Compatible with Facebook, Instagram, Twitter, and WhatsApp
Because it uses special Unicode characters, the bold text appears naturally once pasted into Facebook posts, comments, bios, or Messenger chats. This makes Boldify a practical and beginner-friendly solution for anyone looking to create bold text online.
How Boldify Helps You Create Bold Facebook Text in Seconds
Using Boldify is straightforward and requires no technical knowledge. Here’s a simple step-by-step guide:
Step 1: Enter Your Text
Open Boldify and type your message into the input box. This could be a status update, promotional message, announcement, or bio line.
Example:
New Blog Post Live
Limited Time Offer
Join Our Community Today
Step 2: Automatic Bold Conversion
As soon as you enter your text, Boldify automatically converts it into multiple bold font styles. Within seconds, you’ll see several variations generated instantly.
Step 3: Copy and Paste to Facebook
Choose the bold style you like, click the copy button, and paste it directly into:
- Facebook posts
- Comments
- Bios
- Messenger chats
That’s it. In just a few seconds, your plain text becomes visually powerful Facebook bold text.
Key Features That Make Boldify Stand Out
There are many tools online, but Boldify offers specific advantages that make it reliable and user-friendly.
1. One-Click Copy Feature
No need to manually select text. Just click and copy instantly.
2. Multiple Bold Style Variations
Get access to different bold styles to match your tone and branding.
3. Mobile-Friendly Interface
Boldify works smoothly on smartphones, tablets, and desktops.
4. No Login Required
You don’t need to create an account. Just open and start using.
5. Fast Performance
Text conversion happens instantly without delays.
6. Clean and Simple Design
The interface is distraction-free, making it easy for beginners to use.
These features make Boldify more than just a basic bold letters generator—it becomes a practical social media enhancement tool.
Practical Ways to Use Bold Text on Facebook
Now that you know how to generate bold text, let’s explore practical ways to use it effectively.
Highlight Important Announcements
SALE TODAY ONLY
Registration Closes Tonight
Bold formatting ensures these messages get noticed quickly.
Strengthen Call-to-Actions
Instead of writing:
Join us now
Write:
JOIN US NOW
It creates urgency and clarity.
Emphasize Keywords in Posts
Highlight important parts of your message to guide the reader’s attention.
Improve Facebook Bios
Use bold text to make your profession, tagline, or brand name stand out.
Stand Out in Facebook Groups
When commenting in large groups, bold text increases visibility and improves response rates.
SEO & Branding Benefits of Using Bold Text
While bold text doesn’t directly change Facebook’s algorithm, it improves how users interact with your content.
Here’s how it benefits branding and visibility:
- Improves readability
- Encourages longer post engagement
- Strengthens personal or business branding
- Creates structured content hierarchy
- Makes posts look professional
When your content looks organized and visually appealing, users are more likely to stop scrolling and engage.
Tips for Using Bold Text Effectively
Bold text is powerful—but only when used strategically.
- Don’t overuse bold formatting.
- Highlight only key phrases or calls-to-action.
- Combine bold text with emojis carefully.
- Maintain readability and spacing.
Too much bold text can reduce its impact. The goal is to enhance clarity, not overwhelm the reader.
Conclusion
Standing out on Facebook is no longer optional—it’s necessary. Since Facebook doesn’t offer built-in bold formatting for posts, tools like Boldify provide a fast and effective solution.
-
Business3 years ago
Cybersecurity Consulting Company SequelNet Provides Critical IT Support Services to Medical Billing Firm, Medical Optimum
-
Business3 years ago
Team Communication Software Transforms Operations at Finance Innovate
-
Business3 years ago
Project Management Tool Transforms Long Island Business
-
Business3 years ago
How Alleviate Poverty Utilized IPPBX’s All-in-One Solution to Transform Lives in New York City
-
health3 years ago
Breast Cancer: The Imperative Role of Mammograms in Screening and Early Detection
-
Sports3 years ago
Unstoppable Collaboration: D.C.’s Citi Open and Silicon Valley Classic Unite to Propel Women’s Tennis to New Heights
-
Art /Entertainment3 years ago
Embracing Renewal: Sizdabedar Celebrations Unite Iranians in New York’s Eisenhower Park
-
Finance3 years ago
The Benefits of Starting a Side Hustle for Financial Freedom






























