Technology Explained
The Role of Quantum Cryptography in Secure Communications

Quantum cryptography stands at the forefront of cybersecurity, leveraging principles of quantum mechanics to ensure unprecedented levels of security in communications. Unlike traditional cryptographic methods, which rely on complex mathematical algorithms, quantum cryptography utilizes quantum properties such as superposition and entanglement to enable secure key distribution and data transmission.
Principles of Quantum Cryptography
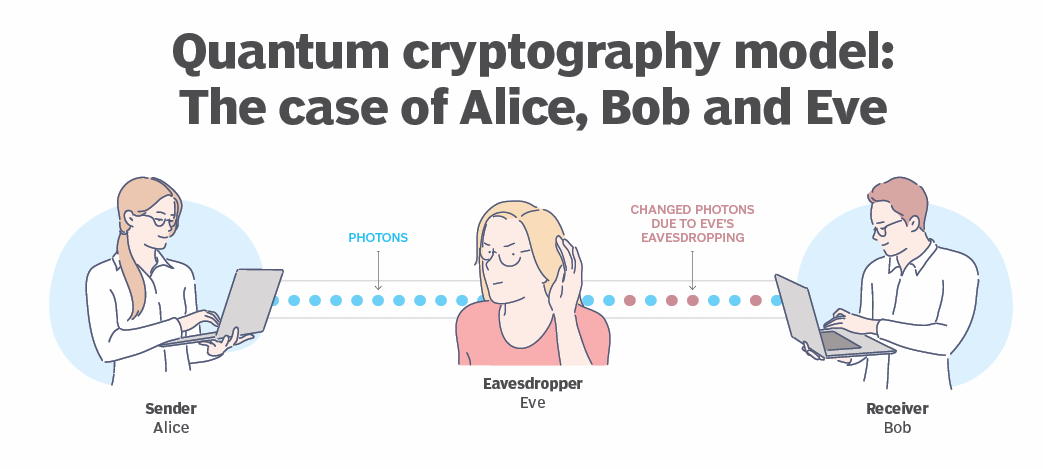
Image by : Yandex
At its core, quantum cryptography relies on quantum key distribution (QKD) protocols like BB84 and E91 to exchange encryption keys securely. These protocols leverage the quantum properties of photons to create cryptographic keys that are inherently secure against eavesdropping attempts. This ensures that any attempt to intercept the key alters its quantum state, alerting both sender and receiver to potential security breaches.
Applications of Quantum Cryptography
In practical terms, quantum cryptography offers robust solutions for secure data transmission across various sectors, including telecommunications, finance, and government. Organizations like ID Quantique and QuintessenceLabs have pioneered quantum key generation and management systems, integrating them into critical infrastructure where data security is paramount. These systems provide a defense against quantum computing threats, which conventional cryptographic methods may be vulnerable to in the future.
Challenges and Limitations
Despite its promise, quantum cryptography faces challenges such as scalability and cost-effectiveness. Implementing QKD systems requires advanced infrastructure and significant initial investments, limiting widespread adoption. Additionally, ensuring compatibility and regulatory compliance across different jurisdictions remains a hurdle for global deployment.
Future Outlook and Innovations
Looking ahead, advancements in quantum computing hold the potential to both enhance and challenge quantum cryptography. Innovations in quantum-resistant algorithms are underway to prepare for future threats posed by quantum computers. Moreover, international efforts are focused on standardizing quantum cryptography protocols and ensuring regulatory alignment to facilitate broader adoption.
Quantum Cryptography in Practice
In practice, quantum cryptography addresses fundamental challenges of traditional cryptographic methods by leveraging quantum phenomena. Quantum key distribution (QKD) protocols, such as BB84, enable the creation of cryptographic keys that are resistant to interception due to the principles of quantum mechanics. This ensures that any attempt to observe or measure quantum states by a third party inevitably alters the state of the quantum particles, thereby alerting the sender and receiver to the presence of an eavesdropper. As a result, quantum cryptography provides a level of security that is theoretically unbreakable, offering robust protection against both current and future threats in the realm of cybersecurity.
Real-World Applications
The adoption of quantum cryptography extends across various industries where secure communications are critical. For instance, in telecommunications, quantum-secure networks ensure confidential transmission of sensitive data and communications between government agencies and financial institutions. These networks employ quantum key distribution to safeguard against cyber espionage and data breaches, supporting national security and protecting proprietary information. Moreover, in sectors like healthcare and e-commerce, where privacy and data integrity are paramount, quantum cryptography offers a trustworthy framework for secure transactions and the protection of personal information.
Technological Advancements

Image by : Yandex
Technological advancements in quantum cryptography continue to drive innovation in cybersecurity. Companies and research institutions are exploring novel approaches to enhance the efficiency and scalability of QKD systems. Innovations in quantum repeaters and quantum memories aim to extend the range and reliability of quantum-secure communication networks. Additionally, efforts in quantum-resistant cryptography aim to develop algorithms capable of withstanding potential threats posed by quantum computers, ensuring long-term security for encrypted data.
Challenges and Considerations
Despite its potential, quantum cryptography faces several practical challenges. The implementation of QKD systems requires sophisticated infrastructure and specialized equipment, which can be costly and complex to deploy. Moreover, achieving interoperability and standardization across different quantum cryptography platforms remains a challenge for widespread adoption. Additionally, regulatory frameworks and compliance requirements vary globally, posing hurdles for seamless integration of quantum cryptography into existing communication networks and systems.
Future Directions
Looking ahead, the future of quantum cryptography holds promise for advancing cybersecurity capabilities. Continued research and development efforts are focused on overcoming current limitations and scaling quantum cryptography solutions for broader commercial and industrial applications. As quantum computing technology matures, the integration of quantum-resistant algorithms and quantum-enhanced security measures will play a pivotal role in safeguarding digital communications and securing critical infrastructures worldwide.
These additional paragraphs expand on the practical applications, technological advancements, challenges, and future directions of quantum cryptography in secure communications. They provide a more comprehensive view of how this cutting-edge technology is reshaping cybersecurity strategies and protecting sensitive information in various sectors globally.
Public and Private Sector Adoption
The adoption of quantum cryptography extends beyond traditional sectors into government and private industries, where secure communications are vital. Governments worldwide are investing in quantum-safe infrastructure to protect national security interests, confidential communications, and critical infrastructure from cyber threats. In the private sector, industries such as banking and finance are exploring quantum cryptography solutions to fortify digital transactions, secure financial data, and ensure compliance with stringent data protection regulations. As quantum technologies mature and become more accessible, collaborations between public and private entities will accelerate the deployment of quantum cryptography across diverse applications.
Educational and Research Initiatives
Educational institutions and research organizations play a crucial role in advancing quantum cryptography through fundamental research and practical applications. Universities and labs worldwide are conducting pioneering research in quantum mechanics, photonics, and information theory to develop cutting-edge QKD (Quantum key distribution) protocols and quantum-resistant algorithms. Collaborative efforts between academia and industry facilitate knowledge transfer and skill development in quantum cryptography, preparing the next generation of cybersecurity professionals and engineers to address evolving challenges in secure communications. By fostering interdisciplinary collaborations and promoting knowledge-sharing initiatives, educational initiatives contribute to the ongoing evolution and adoption of quantum cryptography in global cybersecurity landscapes.
Competitive Analysis Table
| Company/Organization | Quantum Cryptography Solutions | Key Technologies | Market Presence |
| ID Quantique | Quantum Key Distribution (QKD) | BB84 protocol, QRNG | Global telecommunications and government sectors |
| QuintessenceLabs | Quantum-enhanced cybersecurity | Quantum key generation, encryption key management | Financial services, defense sectors |
| Toshiba | Quantum Cryptography Network Solutions | QKD, quantum encryption | Commercial and government communication networks |
| MagiQ Technologies | Quantum Optical Networking Solutions | QKD, entangled photon sources | Optical quantum communication technologies |
Strategic Analysis Table
| Consideration | Description | Benefits | Challenges |
| Security Assurance | High-level security through quantum principles | Unbreakable encryption, protection against quantum attacks | Integration complexity, scalability |
| Regulatory Compliance | Meeting data protection standards | Compliance with privacy regulations, global regulatory alignment | Standardization, legal complexities |
| Cost-effectiveness | Balancing security benefits with costs | Long-term data protection, risk mitigation | Initial investment, affordability |
Conclusion
In conclusion, quantum cryptography represents a paradigm shift in cybersecurity, offering unparalleled levels of protection for sensitive communications and data. By harnessing the principles of quantum mechanics, quantum key distribution (QKD) protocols ensure secure key exchange and data transmission that is resistant to interception, even by advanced computing systems. The adoption of quantum cryptography is gaining momentum across various industries, including telecommunications, finance, healthcare, and government, where data security and privacy are paramount concerns.
Looking forward, the future of quantum cryptography holds tremendous promise and potential. Continued advancements in quantum computing and quantum networking technologies will further enhance the scalability, efficiency, and reliability of quantum cryptography systems. Research efforts in quantum-resistant algorithms and protocols will continue to evolve, addressing challenges such as interoperability, cost-effectiveness, and regulatory compliance. Moreover, collaborative initiatives between academia, industry, and governments will play a crucial role in accelerating the adoption and standardization of quantum cryptography solutions globally.
As organizations navigate an increasingly complex and interconnected digital landscape, quantum cryptography stands poised to provide robust safeguards against emerging cyber threats and vulnerabilities. By integrating quantum-safe solutions into their cybersecurity frameworks, businesses and governments can strengthen their defenses, safeguard sensitive information, and uphold trust and reliability in digital communications. Ultimately, quantum cryptography represents not only a technological advancement but also a critical enabler of secure and resilient communication infrastructures in the digital age.
Digital Development
Vhsgjqm: Understanding Abstract Identifiers in the Digital Age
Costumer Services
SBCGlobal Email Not Receiving Emails: A Comprehensive Guide

Introduction
If you’re facing problems with SBCGlobal email not receiving emails, you’re not alone. Many users experience email delivery issues caused by server settings, outdated configurations, or account security errors. This guide will walk you through why your SBCGlobal email might not be receiving messages, how to fix it step-by-step, and when to contact professional suppor for advanced troubleshooting.
What Is SBCGlobal Email?
SBCGlobal.net is a legacy email service originally provided by Southwestern Bell Corporation, which later merged with AT&T. Even though new SBCGlobal accounts are no longer being created, millions of users still access their SBCGlobal email through AT&T’s Yahoo Mail platform.
However, because SBCGlobal operates on older infrastructure and server settings, users sometimes experience email syncing, login, or receiving issues especially when using third-party apps or outdated settings.

Common Reasons SBCGlobal Email Is Not Receiving Emails
Before you start troubleshooting, it’s important to identify what might be causing the issue. Below are the most frequent culprits behind SBCGlobal email receiving problems:
- Incorrect Email Settings: If your incoming (IMAP/POP3) or outgoing (SMTP) settings are incorrect, emails won’t load properly.
- Server Outages: Temporary outages or server maintenance by AT&T or Yahoo may interrupt incoming mail delivery.
- Storage Limit Reached: When your mailbox exceeds its storage limit, new emails are automatically rejected.
- Spam or Filter Rules: Overly strict filters or incorrect spam settings might send legitimate emails to the Junk or Trash folder.
- Browser Cache or App Glitches: Cached data and outdated email apps can disrupt syncing or message retrieval.
- Blocked Senders or Blacklisted IPs: Accidentally blocking a sender or being on a spam blacklist may prevent messages from reaching your inbox.
- Security or Account Lock Issues: Suspicious login attempts or password errors can cause temporary account restrictions.
Step-by-Step Solutions to Fix SBCGlobal Email Not Receiving Emails
Let’s go through a series of troubleshooting steps to help you restore your email flow. You can perform these solutions on both desktop and mobile platforms.
1. Check SBCGlobal Email Server Status
- Sometimes, the issue isn’t on your end.
- Go to Downdetector or AT&T’s official website to see if SBCGlobal or AT&T Mail is down.
If there’s an outage, you’ll need to wait until the service is restored.
2. Verify Your Internet Connection
Ensure your device has a stable and fast internet connection. Poor connectivity can stop your email client from syncing or fetching new messages.
3. Update Incoming and Outgoing Mail Server Settings
Outdated or incorrect settings are the most common reason SBCGlobal email stops receiving messages. Here are the correct configurations:
Common Reasons SBCGlobal Email Is Not Receiving Emails
Before you start troubleshooting, it’s important to identify what might be causing the issue. Below are the most frequent culprits behind SBCGlobal email receiving problems:
- Incorrect Email Settings: If your incoming (IMAP/POP3) or outgoing (SMTP) settings are incorrect, emails won’t load properly.
- Server Outages: Temporary outages or server maintenance by AT&T or Yahoo may interrupt incoming mail delivery.
- Storage Limit Reached: When your mailbox exceeds its storage limit, new emails are automatically rejected.
- Spam or Filter Rules: Overly strict filters or incorrect spam settings might send legitimate emails to the Junk or Trash folder.
- Browser Cache or App Glitches: Cached data and outdated email apps can disrupt syncing or message retrieval.
- Blocked Senders or Blacklisted IPs: Accidentally blocking a sender or being on a spam blacklist may prevent messages from reaching your inbox.
- Security or Account Lock Issues: Suspicious login attempts or password errors can cause temporary account restrictions.
Step-by-Step Solutions to Fix SBCGlobal Email Not Receiving Emails
Let’s go through a series of troubleshooting steps to help you restore your email flow. You can perform these solutions on both desktop and mobile platforms.
1. Check SBCGlobal Email Server Status
- Sometimes, the issue isn’t on your end.
- Go to Downdetector or AT&T’s official website to see if SBCGlobal or AT&T Mail is down.
If there’s an outage, you’ll need to wait until the service is restored.
2. Verify Your Internet Connection
Ensure your device has a stable and fast internet connection. Poor connectivity can stop your email client from syncing or fetching new messages.
3. Update Incoming and Outgoing Mail Server Settings
Outdated or incorrect settings are the most common reason SBCGlobal email stops receiving messages. Here are the correct configurations:
- Server:
imap.mail.att.net - Port: 993
- Encryption: SSL
- Username: Your full SBCGlobal email address
- Password: Your email password
Outgoing Mail (SMTP) Server:
- Server:
smtp.mail.att.net - Port: 465 or 587
- Encryption: SSL/TLS
- Requires Authentication: Yes
If you’re using POP3, use:
- Incoming server:
inbound.att.net, Port 995 (SSL required) - Outgoing server:
outbound.att.net, Port 465 (SSL required)
Double-check these settings in your email client (Outlook, Apple Mail, Thunderbird, etc.) to make sure they match.
4. Review Spam and Junk Folder
- Sometimes, legitimate emails end up in the Spam or Junk folder. Open these folders and mark any wrongly filtered emails as “Not Spam.”
- Also, check your Filters and Blocked Addresses under email settings to ensure no important addresses are being redirected or blocked.
5. Clear Browser Cache or Update Your App
If you access SBCGlobal email through a browser:
- Clear your cache, cookies, and browsing history.
- Try opening email in incognito/private mode to rule out extensions or ad blockers causing problems.
If you use the Yahoo Mail App or Outlook, ensure the app is updated to the latest version. Outdated apps may not sync with the latest server configurations.
6. Check Mailbox Storage Limit
- SBCGlobal email accounts have a maximum storage quota.
- Delete unnecessary emails from your inbox, sent, and trash folders.
- After clearing space, refresh your inbox or restart your email client — new emails should start appearing.
7. Reset or Re-Add Your SBCGlobal Account
- If none of the above methods work, try removing your SBCGlobal account from your email client and re-adding it with the correct settings.
- This refreshes the connection and often resolves syncing or server timeout issues.
8. Reset Your Password
If you suspect your account might have been compromised or temporarily locked, resetting your password is a smart step.
- Visit the AT&T Password Reset page.
- Follow the on-screen steps to verify your identity.
- Set a strong, unique password and re-login to your email account.
9. Disable Security Software Temporarily
- Firewall or antivirus software can sometimes block email servers.
- Temporarily disable them (only if you’re confident about your network security) and check if you start receiving emails again.
10. Contact SBCGlobal Email Support
- If you’ve followed all the steps and your SBCGlobal email is still not receiving messages, the issue might be server-side or linked to account configuration.
- In that case, it’s best to contact SBCGlobal email support for expert help.
You can reach certified technicians.
They can assist with:
- Account recovery and login errors
- Server synchronization issues
- Email migration or backup
- Advanced spam and security settings
Having professional help ensures your account is restored quickly without losing any important messages or data.
Tips to Prevent Future SBCGlobal Email Problems
- Update Passwords Regularly: Keep your email account secure and avoid login lockouts.
- Use a Reliable Email App: Apps like Outlook or Apple Mail handle IMAP connections more efficiently.
- Backup Emails Periodically: Regular backups protect your messages from unexpected sync failures.
- Keep Storage Under Control: Delete old attachments and large files frequently.
- Monitor Account Activity: Check for unusual login attempts from unknown locations.
Final Thoughts
Facing issues like SBCGlobal email not receiving emails can be frustrating, especially when you rely on your email for important communications. However, most problems can be resolved by verifying server settings, clearing browser cache, managing storage, or resetting passwords.
If you continue to face challenges, don’t hesitate to reach out to expert SBCGlobal email support for personalized assistance. A few minutes of professional troubleshooting can save hours of frustration and get your SBCGlobalemail running smoothly again.
Development
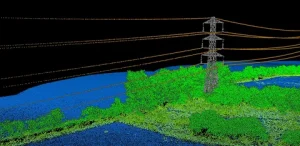
Enhancing Mapping Accuracy with LiDAR Ground Control Targets
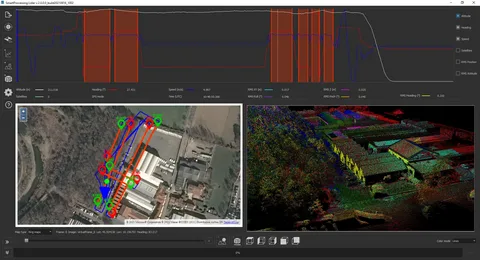
How Do LiDAR Ground Control Targets Work?
LiDAR technology uses laser pulses to scan the ground and capture a wide range of data, including elevation, shape, and distance. However, the data collected by LiDAR sensors needs to be aligned with real-world coordinates to ensure its accuracy. This is where LiDAR ground control targets come in.
Georeferencing LiDAR Data
When LiDAR sensors capture data, they record it as a point cloud, an array of data points representing the Earth’s surface. To make sense of these data points, surveyors need to assign them precise coordinates. Ground control targets provide reference points, allowing surveyors to georeference point cloud data and ensure that LiDAR data aligns with existing maps and models.
By placing LiDAR ground control targets at specific locations on the survey site, surveyors can perform adjustments to correct discrepancies in the data caused by factors such as sensor calibration, flight altitude, or atmospheric conditions.
Why Are LiDAR Ground Control Targets Essential for Accurate Mapping?
LiDAR technology is incredibly powerful, but the accuracy of the data depends largely on the quality of the ground control points used. Here are the key reasons why LiDAR ground control targets are essential for obtaining precise mapping results:
1. Improved Geospatial Accuracy
Without ground control targets, LiDAR data is essentially “floating” in space, meaning its position isn’t aligned with real-world coordinates. This can lead to errors and inaccuracies in the final map or model. By placing LiDAR ground control targets at known geographic coordinates, surveyors can calibrate the LiDAR data and improve its geospatial accuracy.
For large projects or those involving multiple data sources, ensuring that LiDAR data is properly georeferenced is critical. Ground control targets help ensure the survey data integrates seamlessly with other geographic information systems (GIS) or mapping platforms.
2. Reduction of Measurement Errors
LiDAR ground control targets help mitigate errors caused by various factors, such as:
- Sensor misalignment: Minor inaccuracies in the LiDAR sensor’s position or angle can cause discrepancies in the data.
- Aircraft or drone movement can slightly distort the sensor’s collected data.
- Environmental conditions: Weather, temperature, and atmospheric pressure can all affect the LiDAR signal.
By using ground control targets, surveyors can compensate for these errors, leading to more precise and reliable data.
3. Support for Large-Scale Projects
For larger mapping projects, multiple LiDAR scans might be conducted from different flight paths or at different times. Ground control targets serve as common reference points, ensuring that all collected data can be merged into a single coherent model. This is particularly useful for projects involving vast areas like forests, mountain ranges, or large urban developments.
How to Choose the Right LiDAR Ground Control Targets
Choosing the right LiDAR ground control targets depends on several factors, including the project’s size, the terrain, and the required accuracy. Here are some things to consider:
Size and Visibility
The size of the target should be large enough to be easily detectable by the LiDAR sensor from the air. Targets that are too small or poorly placed can lead to inaccurate data or missed targets.
Material and Durability
Ground control targets must have enough durability to withstand weather conditions and remain stable throughout the surveying process. Surveyors often use reflective materials to ensure that the LiDAR sensor can clearly detect the target, even from a distance.
Geospatial Accuracy
For high-accuracy projects, surveyors must place ground control targets at precise, known locations with accurate geospatial coordinates. They should use a GPS or GNSS system to measure and mark the exact position of the targets.
Conclusion
LiDAR ground control targets play a pivotal role in ensuring the accuracy of aerial surveys and LiDAR mapping projects. By providing precise reference points for geo referencing and adjusting LiDAR data, these targets reduce errors and improve the overall quality of the final model. Whether you’re working on a small-scale project or a large-scale survey, integrating ground control targets into your LiDAR workflow is essential for achieving high-precision results.
The right ground control targets, when placed correctly and properly measured, can make the difference between reliable, actionable data and inaccurate measurements that undermine the entire survey.
By understanding the importance of these targets and how they function in the context of LiDAR surveys, you’ll be better prepared to tackle projects that demand accuracy and precision.
-
Business3 years ago
Cybersecurity Consulting Company SequelNet Provides Critical IT Support Services to Medical Billing Firm, Medical Optimum
-
Business3 years ago
Team Communication Software Transforms Operations at Finance Innovate
-
Business3 years ago
Project Management Tool Transforms Long Island Business
-
Business2 years ago
How Alleviate Poverty Utilized IPPBX’s All-in-One Solution to Transform Lives in New York City
-
health3 years ago
Breast Cancer: The Imperative Role of Mammograms in Screening and Early Detection
-
Sports3 years ago
Unstoppable Collaboration: D.C.’s Citi Open and Silicon Valley Classic Unite to Propel Women’s Tennis to New Heights
-
Art /Entertainment3 years ago
Embracing Renewal: Sizdabedar Celebrations Unite Iranians in New York’s Eisenhower Park
-
Finance3 years ago
The Benefits of Starting a Side Hustle for Financial Freedom