Technology
How to Speak to Someone at Norton USA Contact Number

Introduction
Norton has built its reputation as one of the leading names in cybersecurity, offering advanced antivirus software, VPN services, and identity protection tools. Millions of users across the United States trust Norton to safeguard their personal and professional data from threats such as malware, phishing, and ransomware. While the software generally runs smoothly, users occasionally face issues that require professional support. These issues may include installation failures, subscription renewal difficulties, account login errors, or technical glitches that impact performance. In such cases, speaking to a live Norton support agent via USA contact numbers becomes essential. This guide will walk you through the entire process in detail, from preparation before the call to what you can expect during the conversation, ensuring that your support request is handled efficiently and effectively.

Click Here For Norton Helpline
Why Speaking to a Norton Support Agent Is Important
Although Norton offers an extensive knowledge base, self-help articles, and community forums, these resources are not always enough for urgent or complex issues. A live support agent can provide:
- Immediate solutions tailored to your device and issue.
- Assistance with billing or subscription queries that cannot be resolved online.
- Step-by-step troubleshooting for errors or technical malfunctions.
- Security checks if you suspect malware or phishing attempts.
- Guidance for account recovery or login issues.
For users who want direct answers and peace of mind, contacting a live agent is the most reliable option.
Preparing Before Calling Norton USA Contact Numbers
Preparation plays a key role in ensuring your conversation with Norton support is productive. Before you call, make sure you have the following details ready:
- The email address linked to your Norton account.
- Your Norton product name, such as Norton 360, Norton Antivirus Plus, or Norton Secure VPN.
- The operating system you are using, whether Windows, macOS, iOS, or Android.
- Subscription information, such as renewal dates or payment method.
- Any error codes or messages you have encountered.
Having this information readily available saves time, prevents confusion, and allows the support agent to focus directly on resolving your issue.
Navigating the Automated System
When you call Norton’s USA support numbers, you will first encounter an automated voice response system. This system is designed to categorize your request and transfer your call to the appropriate department. The menu typically offers options for technical support, billing and subscription issues, or account recovery. Listen carefully to the prompts and select the option most relevant to your concern. If you are unsure, choose the closest option or wait for an opportunity to be transferred to a live agent.
The automated system may also request your Norton account details for verification. Having your registered email and subscription information on hand ensures the process is smooth and avoids unnecessary delays.
Speaking to a Live Norton Support Agent
Once connected to a live agent, be clear and concise about your issue. Start by describing the problem, such as when it began, what error messages appear, and what troubleshooting steps you have already attempted. For example, if your Norton software is failing to update, let the agent know about the error codes displayed and any restart attempts you made.
Support agents are trained to provide step-by-step guidance. They may walk you through reinstalling software, resetting your password, adjusting settings, or running a complete system scan. If the issue is more technical, the agent may request permission to perform secure remote access on your device. This allows them to directly resolve the issue, although it is optional and requires your approval.
Common Issues Norton Support Can Help With
Norton support agents handle a wide range of problems, including:
- Trouble downloading or installing Norton products.
- Failed subscription renewals or billing discrepancies.
- Difficulty logging in or recovering Norton account details.
- Software updates failing or causing performance issues.
- Suspected malware that Norton has not detected or removed.
- Configuration of VPN, parental controls, or multi-device security.
No matter the issue, speaking to a Norton support agent ensures you receive expert assistance suited to your specific case.
Keeping Records of Your Support Call
During your conversation with Norton support, always take notes. Write down the name of the representative, a case number if provided, and the key troubleshooting steps suggested. This documentation is helpful if you need to call again, as it avoids repeating the same details and ensures continuity in your support request.
Alternative Support Options
If phone support is not immediately available or if you prefer not to wait on hold, Norton also provides alternative methods of assistance. These include live chat with support agents, detailed help articles that explain troubleshooting processes, and community forums where other users share experiences and solutions. However, while these alternatives can be useful, direct phone support often remains the fastest way to resolve urgent or complicated problems.
Tips for an Effective Support Call
To ensure the best results when contacting Norton support in the USA, keep the following tips in mind:
- Call from a quiet place where you can focus on the conversation without distractions.
- Ensure your device is connected to the internet and available for troubleshooting.
- Follow the agent’s instructions carefully and ask for clarification if something is unclear.
- Be patient, as resolving certain technical issues may take time.
By following these tips, you improve your chances of a smooth and efficient support experience.
Final Thoughts
Norton provides advanced protection for your devices and online presence, but occasional technical, subscription, or account issues may require professional assistance. Speaking to a live Norton support agent through USA contact numbers gives you immediate access to expert guidance tailored to your specific needs. With proper preparation, clear communication, and an understanding of the process, you can ensure your support call is productive and results in a quick resolution. Whether you need help installing software, troubleshooting performance problems, or managing your subscription, Norton’s support team is ready to assist. By keeping track of your case details and following best practices for support calls, you can enjoy peace of mind knowing that your cybersecurity provider is always available to help.
Cars
Luxury Car Seats: The Pinnacle of Comfort and Engineering

Seats play a defining role in every luxury car. They shape the driving experience, influence posture, and determine long-term comfort. While engines provide motion and materials define appearance, seats create the most direct connection between the vehicle and its occupants. For this reason, luxury car manufacturers treat seat design as a blend of science, craftsmanship, and advanced engineering.
Unlike standard automotive seating, luxury car seats focus on ergonomics, adaptability, and sensory comfort. Every curve, stitch, and mechanism serves a purpose. This article explores how luxury car seats are formed, how they work, and why they represent one of the most complex components in premium vehicles.
The Formation of Luxury Car Seats
The formation of a luxury car seat begins at the design stage. Engineers first analyze human anatomy, driving posture, and pressure distribution. They then translate these findings into seat geometry.
Manufacturers build seat frames using high-strength steel or lightweight aluminum. These materials provide rigidity while allowing controlled flexibility. Once the frame is complete, engineers add foam layers with varying densities. Firmer foam supports posture, while softer foam enhances comfort.
Brands such as Mercedes-Benz invest years in seat research. Their development process ensures that seats remain supportive during long journeys without causing fatigue.

Advanced Engineering Behind Seat Structure
Luxury car seat engineering goes far beyond cushioning. Engineers design multi-layered structures that adapt to body movement. These structures absorb road vibrations while maintaining stability.
Many luxury seats include reinforced side bolsters. These bolsters hold occupants securely during cornering. At the same time, they remain unobtrusive during relaxed driving.
In vehicles like the BMW 7 Series, seat engineering balances firmness and softness. This balance allows the seat to respond dynamically to both driver input and road conditions.
How Luxury Car Seats Work
Luxury car seats rely on mechanical, electrical, and software systems working together. Electric motors control adjustments such as height, tilt, lumbar support, and headrest position. Memory systems store personalized seating preferences.
Sensors embedded within the seat detect body position and movement. Based on this data, the seat adapts support levels automatically. This responsiveness improves comfort during extended drives.
Additionally, advanced suspension seats isolate occupants from road imperfections. As a result, passengers experience smoother rides, even on uneven surfaces.
Performance Contribution of Luxury Seats
Seat performance directly affects driving precision. Proper seating position improves steering control, braking response, and overall safety.
Luxury car seats keep the driver stable during acceleration and cornering. This stability reduces muscle strain and enhances focus. In high-end sedans and grand tourers, seats also contribute to passenger comfort at higher speeds.
For example, the Audi A8 integrates performance-oriented seat contours with comfort-focused padding. This approach supports both dynamic driving and relaxed travel.
Materials Used in Luxury Car Seats
Material selection defines the tactile experience of luxury seats. High-quality leather remains the most popular choice. However, manufacturers use different grades and treatments to achieve softness, durability, and breathability.
Some luxury brands also use premium fabrics and microfiber materials. These options offer excellent temperature regulation and wear resistance. Stitching patterns further enhance visual appeal while reinforcing structural integrity.
In ultra-premium vehicles from Rolls-Royce, artisans hand-stitch seats using carefully selected hides. This craftsmanship ensures uniform texture and long-lasting elegance.
Climate Control and Seat Comfort Technology
Modern luxury car seats actively manage temperature. Heating systems warm seats during cold conditions, while ventilation systems circulate air during warm weather.
Ventilated seats use perforated materials and internal fans. These components prevent heat buildup and moisture retention. Consequently, occupants remain comfortable in all climates.
Some models even include massage functions. These systems use air bladders or rollers to stimulate muscles. Over time, massage features reduce fatigue and improve circulation.
Ergonomics and Long-Distance Comfort
Ergonomics represent a core principle in luxury seat design. Engineers shape seats to support the spine’s natural curvature. Adjustable lumbar support ensures proper alignment.
Headrests also receive special attention. Active headrests adjust position during sudden stops to reduce neck strain. This feature enhances safety without compromising comfort.
Luxury car seats allow drivers to maintain a relaxed posture over long distances. This ergonomic advantage differentiates luxury vehicles from conventional cars.
Noise Reduction and Vibration Control
Luxury seats also contribute to cabin quietness. Specialized foam and padding absorb vibrations transmitted from the chassis. This absorption reduces road noise felt through the body.
Seat mounts include isolation elements that separate the seat from the vehicle floor. These elements dampen movement and vibration. As a result, the cabin feels calm even at highway speeds.
This refinement supports the overall luxury driving experience.
Customization and Personalization Options
Customization plays a major role in luxury seating. Buyers can choose seat colors, stitching patterns, and materials. Some brands even offer bespoke embroidery.
Seat configuration options include executive rear seating with extended leg rests and reclining functions. In vehicles like the Lexus LS, rear seats provide near-lounge comfort.
Personalization allows owners to align the interior with their preferences. This exclusivity strengthens emotional connection to the vehicle.
Safety Integration in Luxury Seats
Safety features integrate seamlessly into luxury car seats. Airbags deploy from seat sides to protect occupants during side impacts. Seatbelt pre-tensioners work in coordination with seat sensors.
Child seat anchoring systems blend into the design without affecting aesthetics. Meanwhile, structural reinforcement protects occupants during collisions.
Luxury seats combine safety and comfort without visible compromise.
Sustainability in Seat Design
Sustainability now influences luxury seat production. Manufacturers increasingly use eco-friendly leather processing and recycled materials.
Plant-based foams and vegan leather alternatives reduce environmental impact. These materials meet strict durability standards while supporting sustainability goals.
This shift reflects changing consumer expectations within the luxury car market.
The Future of Luxury Car Seating
Future luxury seats will become more intelligent and adaptive. Artificial intelligence may adjust seating posture in real time based on fatigue levels.
Biometric sensors could monitor heart rate and stress. Seats may then activate massage or climate features automatically.
Despite technological growth, craftsmanship will remain essential. Comfort, elegance, and human-centered design will continue to guide innovation.
Conclusion
Seats represent one of the most important components in a luxury car. From formation and engineering to performance and personalization, luxury seats reflect thoughtful design and advanced technology. They support the body, enhance safety, and elevate comfort across every journey.
As luxury cars evolve, seats will continue to define the driving experience. Through innovation and craftsmanship, they transform travel into a refined and effortless pleasure.
Beauty Fitness
Transform Your Skin with Micro Needling in Tomball

Living in Tomball, we know just how much we cherish our sunny days and outdoor adventures. However, the Texas heat, humidity, and intense UV exposure can take a toll on our skin. Whether it’s persistent acne scars, sun spots, or the fine lines that seem to deepen every year, we all know how difficult it can be to maintain that youthful, glowing complexion.
At Enfield Royal Med Spa Tomball, we believe in a holistic approach to skincare — healing from within. That’s why we’re big fans of Micro needling, a gold-standard treatment that’s transforming the skin of many Tomball locals.
What is Micro needling?
Micro needling, or Collagen Induction Therapy, is a minimally invasive procedure that uses a specialized device to create thousands of tiny, microscopic channels in your skin’s surface.
Although the idea of tiny needles poking your skin might sound intimidating, don’t worry! It’s actually a gentle and highly effective process. These micro-injuries stimulate your body’s natural healing response, triggering the production of new collagen and elastin — essential building blocks for firm, smooth, and youthful-looking skin.

Why Tomball Locals Love Micro needling: 5 Key Benefits
If you’re still undecided about whether Micro needling is the right fit for you, here’s why this treatment is a fan favorite in Tomball:
1. The Ultimate Multi-Tasker
One of the best things about Micro needling is its versatility. Unlike treatments that only address one skin concern at a time, Micro needling tackles multiple issues in a single session. With just one treatment, we can improve:
- Fine lines and deep wrinkles
- Acne scars and pockmarks
- Enlarged pores
- Uneven skin texture and tone
- Sun damage and hyperpigmentation
It’s like a skin reset button that gives you a more youthful, even complexion from head to toe.
2. Natural, Effortless Results
One of the biggest advantages of Micro needling is that it works with your body’s own collagen production. That means no artificial-looking changes — just you, looking fresher, more rested, and glowing. Unlike Botox or fillers that can give a “frozen” appearance, Micro needling enhances your natural beauty, leaving you looking like the best version of yourself.
3. Minimal Downtime
Unlike other aggressive treatments like chemical peels or lasers, Micro needling offers a low-impact recovery time. Most clients experience redness similar to a mild sunburn for 24-48 hours, after which they’re ready to go about their normal routine — and even wear makeup! There’s no peeling, flaking, or discomfort that might make you want to hide at home. You’ll be glowing and ready to face the world in no time.
4. Boosts the Power of Your Skincare
Micro needling doesn’t just improve your skin; it also enhances the effectiveness of the skincare products you already use. After the treatment, your skin is primed to absorb serums and moisturizers up to 300% deeper than usual, allowing those pricey products to work even harder for you.
5. Safe for All Skin Types and Tones
If you’ve ever been hesitant to try laser treatments due to concerns about your skin tone, you’ll be happy to know that Micro needling is a great option for almost everyone. Unlike thermal treatments like lasers, which can be risky for darker skin tones, Micro needling uses mechanical action, making it safe and effective for all skin types. Whether your skin is fair or deep-toned, you can enjoy the benefits of a smoother, healthier complexion.
What to Expect at Enfield Royal Med Spa Tomball
We understand that trying a new treatment can be nerve-wracking, but rest assured that your comfort is our top priority. Here’s a look at what a typical Micro needling session at our spa involves:
- Numbing: To ensure the treatment is comfortable, we start by applying a high-quality numbing cream to the treatment area. Most clients only feel a light vibration during the process.
- The Treatment: A trained provider will gently glide the micro needling device over your skin. We can adjust the depth of the needles to target specific concerns like deep acne scars or fine lines around the eyes. The procedure usually takes 30-60 minutes, depending on the area treated.
- Soothe: Once the treatment is complete, we’ll apply soothing serums or a cooling mask to help calm your skin and kickstart the healing process.
Ready to Glow?
If you’ve been dealing with dull texture, stubborn scars, or uneven skin tone, Micro needling could be just the treatment you need to refresh your complexion.
At Enfield Royal Med Spa in Tomball, we specialize in creating personalized skincare plans tailored to your unique needs. Whether you want to smooth out fine lines, minimize sun spots, or rejuvenate your skin’s texture, we’re here to help you look and feel your best.
Stop by for a consultation today, and let’s discuss how Micro needling can help you achieve healthy, glowing skin that’s ready for anything.
Care
Gas Furnace Heating and Its Impact on Indoor Air Quality
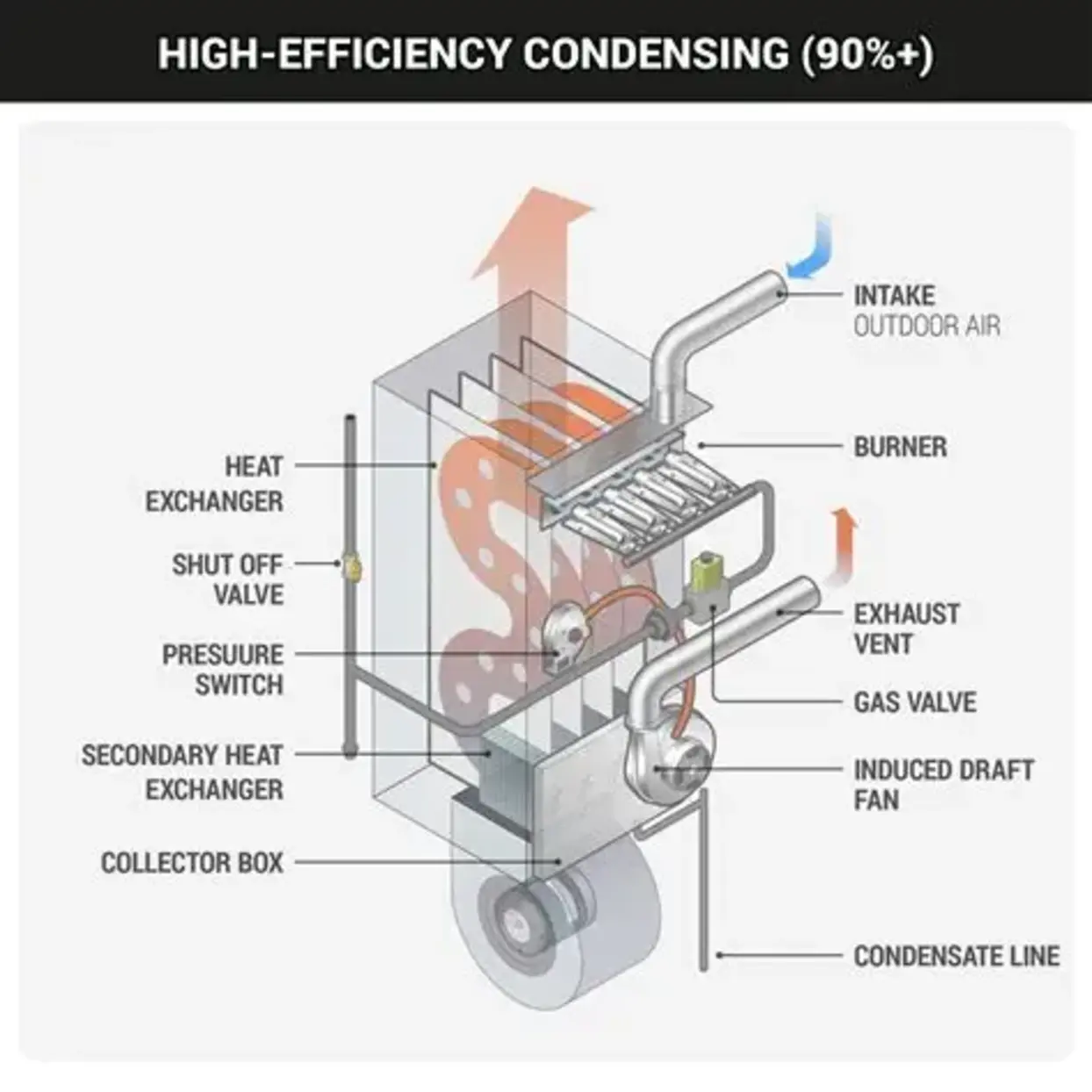
Indoor Air Quality (IAQ) has become a defining metric of building performance. Across residential, commercial, and light industrial spaces, occupants expect heating systems not only to deliver thermal comfort but also to support a healthy indoor environment. Gas furnace heating remains one of the most widely adopted solutions globally due to its reliability, efficiency, and cost-effectiveness. However, its impact on Indoor Air Quality depends heavily on system design, installation, and maintenance.
This article examines how gas furnaces influence Indoor Air Quality and outlines practical strategies to optimize performance while protecting occupant health.
Understanding How Gas Furnaces Operate
A gas furnace generates heat by burning natural gas or propane in a sealed combustion chamber. The combustion gases pass through a heat exchanger, transferring warmth to circulating air, which is then distributed throughout the building via ductwork. Modern high-efficiency furnaces use sealed combustion and direct venting systems to isolate combustion air from indoor air.
This distinction is critical. Older, non-sealed systems may draw combustion air from inside the building, which can negatively affect Indoor Air Quality if ventilation is inadequate. High-efficiency sealed combustion systems, by contrast, significantly reduce indoor contamination risk.

Key Indoor Air Quality Concerns with Gas Furnace Heating
1. Combustion Byproducts
Incomplete combustion can generate pollutants such as carbon monoxide (CO), nitrogen dioxide (NO₂), and trace particulate matter. Carbon monoxide is particularly dangerous due to its colorless and odorless nature.
Properly installed and tuned gas furnaces minimize these risks. Modern units incorporate advanced burner design, flame sensors, and safety shutoff controls to ensure stable combustion. Routine inspections and combustion analysis remain essential to maintaining Indoor Air Quality standards.
2. Particulate Circulation Through Ductwork
Gas furnaces rely on forced-air systems. If ductwork is poorly sealed or filtration is inadequate, dust, allergens, and debris can circulate through indoor spaces.
High-performance filtration systems play a central role here. MERV-rated filters capture varying particle sizes, and advanced systems can integrate HEPA filtration for enhanced Indoor Air Quality in sensitive environments such as healthcare or educational facilities.
3. Humidity Imbalance
Gas furnaces produce dry heat. During winter months, prolonged operation can reduce indoor relative humidity levels below recommended thresholds (30–50%). Low humidity can contribute to respiratory irritation, dry skin, static electricity, and increased viral transmission risk.
Integrated humidification solutions counteract this effect and help stabilize Indoor Air Quality.
Positive Contributions of Modern Gas Furnaces to Indoor Air Quality
While risks exist, modern gas furnace systems are engineered to actively support healthier indoor environments.
Sealed Combustion Technology
Sealed combustion furnaces isolate the combustion process from indoor air, drawing intake air from outside and venting exhaust externally. This prevents back drafting and reduces pollutant exposure. For new installations and retrofits, sealed systems are now the industry standard in high-performance buildings.
Advanced Filtration Integration
Today’s gas furnace platforms are designed to accommodate:
- High-efficiency media filters
- Electronic air cleaners
- UV germicidal lamps
- Bipolar ionization systems
When integrated correctly, these solutions significantly enhance Indoor Air Quality by targeting airborne particulates, microbial growth, and volatile organic compounds (VOCs).
Variable-Speed Blower Motors
Variable-speed ECM blower motors maintain consistent airflow and enable continuous low-speed circulation. This improves air mixing, reduces temperature stratification, and increases the effectiveness of filtration systems—ultimately contributing to better Indoor Air Quality across the entire space.
Installation Quality: The Deciding Factor
Even the most advanced furnace will fail to deliver optimal Indoor Air Quality if improperly installed.
Key installation considerations include:
- Correct furnace sizing based on load calculations
- Proper venting configuration
- Airtight duct sealing
- Balanced airflow distribution
- Adequate fresh air ventilation
Oversized systems short-cycle, reducing filtration time and humidity control. Undersized systems overwork and may stress components. Professional commissioning ensures that combustion efficiency and airflow performance align with Indoor Air Quality objectives.
Maintenance and Monitoring Best Practices
Maintaining Indoor Air Quality with gas furnace heating requires proactive care.
1. Regular Filter Replacement
Filters should be replaced according to manufacturer guidelines, typically every 1–3 months depending on usage and environmental conditions.
2. Annual Professional Inspection
Certified technicians should inspect burners, heat exchangers, venting systems, and safety controls annually to prevent combustion-related air quality issues.
3. Carbon Monoxide Detection
CO detectors should be installed on every occupied level. This is a non-negotiable safety requirement in gas-heated environments.
4. Duct Cleaning and Sealing
Periodic duct inspections prevent particulate buildup and leakage, supporting consistent Indoor Air Quality performance.
Integrating Gas Furnace Systems with IAQ-Focused Solutions
Forward-looking manufacturers are engineering gas furnace platforms that serve as central hubs for Indoor Air Quality management. These integrated systems may include:
- Smart thermostats with air quality monitoring
- Humidity sensors and control modules
- Ventilation energy recovery units (ERVs/HRVs)
- Real-time filter status alerts
By combining heating and air purification into a unified system, building owners can manage comfort and Indoor Air Quality simultaneously through centralized controls.
Global Considerations
In colder regions across North America, Europe, and parts of Asia, gas furnace heating remains a cornerstone of building infrastructure. However, regional air quality standards, building codes, and fuel availability vary widely.
Manufacturers serving a global market must design systems that:
- Meet local emissions regulations
- Accommodate diverse climate conditions
- Support both natural gas and propane options
- Integrate with varying ventilation standards
Global compliance and adaptability are now essential components of product development in the heating sector.
The Bottom Line
Gas furnace heating, when properly designed, installed, and maintained, does not inherently compromise Indoor Air Quality. On the contrary, modern high-efficiency systems can enhance IAQ through sealed combustion, advanced filtration compatibility, and integrated humidity management.
The true impact depends on system quality and lifecycle care. Building owners, facility managers, and HVAC professionals should prioritize equipment that supports comprehensive Indoor Air Quality strategies rather than viewing heating as an isolated function.
As Indoor Air Quality continues to gain global attention, gas furnace technology is evolving beyond simple heat delivery. The future lies in integrated, intelligent systems that provide comfort, safety, and cleaner indoor environments—without compromise.
-
Business3 years ago
Cybersecurity Consulting Company SequelNet Provides Critical IT Support Services to Medical Billing Firm, Medical Optimum
-
Business3 years ago
Team Communication Software Transforms Operations at Finance Innovate
-
Business3 years ago
Project Management Tool Transforms Long Island Business
-
Business2 years ago
How Alleviate Poverty Utilized IPPBX’s All-in-One Solution to Transform Lives in New York City
-
health3 years ago
Breast Cancer: The Imperative Role of Mammograms in Screening and Early Detection
-
Sports3 years ago
Unstoppable Collaboration: D.C.’s Citi Open and Silicon Valley Classic Unite to Propel Women’s Tennis to New Heights
-
Art /Entertainment3 years ago
Embracing Renewal: Sizdabedar Celebrations Unite Iranians in New York’s Eisenhower Park
-
Finance3 years ago
The Benefits of Starting a Side Hustle for Financial Freedom






































