Internet and Telecom
How Malicious Chrome Extensions Threaten Businesses

Introduction: Malicious Chrome Extensions
Imagine a burglar finding a hidden passage into a seemingly impregnable fortress. That’s precisely what malicious Chrome extensions are doing to your business network, infiltrating your defenses and putting your valuable data at risk. While the Chrome Web Store is considered a trusted source for browser extensions, it’s not impervious to infiltration, and cybercriminals are capitalizing on this vulnerability to compromise business networks worldwide.
The Perceived Safety of the Chrome Web Store
The Chrome Web Store is, without a doubt, one of the safer places to acquire extensions for your Google Chrome browser. Google takes extensive measures to prevent malware from infiltrating users’ devices. They restrict the installation of extensions to either the Chrome Web Store or under strict conditions, coupled with vigilant monitoring for suspicious activities.
Despite these efforts, no platform can guarantee 100 percent safety. Some malicious extensions do manage to slip through the cracks, posing a considerable threat to users. However, it’s essential to emphasize that the Chrome Web Store remains significantly safer than downloading random files from the vast, unregulated expanse of the internet.
From PC-Level to Network-Level Threats
Traditionally, most Chrome extension malware targeted individual PCs, often installing keyloggers or monitoring users’ browser activities. The consequences, while concerning, were localized to the specific machine. However, a new breed of Chrome extension malware is emerging, one that seeks not just to infect one PC but to establish a foothold within an organization’s network.
This evolution marks a significant departure from the norm in the cybersecurity landscape. Now, a single individual within a larger network can unwittingly endanger the entire organization merely by downloading a seemingly harmless extension.
Evidence from ThreatPost
Evidence of this alarming development comes from ThreatPost, a reputable source for tracking security threats across the internet. In a recent report, ThreatPost uncovered and subsequently reported 106 malicious extensions to Google, urging their removal.
What’s particularly worrisome about these extensions is not just the data theft they conducted but the backdoor they created. This backdoor provided cybercriminals with an entry point into victims’ networks, paving the way for extensive spying and potential data breaches.
How Malware Developers Evade Detection
Google’s robust security checks pose the most substantial obstacle for extension malware. If Google detects malicious activity, it can trigger alarms and prompt action against the offending extension. However, if the malware manages to pass these checks, it can potentially reach millions of unsuspecting users. After all, users tend to trust Chrome Web Store apps, making them more likely to download and install these extensions.

Image by https://www.makeuseof.com/
One particular strain of malware adopted a clever tactic to circumvent Google’s scrutiny. Instead of directly linking to a malicious website, the malware led users to a “morphing website.” When a connection was established, this website would perform a check to identify the source. If it detected a non-human system, like Google’s automated scans, it displayed an innocent landing page to evade detection.
However, if the connection originated from a typical company or consumer ISP, signaling human interaction, the website redirected users to the “real” website containing the malware payload.
The Alarming Spread of Malicious Extensions
The effectiveness of this method is evident from the shocking numbers: 106 malicious Chrome extensions managed to evade virus checkers, accumulating a staggering 32 million downloads. The malware cleverly disguised itself as tools that identify malicious websites or convert file types—both extensions people commonly install without suspicion.
These extensions established footholds in a wide range of industries, including finance, healthcare, and even government organizations. This broad infiltration suggests a coordinated effort to gain a foothold in various sectors, raising concerns about global surveillance attempts by hackers.
How to Check for and Guard Against Infected Extensions
If you suspect you might have inadvertently downloaded an infected extension, there’s a way to check. Open your extensions page by typing “chrome://extensions/” into your address bar. Locate the extension you suspect, and note the ID listed beneath it.
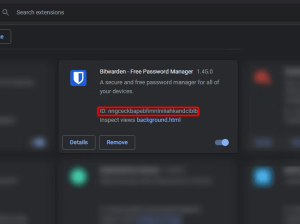
Image by https://www.makeuseof.com/
To confirm its status, compare this ID to the list of known malicious Chrome extensions. Given the complex nature of extension IDs, use the CTRL+F function to quickly search for a match within the list.
| Topic | Key Points |
|---|---|
| Introduction | – Malicious Chrome extensions threaten business networks |
| The Chrome Web Store’s Safety | – Chrome Web Store is safer but not impervious |
| A Single Chrome Extension’s Impact | – Malware traditionally targeted PCs |
| – New extensions seek to infiltrate networks | |
| Real-World Examples of Chrome Malware | – ThreatPost report on 106 malicious extensions |
| How Malware Evades Detection | – Google’s security checks pose a hurdle |
| – Malware uses “morphing websites” to evade detection | |
| The Alarming Spread of Malicious Extensions | – 32 million downloads across industries |
| Identifying and Protecting Against Malware | – Checking for infected extensions |
| Securing Your Chrome Extensions | – Prioritize trusted, well-established extensions |
| – Exercise caution and vigilance |
This table provides a concise and visually appealing summary of the article’s key points, making it easier for readers to grasp the main concepts discussed in the article.
Preventing Future Threats in the Extension Space
This growing threat of Chrome extension malware serves as an early warning for businesses and individuals alike. As we increasingly rely on browser-based office tools like Google Docs and Zoom, the demand for extensions to enhance productivity rises. Unfortunately, malware developers are keenly aware of this trend and are exploiting it to create viruses disguised as helpful extensions.
Traditionally, low download counts and suspicious 5-star reviews might have been warning signs of a malicious extension. However, as demonstrated by the 32 million downloads of these deceptive extensions, download numbers are no longer a reliable indicator of safety.
Conclusion
To protect yourself, stick to well-established, trusted extensions with a history of positive reviews and recommendations. Extensions that have been around for years and have garnered significant user trust are unlikely to have malicious intent. For example, all our recommendations for Chrome extensions that enhance your browsing experience have been carefully vetted for safety.
In a world where digital security is paramount, keeping your Chrome extensions clean is a crucial step in safeguarding your business and personal data. It’s easy to assume that every extension on the Chrome Web Store is safe, but as the evidence shows, that’s far from the truth. Exercise caution, prioritize trusted extensions, and stay vigilant to ensure your online experiences remain secure.
Computer Electronic
SBCGlobal Support Guide: Contact Ways and Troubleshooting

SbcGlobal email, originally provided by Southwestern Bell and now managed through AT&T and Yahoo Mail infrastructure, is still used by thousands of people for personal and business communication. However, many users face login errors, password issues, server problems, or configuration challenges. When these problems occur, the first thing most users search for is the SbcGlobal support number to get quick assistance.
In this complete guide, you will learn the safest and most effective ways to contact support, troubleshoot common issues, and protect your account from scams.
Understanding SbcGlobal Email Support
SbcGlobal email accounts are no longer provided as a new service, but existing accounts are still active and supported through AT&T. This indicates that the majority of SbcGlobal email problems are managed by AT&T email support, Yahoo Mail systems, or authorized help centers.
Because of this transition, many users get confused about where to get help and end up landing on unofficial or third-party websites. That is why it is important to understand the right way to find legitimate SbcGlobal support.

Common Issues That Require SbcGlobal Support
Users typically look for the SbcGlobal support number when facing urgent email problems such as:
1. Login and Password Problems
- Forgotten password
- Account locked after multiple login attempts
- Suspicious activity alerts
- Two-step verification issues
2. Email Sending or Receiving Errors
- Emails not delivering
- Messages stuck in outbox
- Missing emails from inbox
- Spam filtering problems
3. Account Security Issues
- Hacked or compromised account
- Unknown emails sent from your account
- Suspicious login notifications
4. Email Configuration Problems
- Setting up SbcGlobal on Outlook or Gmail
- Mobile email setup issues
- IMAP/POP server errors
5. Server and Sync Errors
- Email not syncing across devices
- Slow email loading
- Attachment download problems
If you experience any of these issues, contacting official support is the safest way to resolve them.
How to Contact SbcGlobal Support Number Safely
Before calling any support number, you must ensure it is official and secure. Many fake tech support websites publish random phone numbers to scam users.
Here are the safe ways to contact SbcGlobal support.
Step 1: Visit the Official AT&T Support Website
Since AT&T manages SbcGlobal accounts, the best place to start is the AT&T Help Center. Search for:
- AT&T Mail Support
- Yahoo Mail Support via AT&T
From there, you can access official contact options.
Step 2: Use the Sign-In Help Page
If you cannot access your account:
- Go to the AT&T sign-in page
- Click Forgot Password
- Follow identity verification steps
This process resolves most login issues without needing to call support.
Step 3: Use Live Chat Support
Many email problems can be solved quickly through chat support. Live chat is often faster than calling and helps you avoid long waiting times.
Step 4: Contact Phone Support (If Required)
If your issue is urgent or complex, you may need phone support. Always verify the number from the official website before calling.
Information to Keep Ready Before Calling Support
To speed up the support process, keep the following information ready:
- Your SbcGlobal email address
- Account recovery phone number or backup email
- Details about the issue
- Error messages or screenshots
- Device and email app you are using
Providing accurate details helps support agents diagnose the problem quickly.
How to Set Up SbcGlobal Email on Devices
Many users contact support for email setup help. You can often fix this yourself using the correct server settings.
IMAP Settings
- Incoming server: imap.mail.att.net
- Port: 993
- Security: SSL
SMTP Settings
- Outgoing server: smtp.mail.att.net
- Port: 465 or 587
- Security: SSL/TLS
Using the correct settings ensures smooth email syncing across devices.
Tips to Recover a Locked SbcGlobal Account
If your account is locked, try these steps before contacting support:
- Reset your password using the recovery page
- Clear browser cache and cookies
- Try logging in from a different device
- Disable VPN if you are using one
- Wait 24 hours and try again
If the issue persists, contacting the SbcGlobal support number may be necessary.
How to Avoid Fake Support Numbers and Scams
Many fake websites target users searching for email support. Protect yourself with these tips:
- Never trust numbers listed on random blogs
- Avoid websites asking for remote access immediately
- Do not share passwords with anyone
- Verify the website URL before calling
- Use only official support channels
Legitimate support agents will never ask for your password.
Prevent Future SbcGlobal Email Problems
You can reduce future issues by following best practices:
Enable Account Security
- Use a strong password
- Enable two-factor authentication
- Update recovery options regularly
Maintain Email Storage
- Delete spam and old emails
- Empty trash and spam folders
- Archive important emails
Keep Apps Updated
- Update email apps regularly
- Use the latest browser version
- Install security updates
When Should You Contact SbcGlobal Support?
You should contact support if:
- Account recovery fails
- Security breach is suspected
- Email stops working completely
- Server errors continue for days
Professional assistance ensures your account remains secure and functional.
Final Thoughts
SbcGlobal email remains a reliable communication platform, but occasional technical issues are normal. When problems arise, searching for the correct SbcGlobal support number is often the first step toward a solution. However, always make sure you use official channels to avoid scams and protect your personal information.
By following the steps in this guide, you can troubleshoot most issues yourself and know exactly when to contact support for professional help. With the right approach, your SbcGlobal email account can continue running smoothly and securely for years to come.
Digital Development
7 Benefits of Hiring an SEO Agency in the USA

Introduction
In today’s digital age, every business aims to improve its visibility online and rank higher on Google. Nonetheless, accomplishing this is not as straightforward as it appears. Google’s algorithms are constantly changing, competition is fierce, and customers increasingly turn to search engines before making any purchase decisions.
This is why many businesses prefer to collaborate with an SEO Agency in the USA rather than managing SEO internally. Whether you’re running a startup or a large enterprise, hiring an expert SEO partner can significantly improve your online visibility, website traffic, and ultimately, revenue.
In this blog post, we’ll dive into the seven major benefits of hiring an SEO Agency in the USA, current SEO trends, insights across different states, and how companies like Team Tweaks Technology can support your business growth.
Why Businesses Need an SEO Agency in the USA
Search engines drive more than 53% of global website traffic (BrightEdge, 2024), and with Google processing over 8.5 billion searches daily, the online competition is immense.
To stand out, businesses must properly optimize their websites. An SEO Agency in the USA brings a deep understanding of market trends, local competition, and constant algorithm updates. Instead of making random guesses, you gain a data-driven, proven strategy that aligns with your goals.
1. Access to Industry Experts and Advanced Tools
An experienced SEO Agency in the USA provides access to a team of skilled professionals who specialize in various SEO fields, including:
- Technical SEO
- On-page optimization
- Content marketing
- Link building
- Local SEO
- E-commerce SEO
Additionally, agencies utilize expensive, premium tools such as:
- Google Search Console
- SEMrush
- Ahrefs
- Screaming Frog
- Surfer SEO
While these tools can be costly for individual businesses, partnering with an agency provides access to them at no additional cost.
Benefit:
You save money while benefiting from expert-level execution, ensuring your SEO strategy is highly effective.
2. Better ROI Compared to In-House SEO
Hiring an in-house SEO team can be expensive. You’ll need to cover:
- Salaries for team members
- Software subscriptions
- Training costs
On the other hand, a professional SEO Agency in the USA provides a full team of specialists with proven strategies, clear reporting, and measurable results at a fraction of the cost.
3. Stay Updated with Google Algorithm Changes
Google’s algorithms change several times each year, and core updates can significantly impact website rankings. Major SEO trends in 2024 and 2025 include:
- Helpful Content Updates
- AI-generated content filtering
- EEAT (Experience, Expertise, Authoritativeness, Trustworthiness) focus
- Spam link penalties
- Mobile-first indexing
A professional SEO Agency in the USA constantly monitors these updates to ensure your website remains compliant and optimized.
4. Strong Local SEO for US-Based Businesses
If your business operates in specific states, such as:
- California
- Texas
- Florida
- New York
- Illinois
- North Carolina
It’s essential to have a strong local SEO strategy. A reliable SEO Agency understands:
- Google Business Profile optimization
- Local citations
- State-specific keywords
- City-based landing pages
- Review management
For example, if your business operates in Texas, optimizing for keywords like “Houston SEO services” or “Dallas marketing agency” is critical for local visibility. Without a tailored local strategy, you risk losing valuable local leads.
5. Scalable Growth with White Label SEO Services
White label SEO services allow agencies to resell SEO services under their own brand while another expert team handles execution. This model benefits smaller marketing agencies by providing:
- SEO white label packages
- White label SEO agency partnerships
- White label SEO reporting
Why It Matters:
- You can offer SEO services without hiring new staff
- You expand services quickly
- You maintain brand identity
- You increase profit margins
This scalable model is expected to grow rapidly in 2025, enabling agencies to serve clients more efficiently.
6. Data-Driven Strategy and Reporting
SEO isn’t based on guesswork; it’s driven by data. A professional SEO Agency in the USA provides detailed reports that track:
- Keyword research
- Competitor analysis
- Monthly traffic reports
- Conversion tracking
- Technical audit reports
Key SEO Metrics to track:
| Metric | Why It Matters |
|---|---|
| Organic Traffic | Measures growth from search engines |
| Keyword Rankings | Shows visibility improvements |
| Bounce Rate | Indicates content quality |
| Conversion Rate | Tracks business results |
| Domain Authority | Reflects website strength |
Detailed reporting ensures that you know exactly how your SEO efforts are performing, making it easier to adjust strategies as needed.
7. Long-Term Brand Authority
Unlike paid ads, SEO helps build long-term authority. A top SEO Company in the USA will help you:
- Create high-quality content
- Earn authoritative backlinks
- Improve user experience
- Build brand trust
Over time, these efforts position your website as a trusted industry leader. As your brand authority grows, so does customer loyalty and conversions.
Current SEO Trends in the USA (2025)
The SEO landscape is evolving, and businesses must keep up to remain competitive. Some key trends include:
- AI-Powered Search: Google is increasingly using AI to understand user intent, so content must be user-focused, helpful, and clear.
- Voice Search Optimization: With more people using voice assistants like Alexa and Siri, businesses need to optimize for long-tail conversational keywords.
- Video SEO Growth: YouTube and short-form videos are ranking higher, meaning businesses are investing more in video content.
- Mobile Optimization: Over 63% of US searches occur on mobile devices, so websites must be fast and mobile-friendly.
- EEAT-Based Content Strategy: Google prioritizes content that demonstrates real experience, expertise, authority, and trust. Implementing this strategy is essential for ranking well.
State-Wise SEO Demand in the USA
SEO competition varies across different states, and your SEO strategy must adapt accordingly. Here’s an overview of SEO demand by state:
| State | SEO Competition Level | Key Industries |
|---|---|---|
| California | Very High | Tech, Startups, E-commerce |
| Texas | High | Energy, Real Estate, Healthcare |
| Florida | Medium-High | Tourism, Local Services |
| New York | Very High | Finance, Media |
| Illinois | Medium | Manufacturing, B2B |
State-specific strategies are essential to optimize for local competition and key industries.
Why Choose Team Tweaks Technology?
If you’re looking for a trusted SEO Agency in the USA, consider Team Tweaks Technology. They offer:
- Complete SEO solutions
- White label SEO services
- Technical SEO audits
- Content marketing
- Link building
- PPC services
- Mobile app development
- Custom web development
What sets them apart?
- Data-driven SEO strategies
- Transparent reporting
- Scalable white label SEO packages
- Dedicated SEO specialists
- Proven results across industries
Whether you’re seeking local SEO or enterprise-level solutions, Team Tweaks Technology provides tailored strategies to meet your needs.
When Should You Hire an SEO Agency in the USA?
Consider hiring an SEO Agency in the USA if:
- Your website traffic is stagnating or declining
- You’re struggling to rank for target keywords
- Your competitors outrank you
- You lack in-house SEO expertise
- You need scalable white label SEO services
- You want long-term organic growth
SEO is a long-term commitment, but with the right partner, results become predictable.
How to Choose the Right SEO Company in the USA
Before selecting an SEO agency, consider:
- Case studies and client reviews
- Reporting transparency
- Clear pricing structure
- Experience in your industry
- Availability of white label SEO services (if needed)
Be cautious of agencies that promise “instant #1 rankings”—SEO is about strategy and consistency, not shortcuts.
Final Thoughts
Hiring an SEO Agency in the USA is a strategic decision that can help propel your business to greater heights. With increasing competition and continuously changing search algorithms, having expert guidance is essential. From local optimization to large-scale enterprise growth and white label services, agencies provide comprehensive support.
If you’re ready to boost your rankings, build long-term brand authority, and achieve sustainable growth, partnering with a professional SEO Company like Team Tweaks Technology can set you on the right path.
Digital Development
Unlocking Success: Essentials of Tailored Mobile App Development

The modern business landscape demands agility, innovation, and a constant willingness to adapt to shifting consumer expectations. Mobile applications have become one of the most powerful tools available to businesses of all sizes, enabling them to connect with customers, optimize workflows, and unlock new revenue streams.
However, not all mobile app development services are created equal. To truly capitalize on the potential of mobile technology, businesses need a partner that understands their unique needs and has the expertise to deliver a customized solution. That is precisely what a top mobile app development company provides — a combination of deep technical knowledge, strategic thinking, and an unwavering focus on results.
Grasping Business Requirements Prior to Coding Anything
The most effective mobile app development services begin not with coding, but with listening. Every business has its own goals, challenges, customer base, and competitive pressures. A development partner that takes the time to understand these nuances is far more likely to deliver an application that creates real value. During the initial discovery phase, experienced developers work closely with stakeholders to gather requirements, identify pain points, and define success metrics.
This consultative approach distinguishes a top mobile app development company from vendors that offer one-size-fits-all solutions. By deeply understanding the business context, developers can make informed decisions about technology choices, feature prioritization, and user experience design that align with strategic objectives rather than purely technical preferences.
Custom Development vs. Off-the-Shelf Solutions
One of the first decisions businesses face when planning a mobile application is whether to opt for custom development or an off-the-shelf product. While pre-built solutions may seem attractive due to their lower upfront costs, they often fall short when it comes to meeting specific business requirements, integrating with existing systems, or differentiating from competitors. Custom development, on the other hand, gives businesses complete control over features, design, and functionality.
Development firms help clients assess these trade-offs objectively and recommend the approach that best suits their needs. In many cases, a hybrid approach is optimal — leveraging existing frameworks and libraries to accelerate development while customizing the application to meet unique business requirements. This pragmatic approach strikes the right balance between cost efficiency and bespoke functionality, ensuring that businesses get maximum value from every dollar invested.
Technology Stacks Suited to Your Business
The technology stack underlying a mobile application has a profound impact on its performance, scalability, and long-term maintainability. Professional developers stay current with the latest technologies and frameworks, enabling them to recommend the best stack for each specific use case. For businesses targeting both iOS and Android platforms simultaneously, cross-platform frameworks such as Flutter and React Native offer significant advantages in terms of development speed and code reusability.
For applications with complex backend requirements — such as real-time data processing, machine learning integration, or high-volume transaction handling — experienced developers will architect robust server-side solutions using scalable cloud platforms and modern API frameworks. Technoyuga brings this level of technical depth to every project, ensuring that the chosen technology stack not only meets current demands but also supports the application’s long-term growth trajectory without requiring costly rewrites.
User-Centric Design as a Business Differentiator
In a marketplace where users have thousands of apps to choose from, design quality is a critical differentiator. An application that is visually appealing, easy to navigate, and responsive to user needs will consistently outperform a technically superior but poorly designed competitor. Professional mobile app development services always include dedicated UX research and UI design phases that place the end user at the center of every design decision, from color palettes and typography to navigation flows and micro-interactions.
Design is not just about aesthetics — it is about creating experiences that guide users toward desired actions, reduce friction, and build brand loyalty. A top mobile app development company will invest in user research, create detailed personas, build interactive prototypes, and conduct usability testing before finalizing the design. This investment pays dividends in the form of higher user adoption rates, better retention, and stronger app store reviews.
Integration With Existing Business Systems
Very few businesses operate in isolation. Most have existing CRM platforms, ERP systems, payment gateways, logistics tools, and marketing automation platforms that must integrate seamlessly with any new mobile application. Experienced developers understand this reality and have deep expertise in building and managing complex API integrations. They design integration architectures that ensure reliable data flow between systems while maintaining performance and security throughout.
The ability to integrate effectively with existing business infrastructure is one of the defining capabilities of a top mobile app development company. It requires not only technical skill but also a thorough understanding of enterprise IT environments and the ability to navigate the complexities that inevitably arise when connecting disparate systems across different vendors and technology generations.
Ensuring Quality Through Rigorous Testing
A mobile application that crashes, loads slowly, or behaves unpredictably will quickly lose users and damage a brand’s reputation. This is why rigorous quality assurance is an indispensable component of any professional mobile app development service. Testing must cover a wide range of scenarios including functional testing, performance testing under load, compatibility testing across devices and operating system versions, security vulnerability scanning, and user acceptance testing.
Professional development teams invest heavily in QA infrastructure and maintain dedicated testing specialists who work in parallel with engineering. This proactive approach to quality catches issues early in the development cycle, dramatically reduces the cost of fixes, and ensures that the application performs reliably from the moment it reaches users’ hands.
Post-Launch Support and Continuous Improvement
Launching a mobile application is not the end of the journey — it is the beginning. User behavior data, performance analytics, and direct feedback will reveal opportunities for improvement and new features that can enhance value over time. A reliable development partner will provide ongoing maintenance and support services that keep the application secure, performant, and aligned with evolving business needs.
Continuous improvement cycles, regular updates, and proactive monitoring are all hallmarks of a development partner genuinely invested in the long-term success of your application. Businesses that maintain this kind of ongoing relationship with their development partner are consistently better positioned to adapt to market changes and capitalize on emerging opportunities.
In summary, mobile app development services tailored to specific business needs deliver far greater value than generic solutions. By partnering with the right development firm that invests in understanding your goals, applies the right technology, designs for users, and supports you long after launch, you set your business up for sustained digital success.
-
Business3 years ago
Cybersecurity Consulting Company SequelNet Provides Critical IT Support Services to Medical Billing Firm, Medical Optimum
-
Business3 years ago
Team Communication Software Transforms Operations at Finance Innovate
-
Business3 years ago
Project Management Tool Transforms Long Island Business
-
Business3 years ago
How Alleviate Poverty Utilized IPPBX’s All-in-One Solution to Transform Lives in New York City
-
health3 years ago
Breast Cancer: The Imperative Role of Mammograms in Screening and Early Detection
-
Sports3 years ago
Unstoppable Collaboration: D.C.’s Citi Open and Silicon Valley Classic Unite to Propel Women’s Tennis to New Heights
-
Art /Entertainment3 years ago
Embracing Renewal: Sizdabedar Celebrations Unite Iranians in New York’s Eisenhower Park
-
Finance3 years ago
The Benefits of Starting a Side Hustle for Financial Freedom































