Technology
Blockchain : What It Is, How It Works, Why It Matters

In today’s digital landscape, the concept of blockchain technology stands out as a revolutionary advancement in data management and security. Originally popularized by cryptocurrencies like Bitcoin, blockchain technology is now recognized for its potential applications across various industries, from finance to healthcare. This article delves into the intricacies of blockchain technology, explaining what it is, how it works, its benefits, challenges, applications, types, and its future significance.
1. Introduction to Blockchain
Blockchain is a decentralized ledger technology that enables the recording of transactions across multiple computers in such a way that the registered transactions cannot be altered retroactively. This technology provides a secure, tamper-proof environment for data management, ensuring that all participants in the network can trust the integrity of the data without needing a central authority.
Each transaction on a blockchain is encapsulated in a block. Once a block is filled with transaction data, it is appended to a chain of previous blocks, forming a secure and chronological record. This decentralized architecture reduces the risk of data breaches and fraud, making blockchain an attractive solution for various applications.
2. How Blockchain Works

Image by Freepik.com
Blockchain technology relies on a network of nodes (computers) that participate in maintaining the ledger. When a transaction occurs, it is broadcasted to all nodes in the network. Here’s a step-by-step breakdown of how blockchain works:
- Transaction Initiation: A user initiates a transaction, which is then transmitted to the network.
- Validation: Nodes in the network validate the transaction using consensus mechanisms, such as proof of work or proof of stake.
- Block Creation: Once validated, the transaction is bundled with others into a new block.
- Appending to Blockchain: The new block is appended to the existing blockchain, creating an immutable record.
- Distribution: The updated blockchain is distributed across all nodes, ensuring that every participant has the latest version of the ledger.
Consensus Mechanisms
Consensus mechanisms are critical to the functioning of blockchain networks, ensuring all participants agree on the validity of transactions before they are added to the blockchain.
- Proof of Work (PoW): In PoW, nodes compete to solve complex mathematical problems. The first node to solve the problem gets the right to add the next block to the blockchain. This process requires substantial computational power and energy, making it secure but environmentally challenging. For example, Bitcoin relies on the PoW mechanism, which has raised concerns about its energy consumption.
- Proof of Stake (PoS): In contrast to PoW, PoS allows participants to validate transactions based on the number of coins they hold. This reduces energy consumption significantly and incentivizes participants to maintain network integrity. Ethereum is transitioning from PoW to PoS to address energy concerns while maintaining security.
3. Benefits of Blockchain
More Security
Blockchain technology offers enhanced security through its use of cryptography and decentralized architecture. Each transaction is encrypted and linked to the previous transaction, making it nearly impossible to alter the data without detection. Additionally, consensus mechanisms like PoW and PoS ensure that only valid transactions are added to the blockchain.
Example: Bitcoin
Bitcoin’s security features have made it a leading cryptocurrency. The PoW mechanism secures the network by requiring miners to solve complex puzzles, making it costly and time-consuming for malicious actors to manipulate transaction data. The more computational power a miner has, the higher their chances of successfully adding a block, ensuring that the network remains secure.
Improved Accuracy
Blockchain’s transparent and immutable ledger minimizes errors that often occur in traditional record-keeping systems. Since all participants can access the same data, discrepancies between different versions of records are virtually eliminated.
Example: Land Registries
Several countries are exploring blockchain for land registries. By recording land ownership on a blockchain, authorities can ensure that property records are accurate and tamper-proof, reducing disputes and fraud related to land ownership.
Higher Efficiency
Blockchain eliminates intermediaries in many processes, streamlining operations and reducing transaction costs. Smart contracts automate processes, enabling transactions to execute automatically when predetermined conditions are met.
Example: Supply Chain Management
In supply chain management, companies like IBM are using blockchain to streamline processes by tracking products from origin to destination. This not only reduces errors but also speeds up transactions and enhances data integrity.
4. Challenges of Blockchain
Despite its numerous benefits, blockchain technology faces several challenges that hinder its widespread adoption.
Transaction Limitations
As blockchain networks grow, they often face bottlenecks in processing transactions. High demand can lead to congestion, resulting in slower transaction times and increased fees.
Example: Ethereum Network Congestion
The Ethereum network has experienced significant congestion during periods of high demand, particularly during Initial Coin Offerings (ICOs) and NFT launches. This congestion leads to higher gas fees and slower transaction confirmations, prompting the need for scalability solutions.
Energy Consumption

Image by Yandex.com
The energy consumption associated with PoW consensus mechanisms raises concerns about environmental sustainability. Critics argue that the carbon footprint of mining activities can negate the benefits of blockchain.
Example: Bitcoin’s Environmental Impact
Bitcoin mining has been criticized for its substantial energy consumption, equivalent to that of some countries. This has led to calls for more sustainable alternatives, such as PoS, which drastically reduce energy usage.
Scalability Issues
Scalability remains a significant hurdle for many blockchain networks. As the number of users and transactions increases, the capacity of the blockchain to process data efficiently is put to the test.
Example: Scalability Solutions
To address scalability issues, various solutions have emerged, including Layer 2 scaling solutions like the Lightning Network for Bitcoin, which enables faster transactions by creating off-chain payment channels.
Regulation Concerns
As blockchain technology evolves, governments are grappling with how to regulate it effectively. The decentralized nature of blockchain presents challenges in enforcing legal frameworks and protecting consumers.
Example: Regulatory Responses
Countries like China have adopted strict regulations on cryptocurrency trading and Initial Coin Offerings (ICOs), while others, like El Salvador, have embraced Bitcoin as legal tender. The inconsistent regulatory landscape creates uncertainty for businesses operating in the blockchain space.
5. Blockchain Applications and Use Cases
Banking
Blockchain technology simplifies banking operations, allowing for faster, cheaper, and more secure transactions. By serving as a single source of truth, blockchain minimizes fraud and enhances trust among participants.
Example: Ripple
Ripple’s blockchain platform enables banks to process cross-border payments quickly and securely, reducing transaction costs and settlement times significantly compared to traditional banking systems.
Smart Contracts
Smart contracts are self-executing contracts with the terms of the agreement directly written into code. These contracts automate and enforce agreements without the need for intermediaries.
Example: Ethereum
Ethereum is the leading platform for smart contracts, enabling developers to create decentralized applications (dApps) that run on its blockchain. These applications range from finance (DeFi) to gaming and supply chain management.
Cybersecurity

Photo by Jefferson Santos on Unsplash
Blockchain technology enhances cybersecurity by providing a decentralized and tamper-proof ledger. This makes it challenging for unauthorized users to alter data or steal sensitive information.
Example: Cybersecurity in Finance
Banks are increasingly adopting blockchain technology to secure their digital assets and protect against fraud. The decentralized nature of blockchain helps safeguard sensitive customer information and reduces the risk of cyberattacks.
Healthcare
In the healthcare sector, blockchain technology ensures the secure and efficient exchange of medical records, improving patient outcomes and reducing administrative overhead.
Example: MedRec
MedRec is a blockchain-based system developed by MIT that allows patients to control access to their medical records. By leveraging blockchain, patients can share their health data securely with healthcare providers and researchers while maintaining privacy.
Logistics
Blockchain enhances supply chain transparency by enabling real-time tracking of goods from origin to destination. This transparency improves efficiency and reduces fraud.
Example: IBM Food Trust
IBM Food Trust is a blockchain-based platform that allows food producers, distributors, and retailers to track food products throughout the supply chain. This transparency helps ensure food safety and reduces the risk of contamination.
NFTs
Non-Fungible Tokens (NFTs) represent ownership of unique digital assets and are secured using blockchain technology. Each NFT is distinct and cannot be exchanged for another on a one-to-one basis.
Example: OpenSea
OpenSea is a popular marketplace for buying, selling, and trading NFTs. The blockchain ensures the authenticity and ownership of each NFT, preventing counterfeiting and enabling artists to receive royalties from future sales.
6. Types of Blockchain
Public Blockchain
Public blockchains are open to anyone, allowing users to join and participate in the network without restrictions. These networks are fully decentralized and rely on consensus mechanisms like PoW or PoS.
Example: Bitcoin
Bitcoin is the most well-known public blockchain. It allows anyone to participate in mining and transaction validation, contributing to its decentralized nature.
Private Blockchain
Private blockchains restrict access to a select group of users. These networks are typically managed by a single organization or consortium, making them suitable for enterprises that require confidentiality and control.
Example: Hyperledger Fabric
Hyperledger Fabric is a permissioned blockchain framework designed for enterprise use. It enables businesses to create private blockchains for their specific applications, allowing for greater control over data access and privacy.
Consortium Blockchain
Consortium blockchains are governed by a group of organizations rather than a single entity. This collaborative approach allows multiple parties to manage the network while maintaining some level of privacy.
Example: R3 Corda
R3 Corda is a consortium blockchain platform specifically designed for the financial services industry. It allows banks and financial institutions to transact securely while preserving confidentiality.
Hybrid Blockchain
Hybrid blockchains combine elements of both public and private networks, allowing organizations to maintain privacy while benefiting from the transparency of a public blockchain.
Example: Dragonchain
Dragonchain is a hybrid blockchain platform that allows businesses to choose which data they want to keep private and which data they want to make public. This flexibility makes it suitable for various applications across industries.
7. Future of Blockchain

Image by Freepik.com
The future of blockchain technology is promising, with ongoing innovations aimed at addressing existing challenges. Key trends shaping the future of blockchain include:
- Interoperability: As multiple blockchain networks emerge, the ability to communicate and share data across different platforms will be essential. Projects like Polkadot and Cosmos are working to create interconnected ecosystems that facilitate seamless data transfer.
- Regulatory Clarity: As governments develop clearer regulations for blockchain and cryptocurrencies, businesses will gain more confidence to invest in and adopt blockchain solutions.
- Decentralized Finance (DeFi): DeFi platforms are gaining popularity, enabling users to lend, borrow, and trade assets without traditional financial intermediaries. This trend will continue to grow as more users seek financial independence.
- Sustainability Initiatives: The blockchain community is increasingly focused on reducing energy consumption and environmental impact. Projects exploring eco-friendly consensus mechanisms, like PoS, will play a crucial role in the technology’s sustainability.
8. Analysis and Comparative Tables
Analysis Table: Benefits vs. Challenges of Blockchain
| Aspect | Benefits | Challenges |
|---|---|---|
| Security | Cryptographically secure permanent records | Vulnerable to attacks if not properly managed |
| Accuracy | Transparent, immutable ledger | Requires consensus, which can be slow |
| Efficiency | Reduced costs and improved processing times | Transaction bottlenecks during high demand |
| Energy Consumption | Alternatives like PoS are being explored | PoW consumes significant energy |
| Regulatory Concerns | Enables new business models and transparency | Legal frameworks still evolving |
Comparative Table: Consensus Mechanisms
| Feature | Proof of Work | Proof of Stake |
|---|---|---|
| Energy Consumption | High (computationally intensive) | Low (energy-efficient) |
| Security | Highly secure, but slower transaction | Secure with faster processing |
| Centralization Risk | Less risk of centralization | Potential for centralization if few hold majority coins |
| Use Case | Bitcoin, Ethereum | Cardano, Polkadot |
Comparative Table: Types of Blockchain
| Type | Access | Governance | Use Cases |
|---|---|---|---|
| Public Blockchain | Open to all | Decentralized | Cryptocurrencies, public records |
| Private Blockchain | Restricted | Centralized or consortium | Enterprise applications, internal processes |
| Consortium Blockchain | Semi-restricted | Group of organizations | Financial services, supply chains |
| Hybrid Blockchain | Mixed | Varies | Flexible enterprise solutions, data privacy |
Examples of Blockchain in Action
- Banking: Ripple’s blockchain facilitates real-time cross-border payments, reducing transaction costs and processing times significantly compared to traditional banking systems.
- Healthcare: MedRec allows patients to maintain control over their medical records while enabling healthcare providers to access verified information quickly and securely.
- Supply Chain: IBM Food Trust improves food safety by allowing participants to track products from farm to table, providing transparency and accountability in the supply chain.
- NFTs: OpenSea has become a leading marketplace for NFTs, enabling artists to monetize their digital creations while ensuring the authenticity of ownership through blockchain.
By understanding blockchain technology’s intricacies and its wide array of applications, stakeholders can better navigate the challenges and opportunities it presents, ultimately driving innovation across multiple sectors. The road ahead for blockchain is filled with possibilities, and its potential to reshape industries and enhance efficiencies is only just beginning to be realized.
Conclusion
Blockchain technology is poised to transform various industries by providing secure, efficient, and transparent solutions for data management. Despite the challenges it faces, ongoing advancements and innovations will drive its adoption and pave the way for new applications. As organizations increasingly recognize the value of blockchain, its potential to reshape the future of business, finance, healthcare, and beyond becomes ever more apparent.
Digital Development
Modern Social Media Management: Building Effective Workflows

A few years ago, many brands posted when someone on the team had time or a sudden idea. That style can work for a short phase, but it does not scale when channels grow, teams expand, and leaders expect clear numbers.
Modern social media management feels closer to a quiet production line: ideas move into drafts, drafts move into a social media posting calendar and that calendar lives inside a shared system.
A good social media management tool sits in the middle of this line. It keeps posts, assets, approvals, and dates in one place. Team members check the same dashboard instead of digging through email chains. Small details like saved templates, tag libraries, and link tracking look simple, but they save time across a month.
The goal is not noise. The goal is a repeatable flow where every post has a reason, a place, and a result that someone can track.

Building a Social Media Posting Calendar That People Can Follow
A social media team often starts with a social media planning calendar on a shared sheet or inside a platform. The calendar turns loose ideas into a clear list of posts by day, channel, and format. It also forces choices: which content types stay weekly, which campaigns deserve more space, and where ad flights fit in.
A strong social media posting calendar usually includes:
- Content pillars, such as education, proof, culture, and offers
- Post slots for each pillar across the week
- Fields for copy, media, links, and target audience
- Notes for platform tweaks, such as hook lines or length
Once the structure feels steady, the team connects it to social media scheduling tools. These tools publish to different channels on set times without manual pushes. For growing brands, that small shift removes late night posting and lets people focus on better ideas, better replies, and better reporting.
Core Tools Behind Modern Social Teams
Even small teams now work with a stack of software, not a single platform. The table below gives a quick snapshot of how different pieces fit together.
Key Social Media Manager Tools (Tabular View)
| Tool Type | Main Use | Why Teams Rely On It |
| Social media management tool | Central hub for posts, assets, comments, and approvals | Keeps work visible and reduces missed tasks |
| Social media scheduling tools | Queue and publish posts across channels | Protects calendars and supports planned campaigns |
| Social media analytics tool | Track reach, clicks, saves, and conversions | Links daily posting to real business numbers |
| Social media reporting dashboards | Turn metrics into simple weekly or monthly summaries | Make results clear for managers and founders |
| Social media listening platforms | Monitor brand mentions, topics, and keywords | Show what audiences say outside brand channels |
| Social media engagement tools | Manage replies, DMs, and comment threads in one inbox | Shorten response time and keep tone consistent |
| Employee advocacy tools | Share pre-approved posts with staff for reshares | Expand organic reach through staff networks |
| Employee advocacy software | Add rules, tracking, and rewards to advocacy programs | Show which staff efforts drive clicks or leads |
In many teams, the social media manager tool combine several rows from this table, which cuts down logins and training. Still, leaders often mix one central tool with a few focused platforms for deep listening or advanced ad work.
Analytics, Reporting, and Real Decisions
Modern teams look at numbers often, but not all numbers carry the same weight. A social media analytics tool should act like a simple control panel. It shows which posts held attention, which topics bring saves or shares, and which channels support core goals such as sign-ups or store visits.
Good analytics setups connect:
- Post-level data (reach, clicks, saves, replies)
- Campaign data (UTM links, landing page performance)
- Channel trends over time (growth, drop, or flat lines)
From there, Social media reporting turns raw data into short stories for leaders. A manager might send a monthly report with three parts: what worked, what failed to move any needle, and what the team will try next. That report might live inside the social media analytics tool or inside a slide deck, but the heart stays the same: numbers linked to clear choices.
The strongest teams use reporting to say “no” as well. When a format drains hours and shows weak results month after month, reports give the proof needed to shift effort toward better work.
Listening, Engagement, and Community Signals
Posting without listening feels flat. Modern social teams use social media listening platforms to track brand mentions, product names, and key phrases across open channels. This listening shows how people talk when the brand is not in the room. It also surfaces small issues early: shipping delays, product bugs, or gaps in support.
At the same time, social media engagement tools give one shared inbox for comments and messages across channels. Instead of jumping between apps, the team sees a single queue. They can tag tricky threads, assign them to support or sales, and track response time.
These two layers together, listening and engagement, keep the brand closer to real users. Content ideas often rise from this space. A repeated question might become a post series. A confused group might lead to a clearer landing page or a short guide.
Social Ads and Employee Voices Working Together
Organic reach still matters, but modern social media management also leans on smart paid support. Social media ad platforms let teams reach new segments, retarget visitors, and test offers without huge budgets. Inside these systems, social media ad management covers tasks like:
- Building audiences from site visitors or past buyers
- Setting budgets and bid rules
- Testing creative versions against each other
- Watching key numbers such as cost per lead or sale
The most advanced setups blend organic posting, paid campaigns, and staff voices. Employee advocacy tools and employee advocacy software give team members ready-made content they can share on their own profiles. Staff remain free to adapt tone a bit, but they start from a safe, approved base.
This approach feels human in the feed. Instead of only brand pages speaking, real people inside the company share launches, wins, and everyday work. With tracking inside the software, leaders can see which shares lead to visits, sign-ups, or new leads.
Final Thoughts: Building a Calm, Modern Social Workflow
Modern social media no longer depends on last-minute posting or one person juggling multiple apps. It works best when teams rely on simple systems, shared calendars, and the right mix of tools that match their size and goals.
A clear social media planning calendar, supported by reliable scheduling and analytics, gives teams space to focus on ideas, testing, and real conversations.
Platforms like Contrank regularly share insights that help brands build structured, sustainable social workflows.
When listening, engagement, reporting, and advocacy tools work together, social channels feel less chaotic and more intentional. Campaigns follow a plan, reports guide decisions, and teams know what to prioritize — without burning out the people behind the work.
Digital Development
Recovering Your Roadrunner Email Account: Steps and Tips
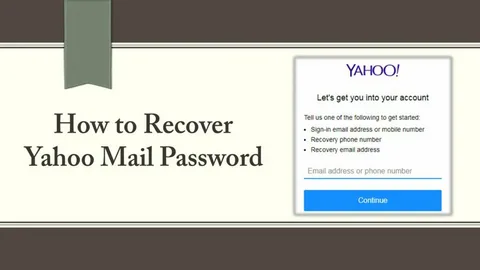
Introduction
Whether you’ve forgotten your password, can’t log in due to a hacked account, or are experiencing login errors, the good news is that you can recover your Roadrunner email account quickly with the right steps.
In this detailed guide, we’ll explain how to restore or recover your Roadrunner account, fix common login problems, and secure your account for the future. For additional assistance, you can also reach out to the Roadrunner email support team.

What Is Roadrunner Email?
Roadrunner was once an email service provided by Roadrunner, which is now managed through Spectrum following the company merger. Roadrunner email addresses (like yourname@roadrunner.com) can now be accessed via the Spectrum Webmail platform.
You can log in and manage your emails through the Spectrum webmail login page or via email clients such as Outlook, Thunderbird, or Apple Mail.
Common Reasons You Can’t Access Your Roadrunner Email
Before starting the recovery process, it’s helpful to understand why your Roadrunner email account isn’t working. Common causes include:
- Incorrect password or username: Simple typos or forgotten passwords are often the main reason users can’t sign in.
- Hacked or compromised account: If you notice suspicious activity or can’t log in with the correct password, your account may have been hacked.
- Browser or cache issues: Outdated browsers or stored cookies can sometimes interfere with login.
- Account inactivity: Long-term inactivity might result in account suspension or deactivation.
- Server problems: Spectrum mail servers occasionally experience temporary outages.
If any of these sound familiar, don’t worry—you can recover your Roadrunner email account using the methods below.
Step-by-Step Guide to Recover Your Roadrunner Email Account
Step 1: Go to the Official Spectrum Login Page
Since Roadrunner is now managed by Spectrum, start by visiting the official Spectrum Webmail login page: https://www.spectrum.net/login
Click on Sign In and enter your Roadrunner email address and password.
Step 2: Use the “Forgot Password” Option
If you’ve forgotten your password or your login credentials aren’t working:
- Click on Forgot Password? below the login fields.
- Enter your Roadrunner email address and follow the on-screen instructions to reset your password.
You’ll typically be asked to verify your identity using one of these methods:
- Recovery email address
- Security questions
- Verification code sent to your registered phone number
If you no longer have access to your recovery email or phone, don’t panic—you can still recover your account by contacting Roadrunner support for manual verification.
Step 3: Reset Your Password and Log In
Step 4: Recover a Hacked or Compromised Roadrunner Account
If you suspect your account has been hacked, take these steps immediately:
- Reset your password right away.
- Review and update your security questions and recovery email.
- Check for unauthorized activity—inspect your sent folder, trash, and email filters.
- Remove any suspicious forwarding addresses or filters.
- Enable two-step verification for added protection.
If you cannot access your account or believe someone changed your recovery details, contact Roadrunner support for assistance.
Recovering Roadrunner Email on Mobile Devices
If you’ve lost access on your phone or tablet:
- Open your mail app’s Account Settings.
- Remove your Roadrunner account if it’s listed.
- Re-add the account using your updated password and correct IMAP/SMTP settings.
- Restart your device and open your inbox to confirm synchronization.
Still can’t access your emails? Call for live support.
Tips to Keep Your Roadrunner Account Secure
Once you regain access, protect it from future issues by following these best practices:
-
Regularly update your password: Change it every few months.
-
Update recovery methods: Ensure your recovery phone number and email are current.
-
Activate two-factor authentication: Provides an additional level of protection
- Avoid suspicious links: Never click links that ask for your password or personal information.
- Update your browser and apps: Security updates help protect your login data.
Final Thoughts
Recovering your Roadrunner email account is straightforward if you follow the right steps. Whether you’ve forgotten your password, been locked out, or need to recover from hacking, you can usually restore access through Spectrum’s official recovery tools—or by contacting Roadrunner support for personal assistance.
Remember to strengthen your security settings and keep your recovery information updated to avoid losing access to your important messages again.
FAQs About Roadrunner Email Account Recovery
1. Can I recover my Roadrunner email if I forgot both my password and recovery email?
Yes, you can contact Roadrunner support for manual verification and account recovery.
2. How long does it take to recover a Roadrunner email account?
If you have recovery options set up, it typically takes a few minutes. Manual recovery via support may take longer depending on verification.
3. Can I recover my emails if my account was deleted?
If the account was recently deactivated, support may be able to restore it. Emails are usually retained for a limited time.
4. Does Spectrum offer two-factor authentication for Roadrunner email?
Yes, enabling two-factor authentication is recommended to enhance your account security.
5. Why am I getting login errors even with the correct password?
Login errors may be caused by browser cache, cookies, or server issues. Clearing your cache or trying another browser can help.
6. Can I access Roadrunner email on my phone?
Yes, you can use the Spectrum Webmail app or set up your account on mobile mail apps using the correct IMAP/SMTP settings.
7. What should I do if I suspect my account is hacked?
Immediately reset your password, update security settings, check for suspicious activity, and contact support if necessary.
8. Are there any fees to recover my Roadrunner email account?
No, account recovery through Spectrum or Roadrunner support is free.
9. Can I forward my Roadrunner emails to another email account?
Yes, once logged in, you can set up forwarding in your account settings.
10. How can I prevent losing access to my Roadrunner email in the future?
Keep your password strong and updated, maintain recovery options, enable two-factor authentication, and avoid suspicious emails or links.
Digital Development
Power of Java Frameworks for Modern Web Development

Java has consistently proven itself as one of the most reliable and versatile programming languages in the technology world. Following the “write once, run anywhere” principle, Java allows developers to write code once and deploy it across multiple platforms without the need for recompilation.
This unique feature has made Java a preferred choice for businesses, startups, and developers worldwide. Beyond its core language features, Java’s vast ecosystem of tools and frameworks has further strengthened its position as a go-to technology for building scalable, secure, and high-performance web applications.
Businesses today are increasingly relying on top professional Java framework services to create applications that are not only interactive but also responsive, efficient, and aligned with modern user expectations.

Whether it’s developing enterprise-grade software, mobile applications, or cloud-based solutions, Java frameworks provide the structure and tools necessary to accelerate development and ensure consistent performance across platforms.
By leveraging the power of these frameworks, businesses can enhance operational efficiency, deliver superior user experiences, and gain a competitive edge in an increasingly digital marketplace.
A Brief History of Java Frameworks
Java was first introduced in 1991 by James Gosling and a team of engineers at Sun Microsystems. Initially, it was named Oak, inspired by an oak tree located outside Gosling’s office.
At the time, the primary focus of Oak was on consumer electronic products, such as smart televisions and set-top boxes. However, due to trademark conflicts with Oak Technologies, the name was later changed to Java.
With the introduction of the World Wide Web (WWW), Java shifted its focus towards interactive web content. Sun Microsystems developed a prototype web browser called Web Runner, which was later renamed HotJava.
This browser allowed Java applets to run directly on web pages, setting the stage for Java’s widespread adoption in web development. In 1995, Java was officially released to the public, marking the beginning of its journey as a dominant programming language.
Over the years, Java has evolved continuously, receiving multiple updates and security patches. Its most recent stable release, Java SE 24, ensures developers have access to the latest features, performance improvements, and security enhancements.
Today, Java is maintained by Oracle Corporation, which continues to support and advance the language for modern development needs. Its reliability, scalability, and cross-platform capabilities have made it a staple for web development projects across industries.
Why Java Frameworks Are Essential in Web Development
Java’s frameworks play a crucial role in simplifying the development process, reducing repetitive coding tasks, and providing ready-to-use solutions for common development challenges. These frameworks help developers create robust web applications with faster deployment times, enhanced security, and better maintainability. Additionally, frameworks allow teams to focus more on business logic rather than technical complexities, ultimately accelerating project delivery and reducing costs.
By using Java frameworks, businesses can create applications that are scalable, maintainable, and optimized for performance. They provide essential tools for integrating databases, managing user sessions, handling HTTP requests, building APIs, and deploying applications in cloud environments. This makes them indispensable for companies looking to develop modern web solutions that can adapt to evolving market demands.
Popular Java Frameworks for Web Development
Java offers a diverse range of frameworks catering to different development needs. Below are some of the most widely used frameworks:
Full-Stack Frameworks
- Spring Framework: One of the most popular Java frameworks, Spring is widely used for building large-scale, enterprise-grade applications. It excels in managing transactions, security, and data integration, making it a preferred choice for sectors like banking, e-commerce, and government services.
- Spring Boot: A derivative of the Spring framework, Spring Boot simplifies the development of microservices and cloud-based applications. Its minimal configuration requirements and built-in features make it ideal for companies aiming for rapid deployment and efficient backend services.
Microservice Frameworks
- Quarkus: Designed specifically for cloud-native applications, Quarkus enables developers to build lightweight, high-performance microservices that consume minimal memory. It is particularly suited for scalable cloud deployments.
- Dropwizard: Focused on building RESTful APIs and efficient web services, Dropwizard is widely used in fintech and API-centric companies. Its simplicity and performance make it a go-to framework for developers working on service-oriented architectures.
Emerging Frameworks
- Javalin: A lightweight, modern framework, Javalin is ideal for developing RESTful APIs and microservices with minimal configuration. Its simplicity and flexibility have made it increasingly popular among developers seeking rapid development cycles.
- Helidon: Helidon is another modern framework designed for cloud-native applications. It provides developers with tools to build scalable and efficient web applications while ensuring seamless integration with cloud platforms.
Web Application Frameworks
- Apache Struts: Struts is a robust web application framework that streamlines the process of handling HTTP requests, data integration, and server-side management. Though traditionally used in monolithic systems, it remains relevant for specific enterprise projects.
- Vaadin: Vaadin is a versatile framework for building modern web applications with Java. It supports both front-end and back-end development, making it particularly useful for creating dashboards, internal tools, and complex web interfaces.
Integrating Java Frameworks for Maximum Efficiency
The wide variety of Java frameworks allows developers to choose the best tool for their specific project requirements. Whether you need a full-stack solution like Spring Boot, a cloud-native microservice framework like Quarkus, or a lightweight API-focused framework like Javalin, Java’s ecosystem provides the flexibility to build tailored solutions.
By combining these frameworks strategically, businesses can develop web applications that are not only functional but also scalable, secure, and future-ready.
Why Businesses Should Opt for Java Development Services
Java’s versatility and robust framework ecosystem make it an ideal choice for businesses looking to develop web applications that support growth and innovation. Professional Java development services offer several advantages, including:
- Scalability: Applications built using Java frameworks can easily scale to accommodate increasing traffic and complex workflows.
- Security: Java provides built-in security features, while frameworks like Spring add additional layers of protection for sensitive business data.
- Cross-Platform Compatibility: Java applications can run seamlessly across multiple platforms, reducing development time and costs.
- Rapid Development: Frameworks reduce repetitive coding tasks, enabling faster project delivery.
- Support and Maintenance: Java’s long-standing presence ensures extensive community support, documentation, and regular updates.
At Pattem Digitals, one of India’s leading software product development companies, our team of expert developers is well-versed in all major Java frameworks.
We assist businesses in understanding the importance of each framework and selecting the right solution that aligns with their project requirements and business objectives. Our approach ensures scalable, high-performance web applications designed to accelerate growth and maximize ROI.
Conclusion
Java continues to be a powerhouse in the world of web development, thanks to its versatile frameworks and robust ecosystem. From enterprise-grade applications to cloud-native microservices and responsive web applications, Java frameworks provide the tools and flexibility needed to meet the demands of modern development.
Businesses leveraging Java frameworks can build secure, scalable, and high-performing applications that drive growth and offer a competitive advantage. With the guidance of experienced Java developers, organizations can harness the full potential of these frameworks, outcomes and sustainable digital transformation.
-
Business2 years ago
Cybersecurity Consulting Company SequelNet Provides Critical IT Support Services to Medical Billing Firm, Medical Optimum
-
Business2 years ago
Team Communication Software Transforms Operations at Finance Innovate
-
Business3 years ago
Project Management Tool Transforms Long Island Business
-
Business2 years ago
How Alleviate Poverty Utilized IPPBX’s All-in-One Solution to Transform Lives in New York City
-
health3 years ago
Breast Cancer: The Imperative Role of Mammograms in Screening and Early Detection
-
Sports3 years ago
Unstoppable Collaboration: D.C.’s Citi Open and Silicon Valley Classic Unite to Propel Women’s Tennis to New Heights
-
Art /Entertainment3 years ago
Embracing Renewal: Sizdabedar Celebrations Unite Iranians in New York’s Eisenhower Park
-
Finance3 years ago
The Benefits of Starting a Side Hustle for Financial Freedom






























