Technology Explained
The Role of Quantum Cryptography in Secure Communications

Quantum cryptography stands at the forefront of cybersecurity, leveraging principles of quantum mechanics to ensure unprecedented levels of security in communications. Unlike traditional cryptographic methods, which rely on complex mathematical algorithms, quantum cryptography utilizes quantum properties such as superposition and entanglement to enable secure key distribution and data transmission.
Principles of Quantum Cryptography
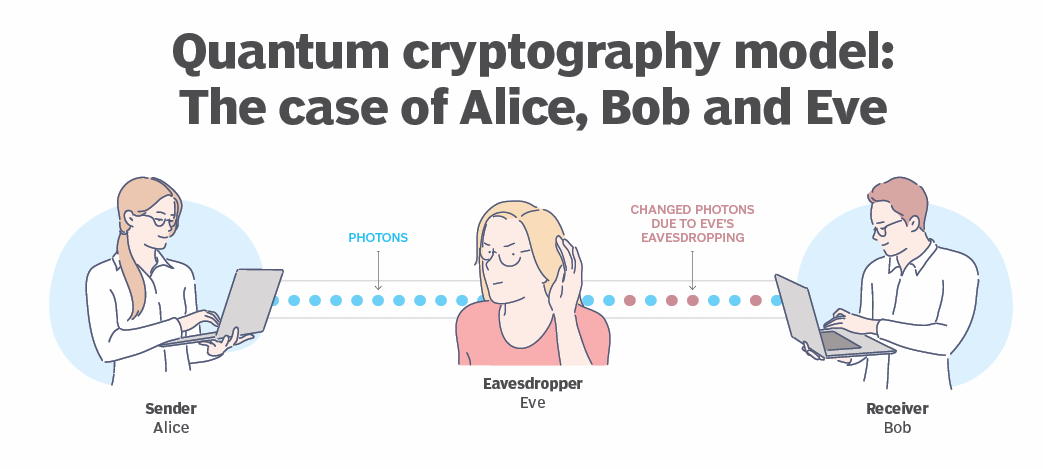
Image by : Yandex
At its core, quantum cryptography relies on quantum key distribution (QKD) protocols like BB84 and E91 to exchange encryption keys securely. These protocols leverage the quantum properties of photons to create cryptographic keys that are inherently secure against eavesdropping attempts. This ensures that any attempt to intercept the key alters its quantum state, alerting both sender and receiver to potential security breaches.
Applications of Quantum Cryptography
In practical terms, quantum cryptography offers robust solutions for secure data transmission across various sectors, including telecommunications, finance, and government. Organizations like ID Quantique and QuintessenceLabs have pioneered quantum key generation and management systems, integrating them into critical infrastructure where data security is paramount. These systems provide a defense against quantum computing threats, which conventional cryptographic methods may be vulnerable to in the future.
Challenges and Limitations
Despite its promise, quantum cryptography faces challenges such as scalability and cost-effectiveness. Implementing QKD systems requires advanced infrastructure and significant initial investments, limiting widespread adoption. Additionally, ensuring compatibility and regulatory compliance across different jurisdictions remains a hurdle for global deployment.
Future Outlook and Innovations
Looking ahead, advancements in quantum computing hold the potential to both enhance and challenge quantum cryptography. Innovations in quantum-resistant algorithms are underway to prepare for future threats posed by quantum computers. Moreover, international efforts are focused on standardizing quantum cryptography protocols and ensuring regulatory alignment to facilitate broader adoption.
Quantum Cryptography in Practice
In practice, quantum cryptography addresses fundamental challenges of traditional cryptographic methods by leveraging quantum phenomena. Quantum key distribution (QKD) protocols, such as BB84, enable the creation of cryptographic keys that are resistant to interception due to the principles of quantum mechanics. This ensures that any attempt to observe or measure quantum states by a third party inevitably alters the state of the quantum particles, thereby alerting the sender and receiver to the presence of an eavesdropper. As a result, quantum cryptography provides a level of security that is theoretically unbreakable, offering robust protection against both current and future threats in the realm of cybersecurity.
Real-World Applications
The adoption of quantum cryptography extends across various industries where secure communications are critical. For instance, in telecommunications, quantum-secure networks ensure confidential transmission of sensitive data and communications between government agencies and financial institutions. These networks employ quantum key distribution to safeguard against cyber espionage and data breaches, supporting national security and protecting proprietary information. Moreover, in sectors like healthcare and e-commerce, where privacy and data integrity are paramount, quantum cryptography offers a trustworthy framework for secure transactions and the protection of personal information.
Technological Advancements

Image by : Yandex
Technological advancements in quantum cryptography continue to drive innovation in cybersecurity. Companies and research institutions are exploring novel approaches to enhance the efficiency and scalability of QKD systems. Innovations in quantum repeaters and quantum memories aim to extend the range and reliability of quantum-secure communication networks. Additionally, efforts in quantum-resistant cryptography aim to develop algorithms capable of withstanding potential threats posed by quantum computers, ensuring long-term security for encrypted data.
Challenges and Considerations
Despite its potential, quantum cryptography faces several practical challenges. The implementation of QKD systems requires sophisticated infrastructure and specialized equipment, which can be costly and complex to deploy. Moreover, achieving interoperability and standardization across different quantum cryptography platforms remains a challenge for widespread adoption. Additionally, regulatory frameworks and compliance requirements vary globally, posing hurdles for seamless integration of quantum cryptography into existing communication networks and systems.
Future Directions
Looking ahead, the future of quantum cryptography holds promise for advancing cybersecurity capabilities. Continued research and development efforts are focused on overcoming current limitations and scaling quantum cryptography solutions for broader commercial and industrial applications. As quantum computing technology matures, the integration of quantum-resistant algorithms and quantum-enhanced security measures will play a pivotal role in safeguarding digital communications and securing critical infrastructures worldwide.
These additional paragraphs expand on the practical applications, technological advancements, challenges, and future directions of quantum cryptography in secure communications. They provide a more comprehensive view of how this cutting-edge technology is reshaping cybersecurity strategies and protecting sensitive information in various sectors globally.
Public and Private Sector Adoption
The adoption of quantum cryptography extends beyond traditional sectors into government and private industries, where secure communications are vital. Governments worldwide are investing in quantum-safe infrastructure to protect national security interests, confidential communications, and critical infrastructure from cyber threats. In the private sector, industries such as banking and finance are exploring quantum cryptography solutions to fortify digital transactions, secure financial data, and ensure compliance with stringent data protection regulations. As quantum technologies mature and become more accessible, collaborations between public and private entities will accelerate the deployment of quantum cryptography across diverse applications.
Educational and Research Initiatives
Educational institutions and research organizations play a crucial role in advancing quantum cryptography through fundamental research and practical applications. Universities and labs worldwide are conducting pioneering research in quantum mechanics, photonics, and information theory to develop cutting-edge QKD (Quantum key distribution) protocols and quantum-resistant algorithms. Collaborative efforts between academia and industry facilitate knowledge transfer and skill development in quantum cryptography, preparing the next generation of cybersecurity professionals and engineers to address evolving challenges in secure communications. By fostering interdisciplinary collaborations and promoting knowledge-sharing initiatives, educational initiatives contribute to the ongoing evolution and adoption of quantum cryptography in global cybersecurity landscapes.
Competitive Analysis Table
| Company/Organization | Quantum Cryptography Solutions | Key Technologies | Market Presence |
| ID Quantique | Quantum Key Distribution (QKD) | BB84 protocol, QRNG | Global telecommunications and government sectors |
| QuintessenceLabs | Quantum-enhanced cybersecurity | Quantum key generation, encryption key management | Financial services, defense sectors |
| Toshiba | Quantum Cryptography Network Solutions | QKD, quantum encryption | Commercial and government communication networks |
| MagiQ Technologies | Quantum Optical Networking Solutions | QKD, entangled photon sources | Optical quantum communication technologies |
Strategic Analysis Table
| Consideration | Description | Benefits | Challenges |
| Security Assurance | High-level security through quantum principles | Unbreakable encryption, protection against quantum attacks | Integration complexity, scalability |
| Regulatory Compliance | Meeting data protection standards | Compliance with privacy regulations, global regulatory alignment | Standardization, legal complexities |
| Cost-effectiveness | Balancing security benefits with costs | Long-term data protection, risk mitigation | Initial investment, affordability |
Conclusion
In conclusion, quantum cryptography represents a paradigm shift in cybersecurity, offering unparalleled levels of protection for sensitive communications and data. By harnessing the principles of quantum mechanics, quantum key distribution (QKD) protocols ensure secure key exchange and data transmission that is resistant to interception, even by advanced computing systems. The adoption of quantum cryptography is gaining momentum across various industries, including telecommunications, finance, healthcare, and government, where data security and privacy are paramount concerns.
Looking forward, the future of quantum cryptography holds tremendous promise and potential. Continued advancements in quantum computing and quantum networking technologies will further enhance the scalability, efficiency, and reliability of quantum cryptography systems. Research efforts in quantum-resistant algorithms and protocols will continue to evolve, addressing challenges such as interoperability, cost-effectiveness, and regulatory compliance. Moreover, collaborative initiatives between academia, industry, and governments will play a crucial role in accelerating the adoption and standardization of quantum cryptography solutions globally.
As organizations navigate an increasingly complex and interconnected digital landscape, quantum cryptography stands poised to provide robust safeguards against emerging cyber threats and vulnerabilities. By integrating quantum-safe solutions into their cybersecurity frameworks, businesses and governments can strengthen their defenses, safeguard sensitive information, and uphold trust and reliability in digital communications. Ultimately, quantum cryptography represents not only a technological advancement but also a critical enabler of secure and resilient communication infrastructures in the digital age.
Consumer Services
Cloud Downtime: Essential for Infrastructure Management

Downtime never comes with a warning. It doesn’t care if you’re launching a feature, running a campaign, or sleeping peacefully. It just shows up — and when it does, the damage goes far beyond a broken dashboard.
I’ve seen teams lose users, revenue, and confidence within minutes of an outage. What’s frustrating is this: most downtime isn’t caused by the cloud itself. It’s caused by how the cloud is managed. That’s where cloud downtime infrastructure management stops being a technical checkbox and becomes a business-critical discipline.

Downtime Is a Management Failure, Not a Cloud Failure
AWS, Azure, and Google Cloud are built for resilience. They fail occasionally — yes — but widespread outages usually trace back to internal issues like:
- No proper load balancing or failover
- Systems not designed for traffic spikes
- Manual deployments without rollback plans
- Weak monitoring that reacts too late
- Security gaps that turn into system crashes
The cloud gives you power. Poor infrastructure decisions turn that power into risk.
What “Stopping Downtime Cold” Really Means
It doesn’t mean hoping nothing breaks.
It means expecting failure and designing systems that survive it.
Strong cloud infrastructure management focuses on four core pillars.
1. Architecture Built for Failure
If your system collapses when one service fails, it was never stable to begin with.
High-availability infrastructure includes:
- Load balancers across multiple availability zones
- Auto-scaling that reacts before performance drops
- Redundant services so failures stay isolated
When architecture is done right, failures don’t become incidents — they become background noise.
2. Proactive Monitoring Instead of Panic Alerts
If customers are the first ones to notice downtime, you’re already late.
Modern cloud environments rely on:
- Real-time health monitoring
- Smart alerts that trigger before limits are reached
- Centralized logs for faster root-cause analysis
Cloud providers themselves emphasize observability because visibility is what turns outages into manageable events instead of full-blown crises.
3. Automation That Removes Human Error
Manual processes are one of the biggest causes of downtime.
Teams that prioritize stability automate:
- Infrastructure provisioning
- Scaling rules
- Backups and disaster recovery
- CI/CD deployments with safe rollbacks
Automation doesn’t just save time — it prevents mistakes, especially during high-pressure moments.
4. Security That Protects Stability
Security incidents are downtime.
Unpatched systems, exposed credentials, and poor access controls often end with services being taken offline.
Strong cloud management includes:
- Continuous security monitoring
- Role-based access control
- Encrypted data pipelines
- Automated patching and compliance checks
Security and uptime aren’t separate goals. They depend on each other.
Where Growing Teams Usually Slip
Here’s something I’ve seen far too often. A product starts gaining traction, traffic slowly increases, integrations pile up, and suddenly the infrastructure that once felt “solid” starts showing cracks. Not all at once but in subtle, dangerous ways. Pages load a little slower. Deployments feel riskier. Minor incidents start happening more frequently, yet they’re brushed off as one-off issues. Teams stay focused on shipping features because growth feels urgent, while infrastructure quietly falls behind. The problem is that cloud systems don’t fail dramatically at first — they degrade.
And by the time downtime becomes visible to users, the technical debt has already piled up. Without regular audits, performance optimization, and proactive scaling strategies, even well-designed cloud environments become fragile over time. This is usually the point where teams realize that cloud infrastructure isn’t something you “set and forget.” It’s a living system that needs continuous attention to stay reliable under real-world pressure.
The Hidden Cost of “Mostly Stable” Systems
A lot of companies settle for “good enough.”
99% uptime sounds impressive — until you realize that’s more than three days of downtime per year.
Now add:
- Lost transactions
- User churn
- Support overload
- Engineering burnout
Suddenly, downtime isn’t a technical issue. It’s a growth blocker.
Reliable infrastructure doesn’t just protect systems — it protects momentum.
Where Growing Teams Usually Slip
I’ve noticed this pattern again and again.
Teams invest heavily in:
- Product features
- Design improvements
- Marketing and growth
But infrastructure gets treated as:
“We’ll fix it when it breaks.”
The problem is that cloud environments are not static. Traffic grows, data scales, integrations multiply. Without continuous management, even well-built systems degrade over time.
That’s why many scaling companies eventually move toward structured cloud engineering practices that focus on long-term reliability, not just initial setup.
Stability Feels Boring — And That’s the Goal
The best infrastructure doesn’t get attention.
It feels boring because:
- Deployments don’t cause anxiety
- Traffic spikes don’t break systems
- Incidents resolve quietly or automatically
That calm is the result of intentional decisions, not luck.
Downtime thrives in chaos.
Stability thrives in preparation.
Final Thoughts
Downtime isn’t inevitable. It’s a signal that systems weren’t built — or managed — for reality. Cloud infrastructure management isn’t about keeping servers running. It’s about protecting user trust, revenue, and your team’s sanity. When infrastructure is resilient, everything else moves faster.
Ready to Stop Worrying About Downtime?
If your platform is scaling — or planning to — reliable cloud downtime infrastructure isn’t optional anymore. The right cloud engineering approach doesn’t just reduce outages.
It removes fear from growth. Explore what resilient, production-ready cloud infrastructure looks like here:
Build for failure. Scale with confidence. And make downtime something your users never have to think about.
Technology
Google Sheet Connector for WooCommerce: Optimize Efficienc
In the ever-evolving landscape of online shopping in 2026, efficiently managing your store’s data is crucial for business growth. Manual data handling for orders and stock has become unviable. Businesses now need automation to thrive. Enter the Google Sheet Connector for WooCommerce—a powerful tool that establishes a seamless link between your WooCommerce store and Google Sheets. This solution enables real-time updates and analytics.
It ensures your operations team always has the most accurate data at their fingertips. Whether you’re looking to analyze sales performance or adjust stock levels, this connector simplifies the process. This allows you to focus on what truly matters: growing your business.

Understanding the Google Sheet Connector for WooCommerce
The Google Sheet Connector for WooCommerce is a sophisticated tool. It automatically synchronizes data from your WooCommerce platform with Google Sheets. By establishing a continuous flow of information, it gathers crucial data—such as orders, product details, and customer information—directly into a user-friendly spreadsheet format. Unlike traditional data export methods that require cumbersome CSV files, this connector ensures that your data is always up-to-date and accessible.
How It Works
The connector operates on a straightforward principle: automatic synchronization. This eliminates the need for manual data entry, significantly reducing human error rates.
- Real-Time Synchronization: Orders, product updates, and customer profiles are instantly reflected in your Google Sheets. This provides operational transparency
- Two-Way Data Sync: You can send data to Google Sheets. You can also update prices or stock levels directly within the spreadsheet. These changes are then reflected back in WooCommerce
- Centralized Reporting: The integration offers a single hub for all your reporting needs. This makes it easier for accountants, inventory managers, and fulfillment teams to manage data without jumping between platforms
Security and Flexibility
One compelling aspect of the WooCommerce Google Sheet Connector is its security features. It utilizes Google OAuth for authentication. The connector requires a Client ID and Secret for a safe and seamless connection. Furthermore, it allows for flexible sync modes. You can choose between immediate synchronization for urgent updates or scheduled syncs to conserve server resources.
Features of the WooCommerce Google Sheet Connector
The Google Sheet Connector is equipped with various features designed to improve operational efficiency:
- Order Management: This feature enables quick updates to order statuses. It ensures that all relevant data is promptly reflected in your spreadsheet
- Inventory Control: Track stock levels and pricing effectively. This gives you better oversight of your inventory
- Custom Field Mapping: You can select which order information is synced to the spreadsheet. This allows for tailored data management that fits your specific needs
- Status-Based Tabs: Orders are sorted into different tabs in Google Sheets based on their current status. This makes it easy to visualize and manage them
Advantages of Integrating Google Sheets with WooCommerce
Using Google Sheets alongside WooCommerce offers numerous benefits that can streamline your business processes:
- Operational Transparency: Your team has immediate access to real-time order data. They don’t need to log into the WordPress dashboard, making it easier to spot trends and respond to customer needs
- Dynamic Analytics: Google Sheets enables you to create customized dashboards using pivot tables and charts. This allows you to visualize your store’s performance effectively
- Effortless Collaboration: The integration facilitates seamless teamwork. It enables shared access to essential data, improving communication with vendors, suppliers, and shipping partners
- Time-Saving Bulk Updates: The connector allows you to perform bulk edits. You can efficiently update prices for numerous products through Google Sheets. This significantly reduces the time spent on manual entry
Setting Up Your Google Sheet Connector for WooCommerce
Getting started with the Google Sheet Connector is straightforward. Here’s a step-by-step guide:
- Install the Plugin: Add and activate the connector plugin on your WordPress site to establish functionality
- Generate API Credentials: Access the Google Cloud Console to create a Client ID and Secret for authentication
- Authenticate Your Account: Link your Google account through the plugin settings on your website. This ensures secure access
- Designate Your Google Sheet: Paste the ID of the desired Google Sheet to set it as your primary data storage.
- Configure Field Mapping: Customize the rules for which data will synchronize. Choose between real-time updates or scheduled syncs
- Execute a Manual Sync: Run a manual synchronization to populate your sheet with existing store data, kickstarting the integration
Best Practices for Managing Your Google Sheets Data
To maximize the benefits of your Google Sheet Connector, consider implementing the following best practices:
- Efficient Mapping: Only sync the columns you need. This keeps your sheet organized and fast-loading
- Color-Coding: Use status-based colors to visually differentiate between pending and completed orders. This allows for quick assessments at a glance
- Sheet Protection: Protect column headers to prevent accidental changes. This ensures data integrity
- Regular Audits: Periodically check your Google API quotas. This helps maintain a smooth synchronization process, especially for high-volume stores
Conclusion: Streamline Your WooCommerce Operations
The Google Sheet Connector for WooCommerce is more than just a tool; it’s a lifeline. It enhances your operational efficiency and data management capabilities. With features designed to provide real-time insights and easy collaboration, this integration empowers your business. It helps you adapt to the fast-paced world of online retail in 2026.
By embracing this technology, you’ll save time and reduce errors. You’ll also cultivate a more informed and agile approach to managing your WooCommerce store. Investing in seamless data management solutions like the Google Sheet Connector is a wise choice that pays dividends in the long run.
Jobs and education
Mastering the Braze Practitioner Exam: Your Comprehensive Guide

Introduction
The Braze Practitioner Exam is a critical certification for professionals looking to demonstrate their expertise in customer engagement, marketing automation, and Braze platform management. As businesses continue to adopt data-driven marketing strategies, Braze has become one of the leading tools for delivering personalized customer experiences.
By earning the Braze Certified Practitioner certification, individuals validate their ability to effectively use Braze’s features to create, manage, and optimize customer journeys.
This guide will delve into the types of Braze Practitioner exam questions, helping you understand the key topics that will be tested, how to prepare, and what you can expect when taking the exam. Whether you’re a marketer, customer success professional, or marketing automation expert, understanding what to expect in the exam will increase your chances of success.

What is the Braze Practitioner Certification Exam?
The Braze Certified Practitioner Exam is a professional certification that assesses your knowledge and hands-on skills in using the Braze platform to create data-driven, personalized customer engagement campaigns. The exam tests your ability to manage campaigns, leverage data for segmentation, automate workflows, and analyze performance to optimize future strategies.
Candidates who successfully pass the exam are recognized as proficient users of the Braze platform and capable of driving significant customer engagement outcomes. The exam includes a mix of multiple-choice questions, case studies, and scenario-based questions that reflect real-world marketing challenges.
Key Topics Covered in Braze Practitioner Exam Questions
The Braze Practitioner Exam covers several important areas that all Braze users should be well-versed in. Here’s a breakdown of the main topics:
1. Braze Platform Fundamentals
One of the core areas tested is your understanding of Braze’s platform fundamentals. This includes knowing how to navigate the dashboard, configure account settings, and understand key platform features. Expect questions about how to integrate Braze with external data sources and how to set up user profiles, events, and attributes.
- Possible Exam Questions:
- What is the primary function of Braze Canvas in creating customer journeys?
- How do you configure push notifications and what data is required to personalize them?
2. Campaign Management and Strategy
Braze is designed for automating and personalizing campaigns, and this is a major focus of the exam. You’ll need to understand how to create and manage multi-channel campaigns using Braze’s various messaging features, including email, in-app messages, push notifications, and more.
- Possible Exam Questions:
- How do you create an automated lifecycle campaign to re-engage inactive users?
- What steps are involved in setting up a cross-channel campaign within Braze?
3. Segmentation and Audience Management
A strong understanding of audience segmentation and how to use customer data to personalize communication is crucial. The exam will test your ability to set up audience segments based on behavioral and demographic data, and how to use those segments to deliver personalized campaigns.
- Possible Exam Questions:
- Which segment criteria would you use to create an audience of high-value customers who have made purchases in the last 30 days?
- How do you use Braze’s event tracking to trigger personalized messages based on user behavior?
4. Data-Driven Marketing
Braze is all about leveraging data to drive engagement. You’ll need to know how to integrate customer data, use event-based triggers, and create personalized messages based on user behavior. Expect questions on how to collect and use data to segment audiences effectively and how to use that data to automate targeted marketing strategies.
- Possible Exam Questions:
- How does Braze’s data integration allow you to sync user attributes and events across different platforms?
- What is the role of dynamic content in email campaigns, and how do you use it to personalize messages?
5. Analytics and Reporting
Braze offers robust analytics tools to track the effectiveness of your campaigns. The exam will test your ability to understand key metrics, analyze campaign results, and make data-driven decisions for optimization.
- Possible Exam Questions:
- Which metrics should you focus on when evaluating the success of a push notification campaign?
-
How can you use Braze’s A/B testing feature to improve the performance of your email campaigns?
6. Advanced Engagement Techniques
Once you’ve mastered the basics of campaign setup and data integration, the exam will test your understanding of advanced engagement strategies. This includes creating complex multi-step journeys, managing user feedback loops, and optimizing customer engagement across all channels.
- Possible Exam Questions:
- How would you set up an abandoned cart workflow that sends a push notification followed by an email reminder?
- What advanced strategies would you implement to re-engage users who haven’t interacted with your app in 60 days?
How to Prepare for the Braze Practitioner Exam?
To succeed in the Braze Certified Practitioner Exam, preparation is key. Here are some practical tips to help you study effectively:
- Gain Hands-On Experience with Braze:
The best way to prepare is by using Braze regularly. Create and manage real campaigns, work with customer segmentation, and use the analytics tools to optimize your strategies. This will ensure that you’re familiar with the platform’s features.
- Study the braze acadmey:
Braze offers online courses and training materials through the Braze Academy. This is a comprehensive resource that covers all the key areas tested in the exam. Completing the courses will give you a solid understanding of the platform. - Review Braze Documentation and Case Studies:
Braze’s official documentation is a treasure trove of information about the platform. Make sure to familiarize yourself with the Braze knowledge base and review case studies that show how Braze is used in real-world scenarios. - Take Practice Exams:
Some online platforms like ExamsEmpire provide practice exams that mimic the format and difficulty of the Braze Certified Practitioner Exam. These can assist you in assessing your preparedness and pinpointing areas needing enhancement
Frequently Asked Questions (FAQs)
What is the passing score for the Braze Practitioner exam?
The passing score for the Braze Certified Practitioner Exam is typically around 70%, though this can vary.
How long is the Braze Practitioner exam?
The exam typically lasts for 90 minutes, and it consists of multiple-choice questions and scenario-based questions.
What is the format of the exam?
The exam is online, with multiple-choice questions and practical scenarios that test your ability to apply Braze tools in real-world situations.
How can I register for the Braze Practitioner exam?
You can register for the exam via the Braze Academy or the official Braze certification portal.
What is the validity of the Braze certification?
The Braze Certified Practitioner Certification is typically valid for two years. After that, you may need to renew it to stay updated with the latest features.
The Braze Practitioner Exam is a comprehensive and practical certification that proves your ability to leverage the Braze platform for data-driven customer engagement. By understanding the key topics covered in the exam, practicing regularly on the platform, and using the resources available in the Braze Academy, you can be well-prepared to pass the exam and boost your career in marketing automation and customer success.
-
Business3 years ago
Cybersecurity Consulting Company SequelNet Provides Critical IT Support Services to Medical Billing Firm, Medical Optimum
-
Business3 years ago
Team Communication Software Transforms Operations at Finance Innovate
-
Business3 years ago
Project Management Tool Transforms Long Island Business
-
Business2 years ago
How Alleviate Poverty Utilized IPPBX’s All-in-One Solution to Transform Lives in New York City
-
health3 years ago
Breast Cancer: The Imperative Role of Mammograms in Screening and Early Detection
-
Sports3 years ago
Unstoppable Collaboration: D.C.’s Citi Open and Silicon Valley Classic Unite to Propel Women’s Tennis to New Heights
-
Art /Entertainment3 years ago
Embracing Renewal: Sizdabedar Celebrations Unite Iranians in New York’s Eisenhower Park
-
Finance3 years ago
The Benefits of Starting a Side Hustle for Financial Freedom






























