Internet and Telecom
How the Internet is Heading Towards a Dark Future

How the Internet is Heading Towards a Dark Future
Unveiling the Dark Future: The Internet’s Troubling Evolution
Introduction: Navigating the Ominous Horizons
In the labyrinth of the digital world, Emily stands as a seasoned cybersecurity analyst, committed to unveiling the intricacies of the internet’s shifting landscape. Over a decade of traversing the online realm has unveiled a concerning truth—our digital future is taking a dark turn.
The internet, once a symbol of global connectivity and boundless knowledge, is fast evolving into an alarming terrain. Its promising potential tainted by growing concerns that are altering the course of our online journey.
1. The Unsettling Trends
In an era where our lives are intricately entwined with the digital fabric, the trends shaping the internet’s trajectory are far from optimistic. The promising beacon of connectivity now casts shadows of concern, shedding light on alarming developments that have the potential to dim the internet’s brilliance.
The first thread in this disconcerting tapestry is the erosion of privacy. Our digital footprints, once seemingly secured, now face unprecedented vulnerability. Data breaches, intrusive surveillance, and the commodification of personal information have raised red flags, threatening the sanctity of our online identities.
Accompanying this is the increasingly fragile fortress of cybersecurity. The proliferation of sophisticated hacking techniques, phishing attacks, and vulnerabilities in digital infrastructures has left both individuals and institutions exposed to the looming specter of cyber threats.
Moreover, the online sphere has become a breeding ground for menacing content and disinformation. Fake news and harmful content dissemination have not only sown seeds of societal division but have also given rise to misinformation’s widespread propagation, shaping public opinions and perceptions.
Policymakers and the industry’s giants hold a pivotal role in navigating this disconcerting path. Their decisions, regulations, and ethical standards significantly impact the digital ecosystem’s security and users’ well-being.
In unraveling these unsettling trends, it becomes evident that our online realm is at a crossroads, beckoning for immediate attention and proactive measures.
2. Navigating the Dark Alleys: Privacy Erosion
The erosion of privacy stands as a monumental concern in our digital age. Our once-private lives are now subject to unprecedented vulnerability. Data breaches, often making headlines, have become distressingly common, leaving individuals exposed and their personal information compromised. Whether it’s social media platforms, e-commerce sites, or even government databases, the omnipresence of data has become a double-edged sword, offering convenience while posing risks.
However, the root of this erosion extends beyond breaches; the commercialization of personal data adds an alarming dimension. Our information is a commodity, traded and sold by corporations, casting doubt on the sanctity of our online identities.
The implications are vast, affecting not only our digital lives but seeping into the real world, influencing decisions, and potentially undermining our autonomy. From targeted advertisements to more sinister possibilities like identity theft and fraud, the consequences of privacy erosion are far-reaching.
3. Cybersecurity: The Weakening Bastion
The cybersecurity fortress, once thought impenetrable, now stands under constant siege. Hacking techniques, once the domain of the few, have proliferated, becoming more sophisticated and widespread. Phishing attacks, malware, ransomware, and vulnerabilities within systems pose an ever-increasing risk, threatening both personal and organizational data security.
For individuals, the risk is palpable. Personal accounts, sensitive information, and financial details are at stake. Businesses and institutions face similar dangers on a larger scale, from data breaches leading to financial loss to compromising sensitive information, damaging trust and credibility.
The integration of technology into every aspect of modern life further amplifies the stakes, with smart homes, interconnected devices, and the Internet of Things (IoT) opening new frontiers for potential attacks.

Image by rawpixel.com on Freepik
4. Menacing Content and Disinformation
The proliferation of harmful content and disinformation online poses a substantial societal threat. The widespread dissemination of fake news and the manipulation of information threaten to undermine the very fabric of our shared reality.
Misinformation and divisive content not only polarize societies but also jeopardize the foundation of informed decision-making, corroding the essence of democratic discourse. This shadowy landscape of misinformation has repercussions on political, societal, and personal levels, shaping perceptions and beliefs.
5. The Role of Policymakers and Responsibility
Amid these turbulent digital waters, the responsibility falls not just on individuals but also on policymakers and tech behemoths. The decisions and regulations set forth by governing bodies and the ethical standards upheld by industry leaders play a pivotal role in shaping a safer digital environment.
Policymakers hold the power to enact regulations that safeguard user privacy, curb the spread of disinformation, and reinforce cybersecurity measures. However, crafting effective policies that strike a balance between protection and innovation is a nuanced challenge.
Similarly, tech giants and corporations wield immense influence over the digital terrain. Their commitment to ethical tech practices, data protection, and the moderation of harmful content profoundly impacts the overall health of the online realm. Upholding responsibility and transparency in their operations becomes imperative in fostering a secure digital future.
6. Illuminating the Path: Solutions and Proactive Measures
While the trends paint a foreboding picture, there exist avenues to steer the internet towards a brighter future. Encryption stands as a fundamental tool in safeguarding data transmission, ensuring confidentiality and integrity.
Moreover, user education becomes paramount. Equipping individuals with digital literacy and promoting critical thinking can empower users to navigate the online realm with prudence, distinguishing fact from fiction.
Implementing ethical tech practices within organizations is essential. By prioritizing responsible use of technology, companies contribute to a more secure digital ecosystem.
Most crucially, collective responsibility serves as the cornerstone for a secure online environment. Collaboration among users, industry players, and policymakers is vital in fortifying the internet’s foundations against evolving threats.
Insightful Visual Table: Trends and Their Impact
| Trends | Impact |
|---|---|
| Privacy Erosion | Vulnerability of personal data |
| Cybersecurity Weaknesses | Increased risk of data breaches and attacks |
| Disinformation | Societal division and misinformation spread |
| Policy and Responsibility | Shaping ethical standards and regulations |
This visual representation encapsulates the primary trends shaping the internet’s trajectory and their consequential impacts, offering a clear and concise overview of the challenges faced in our digital realm.
Comparative Table: Solutions Overview
| Solutions | Description |
|---|---|
| Encryption | Safeguarding data transmission |
| User Education | Empowering individuals with digital literacy |
| Ethical Tech Practices | Implementing responsible tech standards |
| Collective Responsibility | Uniting for a secure online environment |
This comparative table presents a succinct overview of the proposed solutions, highlighting the key strategies necessary for a more secure online environment.
In understanding the concerns that cloud the internet’s future, it becomes evident that navigating these challenges demands a collective effort. While trends paint a grim picture, proactive measures and informed actions can pave the way for a safer and more secure online world. By embracing encryption, fostering user education, advocating ethical tech practices, and uniting in a collective responsibility, individuals, organizations, and policymakers can craft a digital realm where safety and innovation coexist.
Encryption: Safeguarding Data Transmission
Encryption acts as a shield, ensuring that data remains protected during transmission. By encoding information in a manner that can only be deciphered by authorized parties, encryption minimizes the risk of unauthorized access or tampering. Utilizing robust encryption protocols in communications, online transactions, and data storage fortifies the confidentiality and integrity of sensitive information, serving as a cornerstone for digital security.
User Education: Empowering Digital Literacy
Empowering individuals with digital literacy and critical thinking skills forms a powerful defense against online threats. Educating users about identifying potential risks, understanding privacy settings, and distinguishing between credible and misleading information equips them to navigate the digital landscape more securely. By promoting digital literacy initiatives and fostering a culture of conscious online behavior, users become better equipped to protect themselves and contribute to a safer online community.
Ethical Tech Practices: Implementing Responsible Standards
Instituting ethical tech practices within organizations and industries involves a commitment to responsible technological innovation. Embracing principles that prioritize data protection, transparent algorithms, and ethical data usage ensures a more trustworthy and secure online environment. Companies adopting such practices not only safeguard user interests but also contribute to building a digital landscape grounded in trust and integrity.
Collective Responsibility: Uniting for Online Security
Uniting in a collective responsibility is the linchpin for a secure online environment. Collaboration between individuals, tech companies, policymakers, and regulatory bodies is essential. Implementing and abiding by guidelines, advocating for regulations that balance innovation and security, and participating in community efforts to promote digital safety solidifies a unified front against digital threats. It fosters an environment where accountability and cooperation drive the internet towards a more secure and promising future.
Practical Applications and Success Stories
Implementing encryption in various facets of the digital landscape has yielded remarkable success stories. Secure end-to-end communication applications, robust encryption methods in financial transactions, and encrypted storage solutions have significantly reduced the risk of unauthorized access and data breaches. This has not only secured sensitive information but also bolstered user trust and confidence in online platforms.
User education initiatives have shown promise in shaping a more informed online community. Programs focusing on digital literacy, fact-checking, and critical thinking have empowered users to identify and thwart potential threats. Cultivating a culture where individuals are equipped with the necessary skills to navigate the digital realm has led to a more resilient and cautious online population.
Ethical tech practices, when adopted by organizations, have not only fortified data protection but have also elevated consumer trust. Companies adhering to transparent data policies and ethically sound technological innovations have gained a competitive edge. Consumers gravitate towards businesses that prioritize user privacy and integrity, fostering a mutually beneficial relationship between companies and their clientele.
The synergy of collective responsibility has borne fruit in various communities and industry collaborations. Collaborative efforts among individuals, businesses, and policymakers in advocating for robust regulations, initiating awareness campaigns, and fostering a culture of shared responsibility have significantly bolstered online safety. These joint endeavors have contributed to a more vigilant and secure digital environment.
Case Studies: Real-life Implementation
Encryption in Messaging Platforms
Messaging applications adopting end-to-end encryption, such as Signal and WhatsApp, have fortified user privacy. These platforms ensure that only the sender and intended recipient can access messages, assuring users of secure communication. This implementation has significantly contributed to safeguarding sensitive information from prying eyes.
Digital Literacy Initiatives
Communities and educational institutions have successfully implemented digital literacy programs. These initiatives, offering workshops and online modules, have equipped individuals with the tools to discern between reliable and fake news, understand privacy settings, and identify potential cyber threats. The impact has been evident in creating a more cautious and informed online populace.
Businesses Embracing Ethical Tech Standards
Companies integrating ethical tech practices have garnered increased consumer trust and loyalty. For instance, companies actively transparent about their data handling processes and prioritizing user privacy have seen a notable boost in customer loyalty. This shift towards ethical standards not only benefits users but also serves as a competitive advantage for these businesses.
Community-driven Cybersecurity Efforts
Communities uniting for cybersecurity awareness have led to proactive measures against cyber threats. Local initiatives, from organizing cybersecurity workshops to promoting safe online practices, have fortified the community’s resilience against digital threats. These collective efforts have showcased the impact of unity in combatting online dangers.
Challenges in Implementation
However, the widespread adoption of these strategies encounters various challenges. One of the key obstacles lies in the complexity of technology and privacy regulations. Striking a balance between innovation and protection without stifling progress poses a significant challenge for policymakers and industry leaders.
Additionally, there’s the challenge of user engagement. Encouraging individuals to actively participate in digital literacy initiatives and take responsibility for their online safety requires significant effort in fostering a culture of vigilance and education.
The resource constraints faced by smaller businesses in implementing robust cybersecurity measures and ethical tech practices present another challenge. Limited resources, both in terms of finances and expertise, can hinder the swift adoption of these critical strategies.
Overcoming Challenges: Recommendations
To navigate the complexities of technology and privacy regulations, fostering collaboration between policymakers, industry experts, and advocacy groups is imperative. A balanced discourse that addresses concerns and fosters innovation while safeguarding user privacy is essential. This can lead to the formulation of comprehensive policies that strike an equilibrium between progress and protection.
For user engagement, a multifaceted approach is crucial. Encouraging digital literacy from an early age, integrating it into educational curricula, and offering user-friendly resources can significantly enhance engagement. Public awareness campaigns, both online and offline, can also play a pivotal role in fostering a culture of vigilance and responsibility among users.
Addressing resource constraints in smaller businesses involves initiatives such as government support programs, accessible educational resources, and collaborations with larger entities that can provide mentorship and guidance. These efforts can equip smaller businesses with the necessary tools and knowledge to implement robust cybersecurity measures and ethical tech standards.
Long-term Benefits of Embracing Solutions
The long-term benefits of adopting proactive measures are far-reaching. A more secure online environment fosters a culture of trust and reliability. It enhances user confidence in digital platforms, thereby encouraging increased participation in online activities, whether for communication, commerce, or information sharing.
Moreover, the adoption of these strategies promotes innovation. By creating a foundation of security and trust, individuals and businesses can explore new avenues for technological advancement without compromising user privacy and safety. It paves the way for a more sustainable and progressive digital landscape.
Embracing proactive solutions not only safeguards users but also establishes a foundation for a thriving digital economy. Enhanced cybersecurity, protected data, and ethical tech practices can attract investments and collaborations, ultimately fostering economic growth and stability in the digital sphere.
Digital Development
Importance of Digital Development for Small Business Growth

Digital development has become the structural backbone of modern business growth. For small businesses, it is no longer sufficient to simply exist online; they must function, perform, and scale intelligently. A well-developed digital presence enhances usability, credibility, and discoverability simultaneously. When paired with strategic optimization from an experienced seo agency nyc, digital development transforms from a technical necessity into a powerful growth engine.

What Digital Development Really Means Today
Digital development extends far beyond launching a basic website. It encompasses platforms, user journeys, backend efficiency, and long-term adaptability. Modern development is iterative, data-informed, and deeply intertwined with search visibility.
Without SEO-conscious development, even the most visually striking digital assets risk obscurity. Conversely, development aligned with seo services in new york ensures that structure and performance actively support discoverability.
Building a Search-Optimized Digital Foundation
The foundation of effective digital development lies in clean code, logical architecture, and scalable frameworks. Search engines favor websites that are easy to crawl, fast to load, and structurally coherent. Poorly written code, redundant scripts, or convoluted navigation can silently sabotage rankings.
Small businesses that integrate SEO considerations at the development stage gain a durable advantage, particularly when guided by an seo agency with technical expertise.
Mobile-First Development in a Search-First World
Mobile-first development is no longer optional. Search engines now evaluate websites primarily through their mobile versions, making responsiveness and performance critical. Fluid layouts, optimized images, and minimal load times directly affect user satisfaction and rankings.
Core Web Vitals, metrics that measure loading speed, interactivity, and visual stability, have become decisive factors. Thoughtful mobile development ensures that SEO efforts are not undermined by technical friction.
Content Management Systems and SEO Flexibility
Choosing the right content management system (CMS) is a pivotal digital development decision. A robust CMS enables easy control over metadata, URL structures, internal linking, and content expansion. Platforms that restrict customization can stifle SEO growth over time.
Small businesses benefit from CMS environments that support agility, allowing seo services to adapt strategies as algorithms and market demands evolve.
Integrating SEO into Digital Product Development
SEO should not be an afterthought appended to a finished product. It must be embedded within the development lifecycle. UX/UI decisions, such as navigation depth, page hierarchy, and internal linking, directly influence how search engines interpret relevance.
When developers and SEO strategists collaborate, digital products emerge that are not only functional but inherently discoverable. This synergy is a hallmark of high-performing teams led by an experienced seo service nyc.
Local-Focused Digital Development for Small Businesses
For small businesses, local relevance is often the most valuable currency. Digital development should facilitate geo-targeted content, location-specific landing pages, and personalized user journeys. Local schema markup, map integrations, and regionally optimized pages enhance local search performance.
With expert guidance from seo agency in New York, businesses can align development efforts with the intent of nearby customers, driving both traffic and conversions.
Security, Speed, and Trust Signals
Security and performance are silent persuaders. HTTPS encryption, secure payment gateways, and fast-loading pages cultivate user trust while signaling quality to search engines. A slow or insecure website erodes confidence and increases bounce rates, indirectly harming SEO. Digital development that prioritizes speed and security creates a stable environment where optimization efforts can flourish without resistance.
Measuring Digital Development Success
Effective digital development is measurable. Analytics tools reveal how users interact with your platform, where friction exists, and which elements drive engagement. Metrics such as session duration, conversion paths, and page performance provide actionable insights. Continuous refinement, supported by data and professional seo services in new york, ensures that digital assets remain competitive, relevant, and growth-oriented.
Frequently Asked Questions (FAQs)
1. What is digital development for small businesses?
Digital development refers to building and improving digital assets such as websites, platforms, and online systems to enhance performance, usability, and scalability. For small businesses, it focuses on creating a strong technical foundation that supports growth and visibility.
2. Why is digital development important for long-term business growth?
Digital development ensures that a business can adapt to changing technologies, user behavior, and market demands. A well-developed digital presence improves efficiency, customer experience, and overall competitiveness in the online space.
3. How does digital development impact online visibility?
Search engines favor websites that are fast, secure, mobile-friendly, and well-structured. Strong digital development directly supports better indexing, smoother user journeys, and improved engagement, all of which contribute to higher visibility.
4. Is mobile-first development really necessary for small businesses?
Yes. Most users access websites through mobile devices. Mobile-first development ensures better performance, usability, and engagement, which are critical for retaining visitors and encouraging conversions.
5. What role does website speed play in digital development?
Website speed affects both user experience and trust. Slow-loading pages lead to higher bounce rates and lost opportunities. Optimized performance is a core element of effective digital development.
6. Can digital development improve customer trust?
Absolutely. Secure connections, intuitive navigation, and consistent performance signal professionalism and reliability, helping users feel confident when interacting with a business online.
7. How often should digital development be updated or improved?
Digital development is an ongoing process. Regular updates, performance audits, and usability improvements help businesses stay relevant and competitive as technology and user expectations evolve.
8. What is the biggest mistake small businesses make in digital development?
The most common mistake is treating digital development as a one-time project. Without continuous optimization and scalability planning, digital assets quickly become outdated and less effective.
Conclusion
Digital development is not a one-time project; it is an evolving strategy that underpins long-term success. For small businesses, investing in intelligent development aligned with SEO principles creates resilience in an unpredictable digital economy. By integrating performance, usability, and search optimization from the outset, and collaborating with a knowledgeable seo agency nyc, businesses can build digital ecosystems that support sustained visibility and meaningful growth.
Digital Development
Drake Software Installation Errors: Causes & Easy Solutions

Drake Software is one of the most trusted tax preparation tools used by CPAs, accountants, and tax professionals across the world. It is known for its affordability, speed, and powerful features that help professionals manage tax filings efficiently. However, like any software, users may face installation errors while setting it up on their system—especially during peak tax season.
If you’re struggling to install Drake Software and encountering errors, don’t worry. Most Drake installation issues are common and can be fixed easily once you understand their causes. In this blog, we’ll explain Drake Software installation errors, why they happen, and how you can solve them step by step, all in simple language.
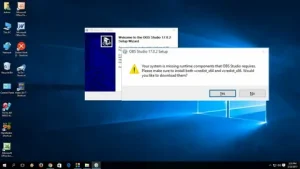
Why Drake Software Installation Errors Occur
Before jumping into solutions, it’s important to understand why installation errors happen in the first place. Most Drake Software installation issues are caused by:
- System compatibility problems
- Lack of administrative permissions
- Antivirus or firewall interference
- Corrupted installation files
- Network or server issues
- Outdated Windows or system components
Knowing the root cause makes troubleshooting faster and less frustrating.
Common Drake Software Installation Errors
Below are some of the most common installation problems users face with Drake Software.
-
System Requirements Not Met
Cause:
Drake Software requires specific system requirements such as:
- Compatible Windows version
- Sufficient RAM and storage
- Updated .NET Framework
If your computer doesn’t meet these requirements, installation may fail or stop midway.
Solution:
- Check Drake Software’s minimum system requirements
- Update your Windows operating system
- Free up disk space before installation
- Install or update Microsoft .NET Framework
A simple system update often solves this issue.
-
Installation Freezes or Stops Midway
Cause:
This usually happens due to:
- Slow internet connection
- Background programs running
- Antivirus blocking the installer
Solution:
- Close all unnecessary programs
- Restart your computer and try again
- Temporarily disable antivirus or firewall (re-enable it after installation)
- Use a stable internet connection
Make sure you download Drake Software only from the official source.
-
Permission or Administrator Errors
Cause:
If you don’t have administrator rights, Windows may block the installation.
Solution:
- Right-click on the installer file
- Select “Run as Administrator”
- Ensure your user account has admin privileges
This is one of the most overlooked but easiest fixes.
-
Antivirus or Firewall Blocking Installation
Cause:
Security software may mistakenly identify Drake files as a threat.
Solution:
- Add Drake Software to antivirus exclusions
- Temporarily disable firewall during installation
- Allow Drake Software through Windows Defender
This issue is very common in office environments with strict security settings.
-
Corrupted or Incomplete Installation File
Cause:
A broken or incomplete download can lead to installation failure.
Solution:
- Delete the existing installer file
- Re-download the setup from the official Drake website
- Avoid using public or unstable networks
Never use third-party or pirated installers.
-
Network Installation Errors (Multi-User Setup)
Cause:
If you’re installing Drake Software on a network or server:
- Network permissions may be incorrect
- Shared folder settings may be misconfigured
Solution:
- Ensure shared folders have full read/write permissions
- Verify network connectivity
- Install Drake Software on the server first, then on workstations
Many firms avoid such issues by switching to Drake Hosting, where the software is already installed and managed on the cloud.
-
Windows Update or Missing Components Error
Cause:
Outdated Windows or missing system files can interfere with installation.
Solution:
- Run Windows Update
- Install pending updates
- Restart your system
- Install required redistributables (C++ or .NET)
Keeping your system updated helps avoid many installation problems.
-
Error Due to Previous Drake Installation
Cause:
Old or incomplete Drake installations can conflict with the new setup.
Solution:
- Uninstall previous versions completely
- Delete leftover Drake folders
- Clean temporary files
- Restart your system before reinstalling
This ensures a clean and smooth installation.
-
Disk Space Errors
Cause:
Insufficient hard drive space may prevent installation.
Solution:
- Free up disk space
- Move large files to external storage
- Install Drake Software on a drive with sufficient space
Always keep extra free space for updates and backups.
10. Installation Errors in Virtual or Remote Environments
Cause:
Installing Drake Software on remote desktops or virtual machines may cause errors due to:
- Limited permissions
- Server restrictions
Solution:
This is where Drake Hosting or UltraTax CS Hosting becomes highly beneficial. With cloud hosting:
- Software comes pre-installed
- No local installation issues
- Access from anywhere
- Professional server management
Hosting removes the headache of manual installations completely.
How Drake Hosting Helps Avoid Installation Errors
Drake Hosting allows tax professionals to access Drake Software through a secure cloud server instead of installing it on local machines. This eliminates most installation-related problems such as:
- Compatibility issues
- Network setup errors
- Permission problems
- Hardware limitations
With hosting, updates, security, and maintenance are handled by experts, allowing you to focus on tax work instead of IT issues.
Drake Software vs UltraTax CS Hosting
Similar to Drake Hosting, UltraTax CS Hosting offers cloud-based access to UltraTax CS software. Both hosting solutions provide:
- Zero installation hassles
- Automatic updates
- Secure data storage
- Remote accessibility
For firms that frequently face installation or technical issues, cloud hosting is a smarter and more reliable solution.
Drake Installation Errors
To avoid future problems, follow these simple tips:
- Always check system requirements
- Keep Windows and drivers updated
- Use antivirus exclusions wisely
- Avoid installing during peak system usage
- Consider cloud hosting for long-term stability
These steps can save time and reduce stress during tax season.
Final Thoughts
Drake Software installation errors can be frustrating, especially when deadlines are tight. However, most issues are caused by common factors like system compatibility, permissions, or security software—and they are easy to fix with the right steps.
For tax professionals who want a hassle-free experience, Drake Hosting and UltraTax CS Hosting offer a reliable alternative by eliminating installation and technical concerns altogether. Cloud hosting not only simplifies access but also improves productivity and data security.
Computer Electronic
AVG Internet Security: A Guide to Protecting Your Digital Life

In today’s digital world, protecting your devices from online threats is no longer optional—it’s essential. From phishing scams and ransomware to spyware and unsafe websites, cyber risks continue to grow in both number and sophistication. AVG Internet Security is one of the most trusted cybersecurity solutions designed to safeguard your computers, smartphones, and personal data. This article explains what AVG Internet Security offers, how to buy a new subscription, how to renew an existing one, and how support can help make the process smooth and stress-free.

What Is AVG Internet Security?
AVG Internet Security is a comprehensive antivirus and online protection suite developed to defend users against a wide range of digital threats. Unlike basic free antivirus tools, this premium solution provides advanced, real-time protection across multiple layers of your digital life.
Key features typically include:
- Real-time antivirus protection against viruses, malware, spyware, and ransomware
- Web and email protection to block malicious links and phishing attempts
- Firewall protection to monitor incoming and outgoing network traffic
- Ransomware defense to safeguard important files and folders
- Performance optimization tools that help keep your system running efficiently
Whether you use your device for work, online banking, shopping, or entertainment, AVG Internet Security helps ensure your data and privacy remain protected.
Why You Need an Active AVG Subscription
AVG Internet Security works on a subscription basis. While the software may remain installed on your device, many of its advanced features require an active license. An expired subscription can leave you vulnerable to the latest threats because:
- Virus definitions and security updates may stop
- Real-time protection may be limited or disabled
- New and emerging threats may not be detected
- Your financial and personal information might be in danger
That’s why buying a new subscription or renewing your existing one on time is critical.
How to Buy AVG Internet Security
Purchasing AVG Internet Security is a straightforward process, even for users who are not very tech-savvy. Here’s a step-by-step overview:
1. Choose the Right Plan
AVG typically offers several plans based on:
- Number of devices (1, 5, or 10 devices)
- Duration (1 year, 2 years, or more)
- Device types (Windows, Mac, Android)
Select a plan that fits your household or business needs.
2. Complete the Purchase
After choosing your plan:
- Enter your email address (this is where your license details are sent)
- Complete payment using a secure method such as credit/debit card or other available options
3. Install and Activate
Once payment is complete:
- Download the AVG Internet Security software
- Install it on your device
- Enter the activation code or sign in with your registered email to activate the subscription
- If you encounter any difficulties during installation or activation, professional support can guide you through the process step by step. Many users prefer speaking directly with a support representative at 1-833-800-3030 to ensure everything is set up correctly.
How to Renew AVG Internet Security Subscription
Renewing your AVG subscription before it expires ensures uninterrupted protection. The renewal process is usually even simpler than buying a new plan.
1. Check Your Expiration Date
You can check your subscription status by:
- Opening the AVG Internet Security dashboard
- Logging into your AVG account
- Reviewing email reminders sent before expiration
2. Renew Online
Most users renew directly through the software or account portal:
- Click on “Renew Now”
- Choose your renewal term
- Complete the payment
Your license is typically extended automatically without the need to reinstall the software.
3. Renew with Support Assistance
Sometimes users face issues such as:
- Renewal payment errors
- Subscription not updating after payment
- Confusion between multiple AVG products
- License not applying to all devices
In such cases, speaking with support can save time and frustration. A knowledgeable support agent can verify your subscription, fix activation problems, and make sure your devices are fully protected.
Common Issues During Buying or Renewal
Even though AVG Internet Security is user-friendly, some common challenges may arise:
- Wrong plan purchased: Buying a plan that doesn’t cover all devices
- Duplicate subscriptions: Accidentally purchasing multiple licenses
- Activation errors: Entering an incorrect license key
- Expired email access: Not receiving activation details due to email issues
Support services can help resolve these problems efficiently. For personalized guidance on buying, renewing, or fixing subscription-related concerns, users often reach out via phone support at 1-833-800-3030 for real-time assistance.
Benefits of Getting Support Help
While many users complete the process on their own, support assistance offers several advantages:
- Saves time by avoiding trial-and-error troubleshooting
- Ensures the correct plan is selected for your needs
- Helps transfer licenses to new or replacement devices
- Provides clarity on billing, renewal terms, and refunds
- Offers peace of mind knowing your security is properly configured
This is especially helpful for non-technical users, seniors, or small businesses managing multiple devices.
Tips to Manage Your AVG Subscription Better
To get the most out of AVG Internet Security:
- Enable auto-renewal to avoid lapses in protection
- Keep your registered email updated for renewal reminders
- Regularly check the AVG dashboard for alerts or updates
- Use the same account across devices to manage licenses easily
- Renew early to avoid last-minute issues
Staying proactive ensures continuous protection against evolving cyber threats.
Final Thoughts
AVG Internet Security is a powerful and reliable solution for safeguarding your digital life. Whether you are purchasing a new subscription or renewing an existing one, the process is designed to be simple and user-friendly. However, if you ever feel unsure or face technical difficulties, getting support can make a significant difference.
By keeping your subscription active and properly configured, you ensure that your devices, personal information, and online activities remain protected at all times. With the right plan and timely renewal, AVG Internet Security continues to act as a strong shield against the ever-changing landscape of cyber threats.
-
Business3 years ago
Cybersecurity Consulting Company SequelNet Provides Critical IT Support Services to Medical Billing Firm, Medical Optimum
-
Business3 years ago
Team Communication Software Transforms Operations at Finance Innovate
-
Business3 years ago
Project Management Tool Transforms Long Island Business
-
Business2 years ago
How Alleviate Poverty Utilized IPPBX’s All-in-One Solution to Transform Lives in New York City
-
health3 years ago
Breast Cancer: The Imperative Role of Mammograms in Screening and Early Detection
-
Sports3 years ago
Unstoppable Collaboration: D.C.’s Citi Open and Silicon Valley Classic Unite to Propel Women’s Tennis to New Heights
-
Art /Entertainment3 years ago
Embracing Renewal: Sizdabedar Celebrations Unite Iranians in New York’s Eisenhower Park
-
Finance3 years ago
The Benefits of Starting a Side Hustle for Financial Freedom






























