Technology Explained
Still Receiving Emails After Unsubscribing? Here’s What to Do
Still Receiving Emails After Unsubscribing?
Unsubscribing from emails should get you taken off the mailing list. But if you’re still getting some slip through, here’s what to do.
Have you ever unsubscribed from a company’s email list, only to receive another email from them the next day? If a sender has already annoyed you enough to hit the unsubscribe button, the last thing you want is to see their name pop up in your inbox almost instantly.
Why Am I Still Receiving Emails After Unsubscribing?
Unsubscribing should be the hassle-free way to stop receiving unwanted emails, but it doesn’t always do the trick. There are several reasons you might continue to receive emails from a company, even after unsubscribing:
- You’re signed up to multiple email lists: Many companies will try to sign you up for multiple email lists (marketing, news, customer service, etc.), which means you have to unsubscribe from all of them to stop receiving any emails from them.
- It takes time to update email lists: Hitting the unsubscribe button doesn’t instantly remove you from an email list. Companies have to update their lists, and this can take time, depending on the system they use and their inclination to act quickly.
- Technical issues can happen: While the chances are relatively slim, technical problems do happen. For example, the company could break something during an update or their email system might experience downtime, failing to unsubscribe anyone during such periods.
- The company needs to send certain emails: If you’re still buying from the company or using their products, they’ll need to send certain types of email–no matter how much you unsubscribe: transactional emails, T&Cs updates, pricing changes, etc.
- Some companies ignore unsubscribe requests: No, it’s not fair, but some companies simply don’t play by the rules.
While none of these reasons makes it any less annoying that you’re still receiving emails, they can help you take actionable steps to protect your inbox. Before we go any further, though, make sure you only unsubscribe from emails you recognize–never unsubscribe from suspected spam emails.
How to Stop Unsubscribed Companies Sending You More Emails
Now you know the main reasons you can still receive emails from a company after unsubscribing, you can take steps to address them.
1. Check Your Email Subscription Settings
The first thing to do if you’re still receiving emails after unsubscribing is to check whether you’re signed up to multiple email lists. If you have an account with the company, sign in to your account and check your email settings or preferences in the back end of the system.
For example, if you’re receiving a bunch of emails from Instagram, log into your account and click Settings and privacy > Email notifications to change your email preferences.
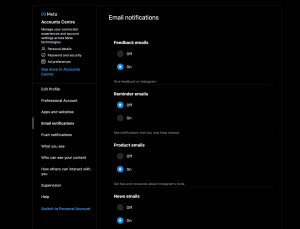
Image by https://www.makeuseof.com/
If you don’t have an account with the company in question, go back to one of the emails they’ve sent you and cycle through their unsubscribing process again. Make sure you click the unsubscribe link in their email, not the one in your email client.
As you repeat the unsubscribe cycle, look out for anything that shows you’re signed up for multiple lists: checkboxes, toggles, etc. Read every step of the unsubscribe process carefully for anything that suggests you’re signed up for other lists or will continue to receive certain types of email.
For example, if you’re still using a company’s software product, you’ll continue to receive emails for updates on pricing, purchase confirmations, etc.
Also, keep an eye out for links to the company’s privacy policy or anything related to email practices that could explain why you’re still receiving emails. You might even see some small print explaining why you’ll still receive occasional emails or that it takes up to 24 to 48 hours for your email address to be removed from their lists.
Hopefully, repeating the unsubscribe process will provide the answers you need. If it doesn’t, head to the company’s website and take a look at their privacy policy on email communication.
2. Wait a Day or Two for Settings to Change
Most companies use email marketing systems to automate communications. These software tools automatically send emails to recipients and handle a range of other tasks, including unsubscribes. Some of these systems will update email lists as soon as you hit the unsubscribe button, but many don’t.
It could take anywhere between 24 and 48 hours for an email system to update its contact lists. This means you’ll continue to receive emails from the sender until their system has run the next update cycle.
In an ideal world, companies will inform you of this during the unsubscribe process, but many don’t. In fairness, a lot of companies may not realize there’s a delay or even pay much attention to subscription requests. Either way, it’s always worth waiting 24 to 48 hours after unsubscribing before you take any further action.
3. Report As Spam If You’re Still Receiving Email
If you’ve waited 24 to 48 hours after unsubscribing, and you’ve done everything possible to make sure you’re not signed up to other email lists, it’s time to take stronger action. By this point, any company that’s still sending you unwanted emails is spamming you, so you should start marking any further emails as spam.
If you’re using Gmail, you can do this by selecting the checkbox next to any spam emails, and then click the Report spam button.
This won’t stop further emails coming through, but every spam report is another black mark on their email sender reputation with ISPs. This means more of their emails will head straight to people’s spam folders and their email marketing efforts will suffer. So, even though it’s annoying to keep dealing with these emails, every spam report you submit is making a difference.
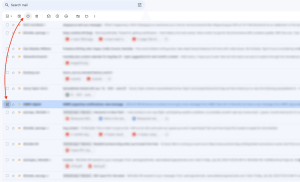
Image by https://www.makeuseof.com/
4. Block the Sender to Stop Receiving Email
If you reach a point where you simply want to stop receiving further emails from a particular sender, you can block them completely. The easiest way to do this in Gmail is to click the three-dot icon at the top of an email and select Block [sender name] from the dropdown menu.
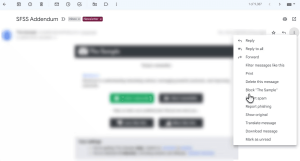
Image by https://www.makeuseof.com/
Keep in mind that this only blocks the exact email address used to send the email in question. So, if the company uses a bunch of email addresses for different types of emails, you won’t block them all.
A more robust method is to create a custom email filter. You can do this in Gmail by clicking the gear icon (Settings) > See all settings > Filters and blocked addresses.
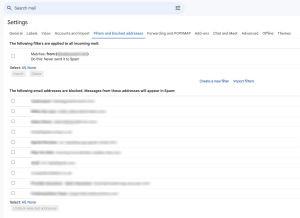
Image by https://www.makeuseof.com/
Next, click on the Create a new filter link and this will bring up the following box:
This time, you want to type in the domain name of the email sender into the From field, which is normally the text following the @ symbol. For example, emailprefix@domain.com. This will block all emails from the domain, so it’ll block anything sent from other people or departments at the same company.
Unfortunately, this still won’t protect you from companies that keep switching domain names to get past spam filters. However, you can type the company name into the Includes the words field and this will help filter out any emails that include the company’s name (which should be all of them).
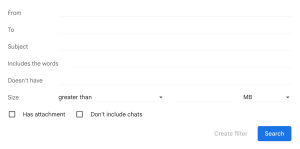
Image by https://www.makeuseof.com/
Again, this isn’t foolproof, but it should deal with the vast majority of emails from legitimate companies.
5. Raise a Complaint With the Company
Hopefully, the steps we’ve covered will help you deal with any unwanted emails that you’ve tried to unsubscribe from. That being said, you might want to contact the company in question to make them aware of the issue.
Broadly speaking, companies are legally obliged to respect any subscription requests you make, and it might help to remind or make them aware of this. Point them in the direction of the CAN-SPAM Act to make them aware you also know they’re legally obliged to respect your wishes.
As mentioned earlier, it’s possible to continue receiving emails due to a system error or legitimate mistake. Raising the issue with a company could help them identify an unknown problem and resolve it.
They might even inform you that a temporary (and fixed) issue kept you on an email marketing list. In this case, manually removing you from an email list on their end of the system could resolve the problem for you.
Sometimes, Unsubscribing Isn’t Enough
As annoying as it is, unsubscribing from an email list isn’t always enough to stop receiving emails from a sender. Sometimes, they intentionally make it harder than it should be to remove your email address from all of their marketing lists. In other cases, they might not understand the rights and wrongs of email marketing–or even care about them.
Either way, it always helps to know the tools Gmail and other email clients give you to take control over your inbox and the emails reaching it.
Key Points Summary Table:
| Reasons for Still Receiving Emails | Steps to Take |
|---|---|
| Signed up to multiple email lists | Check email subscription settings |
| Time required to update email lists | Wait for settings to change |
| Technical issues | Report emails as spam |
| Necessary emails | Block the sender |
| Non-compliance by companies | Raise a complaint with the company |
Digital Development
Boldify for Facebook: Quick Bold Text in Seconds

Scroll through Facebook for just five minutes and you’ll notice something: most posts look exactly the same. Plain text blends into the feed, making it easy for users to scroll past without noticing important messages. In a crowded social media environment, visual formatting plays a major role in grabbing attention and increasing engagement. This is where Boldify, a powerful bold text generator, makes a difference. Instead of struggling with plain, unformatted posts, Boldify allows you to create eye-catching Facebook bold text instantly. In this article, you’ll learn why bold text matters, how Boldify works, and how you can use it to stand out on Facebook within seconds.
Why Bold Text Matters on Facebook (User Engagement Psychology)
Facebook is a fast-moving platform. Users scroll quickly, often stopping only when something visually stands out. Bold text works because it creates contrast. When certain words appear heavier or more prominent, the brain processes them faster.
Here’s why bold text improves engagement:
- It grabs attention in crowded feeds.
- It improves readability and scan ability.
- It highlights key messages instantly.
Bold formatting is especially powerful in:
- Facebook posts
- Comments
- Bios
- Facebook groups
If you’re building a brand or growing a personal profile, bold text strengthens your identity. It emphasizes important announcements, promotions, or calls to action, making your message harder to ignore.
The Challenge: Facebook Doesn’t Offer Built-In Bold Formatting
One of the biggest frustrations for users is that Facebook does not provide built-in bold formatting for regular posts. Unlike word processors, you cannot simply select text and click “Bold.”
That’s why many people search for:
- how to bold text on Facebook
- Facebook bold text generator
- bold letters for Facebook
Without a proper tool, users are left copying complicated codes or trying ineffective formatting tricks. This creates a clear need for a reliable and easy-to-use bold font generator.
What Is Boldify?
Boldify is an online bold text generator designed to help users create stylish bold letters instantly. Instead of modifying Facebook’s formatting, Boldify uses Unicode-based bold fonts that are fully compatible with social media platforms.
Here’s what makes Boldify simple and powerful:
- No installation required
- Works directly in your browser
- Free and instant access
- Compatible with Facebook, Instagram, Twitter, and WhatsApp
Because it uses special Unicode characters, the bold text appears naturally once pasted into Facebook posts, comments, bios, or Messenger chats. This makes Boldify a practical and beginner-friendly solution for anyone looking to create bold text online.
How Boldify Helps You Create Bold Facebook Text in Seconds
Using Boldify is straightforward and requires no technical knowledge. Here’s a simple step-by-step guide:
Step 1: Enter Your Text
Open Boldify and type your message into the input box. This could be a status update, promotional message, announcement, or bio line.
Example:
New Blog Post Live
Limited Time Offer
Join Our Community Today
Step 2: Automatic Bold Conversion
As soon as you enter your text, Boldify automatically converts it into multiple bold font styles. Within seconds, you’ll see several variations generated instantly.
Step 3: Copy and Paste to Facebook
Choose the bold style you like, click the copy button, and paste it directly into:
- Facebook posts
- Comments
- Bios
- Messenger chats
That’s it. In just a few seconds, your plain text becomes visually powerful Facebook bold text.
Key Features That Make Boldify Stand Out
There are many tools online, but Boldify offers specific advantages that make it reliable and user-friendly.
1. One-Click Copy Feature
No need to manually select text. Just click and copy instantly.
2. Multiple Bold Style Variations
Get access to different bold styles to match your tone and branding.
3. Mobile-Friendly Interface
Boldify works smoothly on smartphones, tablets, and desktops.
4. No Login Required
You don’t need to create an account. Just open and start using.
5. Fast Performance
Text conversion happens instantly without delays.
6. Clean and Simple Design
The interface is distraction-free, making it easy for beginners to use.
These features make Boldify more than just a basic bold letters generator—it becomes a practical social media enhancement tool.
Practical Ways to Use Bold Text on Facebook
Now that you know how to generate bold text, let’s explore practical ways to use it effectively.
Highlight Important Announcements
SALE TODAY ONLY
Registration Closes Tonight
Bold formatting ensures these messages get noticed quickly.
Strengthen Call-to-Actions
Instead of writing:
Join us now
Write:
JOIN US NOW
It creates urgency and clarity.
Emphasize Keywords in Posts
Highlight important parts of your message to guide the reader’s attention.
Improve Facebook Bios
Use bold text to make your profession, tagline, or brand name stand out.
Stand Out in Facebook Groups
When commenting in large groups, bold text increases visibility and improves response rates.
SEO & Branding Benefits of Using Bold Text
While bold text doesn’t directly change Facebook’s algorithm, it improves how users interact with your content.
Here’s how it benefits branding and visibility:
- Improves readability
- Encourages longer post engagement
- Strengthens personal or business branding
- Creates structured content hierarchy
- Makes posts look professional
When your content looks organized and visually appealing, users are more likely to stop scrolling and engage.
Tips for Using Bold Text Effectively
Bold text is powerful—but only when used strategically.
- Don’t overuse bold formatting.
- Highlight only key phrases or calls-to-action.
- Combine bold text with emojis carefully.
- Maintain readability and spacing.
Too much bold text can reduce its impact. The goal is to enhance clarity, not overwhelm the reader.
Conclusion
Standing out on Facebook is no longer optional—it’s necessary. Since Facebook doesn’t offer built-in bold formatting for posts, tools like Boldify provide a fast and effective solution.
Consumer Services
Right Software Development Partner in India for Your 2026 Startup

Starting a startup in 2026 feels exciting, but also confusing. You have an idea, maybe even a small team, yet one big question always appears first: who will build your product? Most founders are not programmers. They need reliable custom software development services to turn their idea into a real app, website, or platform.
India has become one of the most trusted places for startups to build software. Why? Because you get skilled engineers, global experience, and affordable pricing in one place. From fintech apps in Dubai to healthcare software used in Europe and the US, many young companies rely on Indian development partners.
In this article, we will understand how startups should choose a development partner and explore ten reliable Indian companies that provide custom software development services suitable for early-stage businesses.
How to Choose the Right Development Partner
Before hiring any company, a founder should understand what they actually need. A startup does not require a huge corporate vendor. It needs guidance and flexibility.
Here is a simple decision checklist-
- Do they build MVPs for startups or only big enterprise projects?
- Do they help with product planning or just coding?
- Do they offer cloud setup on AWS or Google Cloud?
- Can they explain technical ideas in simple English?
- Do they support your product after launch?
A good provider of custom software development services acts like a technical cofounder. They tell you what features to delay, how to save cost, and how to launch faster. For example, many fintech startups first build only login, wallet, and payment features. They add analytics later. This approach saves both time and money.

Top 10 Software Development Companies in India for Startups
Below are ten reliable companies suitable for startup founders. Each offers custom software development and flexible engagement.
1. AppSquadz
AppSquadz focuses on startup MVP development and scalable digital products. They provide mobile app development, SaaS platforms, cloud solutions, and custom software development services based on business needs. Many education and healthcare startups choose them for UI/UX guidance and post-launch support.
2. Konstant Infosolutions
Known for mobile applications, especially ecommerce and booking apps. Startups launching marketplace platforms often use their affordable software development services. They have experience with payment integrations and real time chat systems.
3. TatvaSoft
This custom application development company works with startups building web platforms and dashboards. They are strong in NET and React technologies. Several SaaS products serving the logistics industry were built by their teams.
4. PixelCrayons
Popular among international founders from the UK and Dubai. They offer dedicated developer hiring. Many early stage companies choose them when they need quick product development without hiring an internal team.
5. OpenXcell
A good option for AI and blockchain based startups. If your idea includes automation, chatbots, or analytics tools, they provide custom software development services with consulting support.
6. Radixweb
This firm helps startups scale after launch. Suppose your app suddenly gets 50000 users. They help migrate it to AWS and optimize performance. That makes them useful for growing SaaS businesses.
7. MindInventory
Strong in UI and UX design. Many founders do not realize how important user experience is. This company focuses on making apps easy to use, which improves customer retention.
8. Hidden Brains
A long established custom software development provider that works with fintech and healthcare software projects. They also build ERP systems for startups entering manufacturing.
9. Net Solutions
Useful for ecommerce startups. They have experience with Shopify and headless commerce platforms. Many D2C brands launching online stores work with them.
10. SPEC INDIA
They focus on data driven platforms and analytics dashboards. Startups handling large customer data sets or reporting tools benefit from their expertise.
Why Startups Prefer India in 2026
A few years ago startups hired freelancers. Today they prefer a custom application development company. The reason is simple: startups now build complex products. Think about apps using AI, payment gateways, cloud storage, and real time chat. One freelancer cannot manage everything. India offers three big advantages:
First, cost. A startup in the United States may spend $120000 to build an MVP. In India the same project can often be done for $15000 to $30000 using affordable software development services.
Second, cloud knowledge. Many Indian teams work daily with AWS and Google Cloud. They know how to make scalable systems. This means your app will not crash when 100 users become 10000 users.
Third, startup understanding. Indian companies now follow agile methods. They release small updates weekly instead of waiting six months.
You might ask: Is cheaper always lower quality? No. Many Indian developers build SaaS products used worldwide. Cost is lower mainly because operating expenses are lower, not because skill is lower.
Conclusion
Choosing the right development partner in 2026 is not just a technical decision — it’s a strategic one. For early-stage startups, the company you hire will directly influence your product quality, launch speed, scalability, and even investor confidence.
India continues to be a preferred destination because it offers a strong balance of cost efficiency, technical expertise, and startup-focused execution. However, the real advantage does not come from geography alone , it comes from selecting a partner who understands MVP thinking, agile development, cloud scalability, and long-term product growth.
FAQs
1. Why do startups prefer hiring Indian software development companies?
Startups prefer Indian companies because they offer a strong balance of cost efficiency, technical expertise, and scalable development practices. Many firms in India have global experience working with startups from the US, Europe, and the Middle East, making them comfortable with international standards and agile workflows.
2. How much does it cost to build an MVP in India?
The cost of building a Minimum Viable Product (MVP) in India typically ranges between $15,000 and $30,000, depending on complexity, features, and technology stack. More advanced platforms involving AI, fintech integrations, or complex dashboards may cost more.
3. How long does it take to develop a startup MVP?
Most startup MVPs take 8 to 16 weeks to develop. Simple apps with limited features can launch faster, while SaaS platforms or fintech products may require additional time for backend development, security setup, and testing.
4. Should startups hire freelancers or a development company?
Freelancers may work for very small projects, but modern startup products often require backend development, UI/UX design, cloud setup, testing, and ongoing support. A development company provides a structured team, project management, and long-term maintenance — reducing risk for early-stage founders.
5. What should startups look for before signing a development contract?
Before signing, startups should check:
- Portfolio of similar startup projects
- Clear pricing structure
- Post-launch support policy
- Ownership of source code
- Experience with cloud platforms like Amazon Web Services and Google Cloud
Digital Development
Vhsgjqm: Understanding Abstract Identifiers in the Digital Age
-
Business3 years ago
Cybersecurity Consulting Company SequelNet Provides Critical IT Support Services to Medical Billing Firm, Medical Optimum
-
Business3 years ago
Team Communication Software Transforms Operations at Finance Innovate
-
Business3 years ago
Project Management Tool Transforms Long Island Business
-
Business3 years ago
How Alleviate Poverty Utilized IPPBX’s All-in-One Solution to Transform Lives in New York City
-
health3 years ago
Breast Cancer: The Imperative Role of Mammograms in Screening and Early Detection
-
Sports3 years ago
Unstoppable Collaboration: D.C.’s Citi Open and Silicon Valley Classic Unite to Propel Women’s Tennis to New Heights
-
Art /Entertainment3 years ago
Embracing Renewal: Sizdabedar Celebrations Unite Iranians in New York’s Eisenhower Park
-
Finance3 years ago
The Benefits of Starting a Side Hustle for Financial Freedom

































